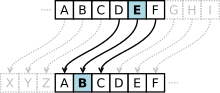
In the history of cryptography, a grille cipher was a technique for encrypting a plaintext by writing it onto a sheet of paper through a pierced sheet...
17 KB (2,243 words) - 15:06, 26 January 2024
steganography, which is a sub-branch of general cryptography. But the name Cardan was applied to grilles that may not have been Cardan's invention, and...
6 KB (784 words) - 22:27, 22 January 2024
Visual cryptography is a cryptographic technique which allows visual information (pictures, text, etc.) to be encrypted in such a way that the decrypted...
11 KB (1,412 words) - 17:32, 20 November 2024
machine) • Caesar cipher • Camellia (cipher) • CAPICOM • Capstone (cryptography) • Cardan grille • Card catalog (cryptology) • Carlisle Adams • CAST-128 • CAST-256...
67 KB (2,933 words) - 12:41, 17 October 2024
Cryptography, or cryptology (from Ancient Greek: κρυπτός, romanized: kryptós "hidden, secret"; and γράφειν graphein, "to write", or -λογία -logia, "study"...
99 KB (10,933 words) - 18:36, 19 November 2024
and topical guide to cryptography: Cryptography (or cryptology) – practice and study of hiding information. Modern cryptography intersects the disciplines...
20 KB (1,899 words) - 15:57, 22 November 2024
Transposition cipher (redirect from Transposition (cryptography))
In cryptography, a transposition cipher (also known as a permutation cipher) is a method of encryption which scrambles the positions of characters (transposition)...
25 KB (3,604 words) - 15:23, 5 November 2024
Classical cipher (redirect from Classical cryptography)
In cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. In contrast to modern...
15 KB (2,528 words) - 02:24, 15 June 2024
Zygalski sheets (category Cryptographic attacks)
was used by British and American cryptologists during World War II Grille (cryptography) Punched card Jacquard loom On 15 December 1938 the Germans increased...
10 KB (1,188 words) - 06:07, 21 December 2023
In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code, or Caesar shift, is one of the simplest and most widely...
19 KB (2,058 words) - 14:38, 20 October 2024
Substitution cipher (redirect from Substitution cryptography)
In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with...
30 KB (4,047 words) - 18:46, 28 October 2024
Null cipher (section Classical cryptography)
cipher used in classical cryptography along with substitution ciphers and transposition ciphers. In classical cryptography, a null is an extra character...
11 KB (1,498 words) - 01:12, 19 November 2024
One-time pad (category Cryptography)
In cryptography, the one-time pad (OTP) is an encryption technique that cannot be cracked, but requires the use of a single-use pre-shared key that is...
57 KB (7,613 words) - 09:47, 6 October 2024
used for encoding and decoding. The algorithm provides virtually no cryptographic security, and is often cited as a canonical example of weak encryption...
20 KB (2,036 words) - 20:26, 12 November 2024
Caprotti valve gear Gerolamo Cardano (1501–1576), Italy – Cardan grille (cryptography) Philip Cardew (1851–1910), UK – Hot-wire galvanometer Chester Carlson...
107 KB (12,077 words) - 15:11, 20 November 2024
Tabula recta (redirect from Cryptographic tableau)
In cryptography, the tabula recta (from Latin tabula rēcta) is a square table of alphabets, each row of which is made by shifting the previous one to the...
7 KB (939 words) - 23:25, 2 February 2024
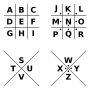
letters can be assigned to the grid. The Pigpen cipher offers little cryptographic security. It differentiates itself from other simple monoalphabetic...
10 KB (1,303 words) - 19:12, 18 November 2024
In classical cryptography, the Hill cipher is a polygraphic substitution cipher based on linear algebra. Invented by Lester S. Hill in 1929, it was the...
13 KB (2,241 words) - 21:56, 17 October 2024
Kasiski examination (category Cryptographic attacks)
Code, retrieved 30 November 2014 R. Morelli, R. Morelli, Historical Cryptography: The Vigenere Cipher, Trinity College Hartford, Connecticut, retrieved...
8 KB (1,129 words) - 21:01, 2 November 2024
(2012). Everyday Cryptography. Oxford University Press. p. 142. ISBN 978-0-19-162588-6. Laurence Dwight Smith (1955). Cryptography: The Science of Secret...
45 KB (5,937 words) - 11:20, 17 November 2024
In cryptography, a scytale (/ˈskɪtəliː/; also transliterated skytale, Ancient Greek: σκυτάλη skutálē "baton, cylinder", also σκύταλον skútalon) is a tool...
5 KB (726 words) - 21:57, 25 October 2024
Polybius square (section Cryptography)
smaller set of symbols, which is useful for telegraphy, steganography, and cryptography. The device was originally used for fire signalling, allowing for the...
11 KB (1,130 words) - 06:40, 8 February 2024
the author of a short book on cryptography and as the proponent of a modified Cardan grille known as a turning grille. He was born in Lemberg, the son...
2 KB (210 words) - 18:00, 24 October 2024
Index of coincidence (category Cryptographic attacks)
In cryptography, coincidence counting is the technique (invented by William F. Friedman) of putting two texts side-by-side and counting the number of times...
16 KB (2,347 words) - 15:16, 2 August 2024
In cryptography, the ADFGVX cipher was a manually applied field cipher used by the Imperial German Army during World War I. It was used to transmit messages...
13 KB (1,696 words) - 18:27, 12 February 2024
University Press, ISBN 978-0-521-00890-7 Gaines, Helen Fouché (1939), Cryptanalysis, Dover, ISBN 0-486-20097-3 Vigenère cipher Topics in cryptography...
6 KB (732 words) - 20:12, 20 October 2024
In classical cryptography, the running key cipher is a type of polyalphabetic substitution cipher in which a text, typically from a book, is used to provide...
10 KB (1,298 words) - 08:50, 11 November 2024
Pipher, Jill; Silverman, Joseph (2014). An Introduction to Mathematical Cryptography. Springer. p. 288. ISBN 9781493917112. "Autokey Calculator". Asecuritysite...
9 KB (1,276 words) - 15:02, 26 January 2024
Frequency analysis (category Cryptographic attacks)
a literary device than anything significant cryptographically. Index of coincidence Topics in cryptography Zipf's law A Void, a novel by Georges Perec...
16 KB (1,663 words) - 06:05, 8 April 2024