In computer science, hierarchical protection domains, often called protection rings, are mechanisms to protect data and functionality from faults (by...
30 KB (3,750 words) - 00:41, 22 July 2024
network, a ring network affords fault tolerance to the network because there are two paths between any two nodes on the network. Ring protection is the system...
2 KB (286 words) - 22:31, 14 January 2024
Ethernet Ring Protection Switching (ERPS) is an effort at ITU-T under G.8032 Recommendation to provide sub-50ms protection and recovery switching for...
5 KB (755 words) - 23:34, 14 February 2024
each segment has a protection ring for reading, writing and execution; an attempt by a process with a higher ring number than the ring number for the segment...
18 KB (2,273 words) - 11:11, 19 March 2024
sphere Ring (data structure), or ring buffer Ring network, a network topology Protection ring, in computer security Ring (software), VOIP software Ring circuit...
5 KB (665 words) - 22:41, 17 March 2024
System Management Mode (redirect from Ring -2)
System Management Mode (SMM, sometimes called ring −2 in reference to protection rings) is an operating mode of x86 central processor units (CPUs) in which...
13 KB (1,406 words) - 19:24, 25 July 2024
Section Shared Protection Ring (MS-SP Ring), which offers a shared protection mode, and Multiplex Section Dedicated Protection Ring (MS-DP Ring), which offers...
4 KB (508 words) - 08:01, 6 September 2023
: 153 This preemptive scheduler usually runs in the most privileged protection ring, meaning that interruption and then resumption are considered highly...
12 KB (1,384 words) - 21:22, 20 August 2024
Write protection is any physical mechanism that prevents writing, modifying, or erasing data on a device. Most commercial software, audio and video on...
4 KB (531 words) - 10:58, 20 December 2023
Magicians Ring 1, a protection ring in computer security Search for "ring 1" , "ring one", or "ring i" on Wikipedia. Ring (disambiguation) One ring (disambiguation)...
689 bytes (116 words) - 12:05, 7 August 2022
mode separate from kernel mode involves operating system protection rings. Protection rings, in turn, are implemented using CPU modes. Typically, kernel...
5 KB (514 words) - 19:48, 30 July 2024
(computing) Privilege separation Protection ring setuid sudo Saltzer, Jerome H.; Schroeder, Michael D. (1975). "The protection of information in computer systems"...
15 KB (1,760 words) - 11:17, 31 July 2024
Kernel (operating system) (section Protection)
architectures, such as supervisor mode, kernel mode, CPL0, DPL0, ring 0, etc. See Protection ring for more information. "Kernel". Linfo. Bellevue Linux Users...
82 KB (10,157 words) - 10:56, 19 August 2024
most notable ring-based protection techniques for mesh networks are ring covers, cycle double covers and p-cycles (pre-configured protection cycles). The...
11 KB (1,475 words) - 00:00, 9 April 2024
Egyptian, encircle, while the shen ring represented eternal protection. In Gardiner's sign list, it is sign V9. The shen ring is most often seen carried by...
3 KB (329 words) - 03:27, 4 August 2024
Synchronous optical networking (redirect from SONET ring)
the ring could only act as pass-through nodes. The SDH equivalent of UPSR is subnetwork connection protection (SNCP); SNCP does not impose a ring topology...
45 KB (5,524 words) - 17:14, 25 April 2024
Packet Ring, and Ethernet Ring Protection Switching. IEEE 802.5 networks – also known as IBM Token Ring networks – avoid the weakness of a ring topology...
7 KB (986 words) - 15:55, 14 August 2024
Object-capability model Protection ring Relationship-based access control (ReBAC) Role-based access control (RBAC) Take-grant protection model Discretionary...
2 KB (184 words) - 14:25, 17 July 2024
processor as a four-layer protection ring, but four rings was found to be too cumbersome to program and too slow to operate. Protection ring architecture is now...
28 KB (3,315 words) - 04:38, 2 June 2024
resources directly. In a low-level microcontroller, the chip might lack protection modes and have no memory management unit (MMU). In these chips, the execution...
13 KB (1,800 words) - 05:48, 22 February 2024
supply design, a ring circuit is an electrical wiring technique in which sockets and the distribution point are connected in a ring. It is contrasted...
14 KB (1,929 words) - 10:02, 6 May 2024
"Ring a Ring o' Roses", "Ring a Ring o' Rosie", or (in the United States) "Ring Around the Rosie", is a nursery rhyme, folk song and playground singing...
20 KB (2,310 words) - 09:19, 6 August 2024
Ringfencing (redirect from Ring-fencing)
taxation purposes avoiding sanctions against a country. In asset protection arrangements, ring-fencing can be employed through segregating specific assets...
5 KB (595 words) - 17:01, 19 July 2024
Information hiding Layer (object-oriented design) Namespace violation Protection ring Operating system, an abstraction layer between a program and computer...
6 KB (783 words) - 13:03, 16 August 2024
increasing experience gain. Assist Magic Rings grant helpful abilities, such as protection or healing. "Magic Rings" can be found throughout the island in...
11 KB (1,121 words) - 20:16, 1 November 2023
(software) Hardware-dependent software (HDS) Nanokernel Picokernel Protection ring "Portability and supported hardware platforms". The NetBSD Foundation...
12 KB (1,506 words) - 08:27, 22 July 2024
SONET/SDH rings, carriers implemented ring protection such as SONET Unidirectional Path Switched Ring (UPSR) (also called Sub-Network Connection Protection (SCNP)...
24 KB (2,372 words) - 04:35, 31 July 2024
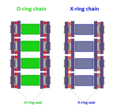
non-O-ring chains as it has less friction than O-ring chain while providing adequate lubrication and protection against foreign elements which also increases...
4 KB (381 words) - 17:16, 19 January 2024
available Ethernet switched rings (commonly used in Metro Ethernet) to replace legacy TDM based transport protection fiber rings. Other implementations include...
4 KB (539 words) - 14:59, 8 August 2024
interlocking arrangement of five rings, and usage of the word "Olympic". The rings are not eligible for copyright protection[where?], both because of their...
54 KB (5,978 words) - 07:21, 22 August 2024