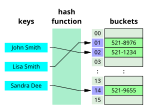
Linear hashing (LH) is a dynamic data structure which implements a hash table and grows or shrinks one bucket at a time. It was invented by Witold Litwin...
13 KB (1,731 words) - 21:42, 15 July 2024
perfect hash function can be created if all the keys are known ahead of time. The schemes of hashing used in integer universe assumption include hashing by...
52 KB (5,873 words) - 00:21, 27 September 2024
H(z,n) with probability close to n/(n + 1). Linear hashing and spiral hashing are examples of dynamic hash functions that execute in constant time but...
50 KB (7,536 words) - 12:34, 29 September 2024
Database index (section Linear hashing)
systems is linear hashing. Indices can be implemented using a variety of data structures. Popular indices include balanced trees, B+ trees and hashes. In Microsoft...
17 KB (2,458 words) - 23:02, 27 September 2024
password hashing is performed; original passwords cannot be recalculated from the stored hash value. However, use of standard cryptographic hash functions...
48 KB (6,237 words) - 11:39, 3 October 2024
double hashing, linear probing is a form of open addressing. In these schemes, each cell of a hash table stores a single key–value pair. When the hash function...
28 KB (3,605 words) - 04:19, 21 June 2024
In computer science, consistent hashing is a special kind of hashing technique such that when a hash table is resized, only n / m {\displaystyle n/m} keys...
22 KB (2,594 words) - 19:16, 22 September 2024
Double hashing is a computer programming technique used in conjunction with open addressing in hash tables to resolve hash collisions, by using a secondary...
9 KB (1,570 words) - 10:56, 18 May 2024
perfect hashing in Java MPHSharp: perfect hashing methods in C# BBHash: minimal perfect hash function in header-only C++ Perfect::Hash, perfect hash generator...
24 KB (2,956 words) - 14:27, 22 July 2024
Extendible hashing: ZFS and GFS" and "Table 4.1: Directory organization in filesystems" Trie Hash table Stable hashing Consistent hashing Linear hashing Fagin...
11 KB (1,732 words) - 15:04, 29 May 2024
List of data structures (redirect from Linear data structure)
Distributed hash table Double hashing Dynamic perfect hash table Hash array mapped trie Hash list Hash table Hash tree Hash trie Koorde Prefix hash tree Rolling...
9 KB (912 words) - 16:16, 9 July 2024
Larson) is a computer scientist. He is most famous for inventing the linear hashing algorithm with Witold Litwin. Paul Larson is currently a senior researcher...
2 KB (103 words) - 20:29, 28 September 2024
materials. Zobrist hashing is the first known instance of the generally useful underlying technique called tabulation hashing. Zobrist hashing starts by randomly...
7 KB (851 words) - 21:58, 26 February 2024
Open addressing (redirect from Closed hashing)
Double hashing can also require more computation than other forms of probing. Some open addressing methods, such as Hopscotch hashing, Robin Hood hashing,...
8 KB (1,044 words) - 02:38, 25 September 2024
families are known (for hashing integers, vectors, strings), and their evaluation is often very efficient. Universal hashing has numerous uses in computer...
29 KB (4,875 words) - 10:36, 18 April 2024
hopscotch hashing, as in cuckoo hashing, and unlike in linear probing, a given item will always be inserted-into and found-in the neighborhood of its hashed bucket...
7 KB (918 words) - 10:20, 1 June 2024
inserting a new key into a cuckoo hashing table may push an older key to a different location in the table. Cuckoo hashing was first described by Rasmus Pagh...
23 KB (2,563 words) - 18:01, 1 August 2024
In machine learning, feature hashing, also known as the hashing trick (by analogy to the kernel trick), is a fast and space-efficient way of vectorizing...
20 KB (3,124 words) - 18:26, 13 May 2024
Fareham, UK County Louth, Ireland (code LH) Linear hashing, a computer science algorithm for a dynamic hash LH, a type of single-mode optical fiber LH...
2 KB (327 words) - 21:51, 15 July 2024
A rolling hash (also known as recursive hashing or rolling checksum) is a hash function where the input is hashed in a window that moves through the input...
14 KB (2,011 words) - 08:23, 4 October 2024
Spiral hashing, also known as Spiral Storage is an extensible hashing algorithm. As in all hashing schemes, spiral hashing stores records in a varying...
4 KB (461 words) - 11:49, 13 August 2023
computer science and data mining, MinHash (or the min-wise independent permutations locality sensitive hashing scheme) is a technique for quickly estimating...
25 KB (3,184 words) - 23:20, 4 December 2023
take place when a hash collision happens and this method is implemented. Some types of probing are linear probing, double hashing, and quadratic probing...
9 KB (1,130 words) - 16:51, 9 August 2024
element vary. Linear search is rarely practical because other search algorithms and schemes, such as the binary search algorithm and hash tables, allow...
8 KB (1,010 words) - 09:15, 9 April 2024
probability. Unfortunately, we do not have linear perfect hashing, so we have to use an almost linear hash function, i.e. a function h such that: h (...
17 KB (2,664 words) - 18:47, 28 July 2024
Rabin–Karp algorithm (category Hashing)
Michael O. Rabin (1987) that uses hashing to find an exact match of a pattern string in a text. It uses a rolling hash to quickly filter out positions of...
14 KB (1,975 words) - 15:46, 18 April 2024
state expandable hashing expander graph exponential extended binary tree extended Euclidean algorithm extended k-d tree extendible hashing external index...
35 KB (3,137 words) - 03:02, 24 July 2024
Quadratic probing (redirect from Quadratic hashing)
alternative to linear probing because it incurs less clustering. Quadratic probing exhibits better locality of reference than many other hash table such as...
6 KB (884 words) - 01:08, 28 November 2023
Implementation of the Whirlpool Hashing Function RHash, an open source command-line tool, which can calculate and verify Whirlpool hash. Perl Whirlpool module...
11 KB (1,054 words) - 03:57, 19 March 2024