to the reported security vulnerabilities with an official statement. AMD originally acknowledged vulnerability to one of the Spectre variants (GPZ variant...
82 KB (6,994 words) - 18:28, 10 February 2025
Meltdown also discovered Spectre. The security vulnerability was called Meltdown because "the vulnerability basically melts security boundaries which are...
87 KB (8,241 words) - 14:35, 26 December 2024
Speculative Store Bypass (redirect from SSB (security vulnerability))
hardware security vulnerability and its exploitation that takes advantage of speculative execution in a similar way to the Meltdown and Spectre security vulnerabilities...
13 KB (869 words) - 01:53, 18 November 2024
Foreshadow (redirect from Foreshadow-NG (security vulnerability))
is similar to the Spectre security vulnerabilities discovered earlier to affect Intel and AMD chips, and the Meltdown vulnerability that also affected...
22 KB (1,943 words) - 13:13, 19 November 2024
the Spectre security vulnerability, and expects to release the newly redesigned processors later in 2018. On May 3, 2018, eight additional Spectre-class...
68 KB (4,792 words) - 23:16, 3 February 2025
SWAPGS, also known as Spectre variant 1, is a computer security vulnerability that utilizes the branch prediction used in modern microprocessors. Most...
6 KB (581 words) - 03:53, 6 February 2025
CVE-2019-0162. Transient execution CPU vulnerability Hardware security bug Tung, Liam. "All Intel chips open to new Spoiler non-Spectre attack: Don't expect a quick...
3 KB (195 words) - 09:13, 15 August 2024
US The Spectre (Antarctica), a rock spire in the Queen Maud Mountains HP Spectre, a Hewlett-Packard computer Spectre (security vulnerability), a computer...
6 KB (771 words) - 01:13, 14 February 2025
aforementioned Ryzen 9 3950X. Zen 2 includes hardware mitigations to the Spectre security vulnerability. Zen 2-based EPYC server CPUs use a design in which multiple...
22 KB (3,194 words) - 06:32, 23 January 2025
believe the vulnerability posed a serious threat to users because it requires specific conditions to be exploited. Pacman is similar to Spectre, abusing...
13 KB (1,390 words) - 09:13, 15 August 2024
In computer security, coordinated vulnerability disclosure (CVD, sometimes known as responsible disclosure) is a vulnerability disclosure model in which...
12 KB (1,019 words) - 22:06, 5 February 2025
Downfall, known as Gather Data Sampling (GDS) by Intel, is a computer security vulnerability found in 6th through 11th generations of consumer and 1st through...
8 KB (569 words) - 09:12, 15 August 2024
Intel Management Engine (redirect from Converged Security and Manageability Engine)
vPro Meltdown (security vulnerability) Microsoft Pluton Next-Generation Secure Computing Base Samsung Knox Spectre (security vulnerability) Trusted Computing...
47 KB (4,501 words) - 20:24, 25 December 2024
SPECTRE ("Special Executive for Counter-intelligence, Terrorism, Revenge and Extortion") is a fictional organisation featured in the James Bond novels...
53 KB (6,846 words) - 15:46, 11 February 2025
leading to a security vulnerability. Hardware security Security bug Computer security Threat (computer) Bruce Schneier (January 5, 2018). "Spectre and Meltdown...
3 KB (295 words) - 20:51, 30 September 2022
instructions accurately which can be exploited in the Meltdown and Spectre security vulnerabilities. However, if this is not available other counters or timers...
11 KB (1,248 words) - 21:48, 13 November 2024
Denial-of-service attack Pentium FDIV bug Meltdown (security vulnerability) Spectre (security vulnerability) Collins, Robert R. (1998-05-01). "The Pentium...
12 KB (1,583 words) - 14:36, 13 August 2024
Microarchitectural Data Sampling (redirect from Fallout (security vulnerability))
hyperthreading. Nevertheless, the ZombieLoad vulnerability can be used by hackers exploiting the vulnerability to steal information recently accessed by...
14 KB (977 words) - 09:13, 15 August 2024
ARM architecture family (section Security extensions)
ARM processors Meltdown (security vulnerability) Reduced instruction set computer (RISC) RISC-V Spectre (security vulnerability) Unicore – a 32-register...
140 KB (13,593 words) - 16:14, 16 February 2025
JavaScript (redirect from JavaScript security vulnerabilities)
2010-02-18 at the Wayback Machine SecurityFocus, Microsoft WebViewFolderIcon ActiveX Control Buffer Overflow Vulnerability Archived 2011-10-11 at the Wayback...
83 KB (7,891 words) - 06:26, 15 February 2025
Lazy FP state restore (redirect from Spectre-NG 3)
as Lazy FP State Restore or LazyFP, is a security vulnerability affecting Intel Core CPUs. The vulnerability is caused by a combination of flaws in the...
7 KB (832 words) - 01:53, 18 November 2024
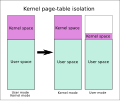
Kernel page-table isolation (category Transient execution CPU vulnerabilities)
macOS released similar updates. KPTI does not address the related Spectre vulnerability. The KPTI patches were based on KAISER (short for Kernel Address...
14 KB (1,275 words) - 09:13, 15 August 2024
Software Guard Extensions (section Spectre-like attack)
College London showed a proof of concept that the Spectre speculative execution security vulnerability can be adapted to attack the secure enclave. The...
22 KB (2,129 words) - 17:35, 10 January 2025
Dynamically Allocated Way Guard, a mitigation approach to the Spectre security vulnerability Alternative spelling of dog All pages with titles containing...
2 KB (218 words) - 23:05, 1 January 2025
settings CPU-X, an alternative of CPU-Z for Linux and FreeBSD Spectre (security vulnerability) Speculative Store Bypass (SSB) /proc/cpuinfo, a text file...
228 KB (12,773 words) - 18:20, 12 February 2025
Speculative execution (redirect from Speculative execution vulnerability)
Sampling Spectre SPOILER Pacman Anticiparallelism Out-of-order execution Slipstream (computer science) Speculative multithreading Hardware security bug Transient...
8 KB (978 words) - 23:32, 1 December 2024
School, in Bangalore, India Bounds Check Bypass Store, a Spectre-NG class security vulnerability This disambiguation page lists articles associated with...
262 bytes (64 words) - 20:08, 27 December 2019
Virtual machine escape (category Computer security exploits)
CVE-2007-1744 Directory traversal vulnerability in shared folders feature for VMware CVE-2008-0923 Directory traversal vulnerability in shared folders feature...
11 KB (1,139 words) - 00:23, 24 December 2024
Retbleed (category Transient execution CPU vulnerabilities)
and AMD chips. First made public in 2022, it is a variant of the Spectre vulnerability which exploits retpoline, which was a mitigation for speculative...
4 KB (305 words) - 09:13, 15 August 2024
Site isolation (category Internet security)
unbounded process use. In 2018, following the discovery of the Spectre and Meltdown vulnerabilities to the public, Google accelerated the work, culminating in...
23 KB (2,386 words) - 16:06, 22 January 2025