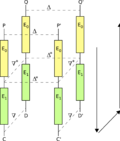
cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in...
9 KB (864 words) - 04:16, 17 October 2023
Captain Boomerang is the name of two supervillains appearing in American comic books published by DC Comics, who respectively serve as enemies to both...
46 KB (6,211 words) - 11:33, 30 July 2024
montage. The sound effects suite that concludes the disc has two cues, "Boomerang Attack" and "Gyro Flight", that do not appear elsewhere on the album (the...
13 KB (958 words) - 17:47, 13 April 2024
collisions in SHA-0 in 239 operations. Another attack in 2008 applying the boomerang attack brought the complexity of finding collisions down to 233.6, which was...
51 KB (5,762 words) - 21:53, 22 July 2024
Cryptanalysis (redirect from Cryptanalytic attack)
field of information security remain quite active. Boomerang attack Brute-force attack Davies' attack Differential cryptanalysis Harvest now, decrypt later...
44 KB (5,202 words) - 13:26, 19 August 2024
The CAC Boomerang is a fighter aircraft designed and manufactured in Australia by the Commonwealth Aircraft Corporation between 1942 and 1945. Approved...
43 KB (5,067 words) - 06:30, 17 April 2024
COCONUT98's security, in 1999 David Wagner developed the boomerang attack against it. This attack, however, requires both chosen plaintexts and adaptive...
5 KB (435 words) - 15:07, 29 October 2023
Block cipher (section Brute-force attacks)
square and integral attacks, slide attacks, boomerang attacks, the XSL attack, impossible differential cryptanalysis, and algebraic attacks. For a new block...
50 KB (6,475 words) - 03:59, 22 August 2024
complexity are required merely to distinguish the cipher from random. A boomerang attack (Wagner, 1999) can be used in an adaptive chosen plaintext / chosen...
9 KB (839 words) - 12:48, 9 June 2024
Differential cryptanalysis (redirect from Differential attack)
Truncated differential cryptanalysis Impossible differential cryptanalysis Boomerang attack Cryptography Integral cryptanalysis Linear cryptanalysis Differential...
13 KB (1,688 words) - 22:44, 29 October 2023
"Mudge"). 1999 Invention of the slide attack, a new form of cryptanalysis (with Alex Biryukov); also the boomerang attack and mod n cryptanalysis (the latter...
6 KB (439 words) - 09:24, 26 July 2024
round 3 of the NIST hash function competition. In 2009, a related key boomerang attack against a reduced round Threefish version was published. For the 32-round...
9 KB (1,332 words) - 23:43, 26 May 2024
of 32 rounds of Serpent and an amplified boomerang attack against 9 of 32 rounds in Serpent. A 2001 attack by Eli Biham, Orr Dunkelman and Nathan Keller...
16 KB (1,912 words) - 12:54, 8 June 2024
Seokhie Hong; Sangjin Lee; Seokwon Jung (December 2002). Amplified Boomerang Attack against Reduced-Round SHACAL. ASIACRYPT 2002. Queenstown, New Zealand:...
9 KB (903 words) - 07:08, 27 April 2022
Boomerang is a 2019 Indian Tamil-language action thriller film written, produced, and directed by R. Kannan. The film stars Atharvaa in a dual role, alongside...
15 KB (1,633 words) - 04:46, 12 July 2024
coincidence Kasiski examination Symmetric algorithms Boomerang attack Brute force attack Davies' attack; Differential cryptanalysis Impossible differential...
20 KB (1,890 words) - 03:11, 18 August 2024
scenarios; it presents a 224 time complexity attack to recover the S-box in a chosen-key scenario, a 248 boomerang attack to recover the key with a known S-box...
7 KB (675 words) - 15:07, 29 October 2023
transforms into Sailor Mars. After Usagi launches one final Moon Tiara Boomerang attack to trap Jadeite, Rei overpowers Jadeite's ice abilities with her own...
93 KB (2,026 words) - 15:41, 11 August 2024
cryptanalysis" presents boomerang attack and known-plaintext attack on reduced round versions up to 6 rounds. In 2015 few additional attacks have been published...
13 KB (1,376 words) - 13:37, 2 May 2024
a related-key rectangle (boomerang) attack on KASUMI that can break all 8 rounds faster than exhaustive search. The attack requires 254.6 chosen plaintexts...
17 KB (2,555 words) - 01:42, 17 October 2023
grab them. It can also be used as the Stinger Boomerang (スティンガーブーメラン, Sutingā Būmeran). Its powerful attack is the Raging Slash (レイジングスラッシュ, Reijingu Surasshu)...
64 KB (9,896 words) - 08:21, 6 August 2024
see comparison of cryptographic hash functions. No attack successfully demonstrated — attack only breaks a reduced version of the hash or requires...
17 KB (1,055 words) - 12:18, 2 March 2023
separate into swords and shields to be used in their Combination Cross Boomerang attack. Rolling Vulcan (ローリングバルカン, Rōringu Barukan): The finishing cannon...
30 KB (4,282 words) - 05:29, 24 July 2024
List of Marvel Comics characters: B (redirect from Boomerang (character))
battle the Avengers Resistance when the group attacks. He is knocked out by Ultra Girl and Batwing. Boomerang appeared as a hired goon of the Rose and came...
212 KB (26,062 words) - 17:40, 20 August 2024
Operation Boomerang was a partially successful air raid by the United States Army Air Forces' (USAAF) XX Bomber Command against oil refining facilities...
25 KB (3,176 words) - 04:49, 28 May 2024
Zurich, known for several attacks on cryptosystems. David Wagner, US, UC Berkeley, co-discoverer of the slide and boomerang attacks. Xiaoyun Wang, the People's...
21 KB (2,421 words) - 18:12, 17 August 2024
In cryptography, a timing attack is a side-channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute...
12 KB (1,524 words) - 20:12, 19 July 2024
Be Cool, Scooby-Doo! (category Boomerang (TV network) original programming)
announced the show to air on Boomerang and the news was later confirmed on June 29, 2015. It was originally scheduled to air on Boomerang, but the series instead...
68 KB (1,882 words) - 06:00, 5 August 2024
Koenigsegg Jesko (redirect from Koenigsegg Jesko Attack)
Koenigsegg. There are two variations of the car, the "Absolut" and the "Attack". The engine is a development of the 5.1 L (5,065 cc) twin-turbocharged...
26 KB (2,204 words) - 01:25, 17 August 2024
brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically...
21 KB (2,250 words) - 15:26, 19 July 2024