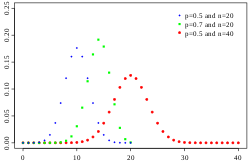
In cryptanalysis, the piling-up lemma is a principle used in linear cryptanalysis to construct linear approximations to the action of block ciphers. It...
8 KB (1,445 words) - 06:28, 20 June 2024
mixing, to arrive at linear approximations for the entire cipher. The piling-up lemma is a useful tool for this combination step. There are also techniques...
6 KB (812 words) - 13:20, 1 November 2023
with individual probabilities x. A special case of this fact is the piling-up lemma for parity functions. The polynomial form of a Boolean function can...
23 KB (2,887 words) - 21:32, 19 June 2025
measure, an example of a multifractal measure. Statistical mechanics Piling-up lemma, the resulting probability when XOR-ing independent Boolean variables...
53 KB (7,554 words) - 03:55, 26 May 2025
with titles containing piling All pages with titles beginning with piling Piling-up lemma Pressure piling, piling up of pressure Pile (disambiguation) Pilling...
717 bytes (135 words) - 08:02, 25 January 2025
lemma Isolation lemma Switching lemma Forking lemma Leftover hash lemma Piling-up lemma (linear cryptanalysis) Yao's XOR lemma Interchange lemma Newman's...
8 KB (525 words) - 21:03, 22 April 2025
exist. The simplest is to add null bytes to the plaintext to bring its length up to a multiple of the block size, but care must be taken that the original...
52 KB (5,828 words) - 12:52, 13 June 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
10 KB (1,040 words) - 10:14, 4 January 2025
the success probability in observation 1 of this paper matches that of lemma 2 from the INDOCRYPT 2004 analysis (setting w = 128 and l = n × 128). Saarinen...
23 KB (3,051 words) - 16:00, 1 July 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
10 KB (1,316 words) - 19:41, 2 February 2025
that changes as the cipher operates. That internal state is initially set up using the secret key material. RC4 is a widely used stream cipher. Block ciphers...
100 KB (11,007 words) - 01:11, 20 June 2025
bitwise XOR. On systems with 32-bit or larger words, it is possible to speed up execution of this cipher by combining the SubBytes and ShiftRows steps with...
50 KB (5,679 words) - 11:17, 28 June 2025
function, a continuous equivalent Parity bit, the output of the function Piling-up lemma, a statistical property for independent inputs Multiway switching,...
7 KB (1,050 words) - 02:51, 12 June 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
17 KB (2,269 words) - 14:13, 13 January 2024
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
13 KB (1,616 words) - 12:26, 4 June 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
6 KB (723 words) - 23:05, 27 March 2024
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
3 KB (224 words) - 16:45, 4 November 2024
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
7 KB (842 words) - 16:23, 27 May 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
9 KB (864 words) - 04:16, 17 October 2023
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
4 KB (398 words) - 12:58, 8 January 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
8 KB (934 words) - 10:33, 6 January 2025
the binary expansions of both e and the golden ratio as sources of "nothing up my sleeve numbers". The tantalising simplicity of the algorithm together with...
12 KB (1,465 words) - 18:48, 18 February 2025
variables then their parity (XOR) is a Bernoulli variable described by the piling-up lemma. Approximate or limit relationship means either that the combination...
21 KB (2,382 words) - 20:22, 5 May 2025
components as if they were a solid component (usually they are in fact look-up tables or S-boxes). Observing the desired output difference (between two chosen...
13 KB (1,677 words) - 11:30, 9 March 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
15 KB (1,834 words) - 05:42, 19 February 2025
and one for decrypting, all the machines can be identical and can be set up (keyed) the same way. Examples of reciprocal ciphers include: Atbash Beaufort...
15 KB (1,540 words) - 21:14, 19 June 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
6 KB (749 words) - 15:35, 22 November 2023
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
5 KB (568 words) - 14:12, 24 May 2025
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
14 KB (1,797 words) - 08:53, 7 September 2024
(EFF DES cracker) MITM Biclique attack 3-subset MITM attack Linear (Piling-up lemma) Differential Impossible Truncated Higher-order Differential-linear...
5 KB (623 words) - 03:12, 31 December 2023