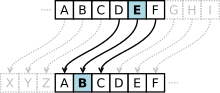
Link encryption is an approach to communications security that encrypts and decrypts all network traffic at each network routing point (e.g. network switch...
2 KB (205 words) - 12:57, 24 October 2023
In cryptography, encryption is the process of transforming (more specifically, encoding) information in a way that, ideally, only authorized parties can...
35 KB (3,687 words) - 11:44, 15 November 2024
distribution center (KDC) Key management Key stream KSD-64 Link encryption MISTY1 Multiplex link encryption Net control station (NCS) Null cipher One-time pad...
5 KB (446 words) - 21:24, 28 August 2024
Symmetric-key algorithm (redirect from Symmetric encryption)
algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical...
15 KB (1,544 words) - 20:48, 3 November 2024
National Security Agency took over responsibility for all US government encryption systems when it was formed in 1952. The technical details of most NSA-approved...
26 KB (3,313 words) - 15:30, 29 October 2024
Homomorphic encryption is a form of encryption that allows computations to be performed on encrypted data without first having to decrypt it. The resulting...
40 KB (4,409 words) - 00:38, 14 November 2024
End-to-end encryption (E2EE) is a private communication system in which only communicating users can participate. As such, no one else, including the communication...
29 KB (3,041 words) - 17:21, 31 July 2024
peer-to-peer networking and an official GNU package. The framework offers link encryption, peer discovery, resource allocation, communication over many transports...
20 KB (2,142 words) - 10:59, 11 March 2024
Disk encryption is a special case of data at rest protection when the storage medium is a sector-addressable device (e.g., a hard disk). This article presents...
30 KB (3,771 words) - 08:32, 29 October 2024
The Data Encryption Standard (DES /ˌdiːˌiːˈɛs, dɛz/) is a symmetric-key algorithm for the encryption of digital data. Although its short key length of...
59 KB (6,543 words) - 16:59, 10 November 2024
In cryptography and steganography, plausibly deniable encryption describes encryption techniques where the existence of an encrypted file or message is...
24 KB (2,832 words) - 16:35, 5 September 2024
Disk encryption is a technology which protects information by converting it into code that cannot be deciphered easily by unauthorized people or processes...
17 KB (2,194 words) - 03:24, 4 September 2024
Advanced Encryption Standard (AES), also known by its original name Rijndael (Dutch pronunciation: [ˈrɛindaːl]), is a specification for the encryption of electronic...
50 KB (5,614 words) - 16:05, 16 November 2024
This is a technical feature comparison of different disk encryption software. Hidden containers: Whether hidden containers (an encrypted container (A)...
70 KB (2,834 words) - 08:37, 8 October 2024
NSA cryptography (redirect from NSA encryption algorithms)
The vast majority of the National Security Agency's work on encryption is classified, but from time to time NSA participates in standards processes or...
9 KB (469 words) - 02:34, 21 October 2023
Proxy re-encryption (PRE) schemes are cryptosystems which allow third parties (proxies) to alter a ciphertext which has been encrypted for one party, so...
6 KB (897 words) - 17:26, 4 September 2024
Caesar cipher (redirect from Caesar encryption)
Caesar's code, or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in...
19 KB (2,058 words) - 14:38, 20 October 2024
Transport Layer Security (redirect from Transport layer encryption)
authenticated encryption ciphers, used mainly for Galois/Counter Mode (GCM) and CCM mode of Advanced Encryption Standard (AES) encryption. TLS Extensions...
179 KB (17,618 words) - 14:07, 15 November 2024
SAFER (redirect from Secure And Fast Encryption Routine)
In cryptography, SAFER (Secure And Fast Encryption Routine) is the name of a family of block ciphers designed primarily by James Massey (one of the designers...
7 KB (838 words) - 06:46, 27 April 2022
In cryptography, the Tiny Encryption Algorithm (TEA) is a block cipher notable for its simplicity of description and implementation, typically a few lines...
13 KB (1,189 words) - 18:51, 14 April 2024
HTTPS (redirect from HTTPS encryption)
(HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It uses encryption for secure communication over a computer network, and is widely used on...
40 KB (4,186 words) - 10:09, 17 November 2024
Strong cryptography (redirect from Strong encryption)
dealing with export control of encryption, considered as of 1999[update] any implementation of the symmetric encryption algorithm with the key length above...
22 KB (2,846 words) - 07:57, 27 March 2024
Identity-based encryption (IBE), is an important primitive of identity-based cryptography. As such it is a type of public-key encryption in which the public...
16 KB (1,944 words) - 12:51, 17 February 2024
Cold boot attack (redirect from Full memory encryption)
target machine. Typically, cold boot attacks are used for retrieving encryption keys from a running operating system for malicious or criminal investigative...
38 KB (4,246 words) - 11:43, 3 November 2024
Glossary of cryptographic keys (redirect from Key Encryption Key)
protected by encryption or other means so that it can be distributed without fear of its being stolen. Also called BLACK key. content-encryption key (CEK)...
9 KB (1,187 words) - 20:52, 6 August 2024
Key size (redirect from 128 bit encryption)
therefore, be large enough that a brute-force attack (possible against any encryption algorithm) is infeasible – i.e. would take too long and/or would take...
29 KB (3,213 words) - 18:15, 18 September 2024
Cryptographic protocol (redirect from Encryption protocol)
aspects: Key agreement or establishment Entity authentication Symmetric encryption and message authentication material construction Secured application-level...
9 KB (1,009 words) - 10:38, 7 October 2024
Blowfish (cipher) (redirect from Blowfish encryption algorithm)
Schneier and included in many cipher suites and encryption products. Blowfish provides a good encryption rate in software, and no effective cryptanalysis...
18 KB (2,000 words) - 06:17, 22 September 2024
or not traffic is being transmitted. This is also called masking or link encryption. Traffic-flow security is one aspect of communications security. The...
21 KB (2,397 words) - 22:53, 13 September 2024
Opportunistic encryption (OE) refers to any system that, when connecting to another system, attempts to encrypt communications channels, otherwise falling...
11 KB (1,279 words) - 19:41, 18 October 2024