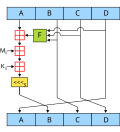
The MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value. MD5 was designed by Ronald Rivest in 1991 to replace an...
47 KB (4,650 words) - 04:08, 26 July 2024
In cryptography, CRAM-MD5 is a challenge–response authentication mechanism (CRAM) based on the HMAC-MD5 algorithm. As one of the mechanisms supported...
7 KB (839 words) - 21:00, 14 May 2023
Digest access authentication (redirect from DIGEST-MD5)
of string variables): HA1 = MD5(username:realm:password) HA2 = MD5(method:digestURI) response = MD5(HA1:nonce:HA2) An MD5 hash is a 16-byte value. The...
24 KB (2,843 words) - 13:39, 13 July 2024
Md5sum (section Create MD5 hash file hash.md5)
computer program that calculates and verifies 128-bit MD5 hashes, as described in RFC 1321. The MD5 hash functions as a compact digital fingerprint of a...
5 KB (469 words) - 17:47, 8 December 2023
Cryptographic hash function (section MD5)
attacker to find two messages with the same MD5 hash, then they can find as many additional messages with that same MD5 hash as they desire, with no greater...
48 KB (6,228 words) - 08:01, 25 June 2024
The National Security Innovation Network (previously named the MD5 National Security Technology Accelerator) is a United States Department of Defense...
12 KB (1,196 words) - 12:12, 4 July 2024
present, it is hidden using a method based on the RSA Message Digest Algorithm MD5. Accounting is described in RFC 2866. When network access is granted to the...
33 KB (2,791 words) - 15:46, 18 July 2024
Crypt (C) (section MD5-based scheme)
where id: an identifier representing the hashing algorithm (such as 1 for MD5, 5 for SHA-256 etc.) param name and its value: hash complexity parameters...
28 KB (3,039 words) - 21:59, 6 July 2024
are specific to the hash function they were created for e.g., MD5 tables can crack only MD5 hashes. The theory of this technique was invented by Philippe...
24 KB (3,446 words) - 08:05, 23 June 2024
(Hex) ] Message Digest 5 (MD5) Supported by G2 (Gnutella2), such hashes are vulnerable to hash collision attacks. xt=urn:md5:[ MD5 Hash (Hex) ] There are...
20 KB (1,304 words) - 11:27, 7 March 2024
SMB, etc.; this eases firewall administration and network security CRAM-MD5 – configurable client–server authentication GZIP/LZO – client-side compression...
9 KB (663 words) - 08:51, 12 July 2024
older SASL mechanism for ESMTP authentication (ESMTPA) is CRAM-MD5, and uses of the MD5 algorithm in HMACs (hash-based message authentication codes) are...
10 KB (1,229 words) - 18:58, 17 April 2024
version SHA-1. SHA-1: A 160-bit hash function which resembles the earlier MD5 algorithm. This was designed by the National Security Agency (NSA) to be...
3 KB (464 words) - 13:15, 22 July 2024
(458732) 2011 MD5 is an Apollo near-Earth asteroid around 1.2 kilometers (0.75 miles) in diameter. It is the largest asteroid known to have passed closer...
4 KB (267 words) - 18:46, 27 November 2023
attacks against two very commonly used hash functions, MD5 and SHA-1. The collision attacks against MD5 have improved so much that, as of 2007, it takes just...
17 KB (2,010 words) - 21:48, 17 May 2024
pointing to the duplicate. It first compares file sizes, partial MD5 signatures, full MD5 signatures, and then performs a byte-by-byte comparison for verification...
2 KB (88 words) - 07:36, 4 March 2024
and SSL, PGP, SSH, S/MIME, and IPsec. Those applications can also use MD5; both MD5 and SHA-1 are descended from MD4. SHA-1 and SHA-2 are the hash algorithms...
51 KB (5,762 words) - 21:53, 22 July 2024
Windows. Examples of hashcat-supported hashing algorithms are LM hashes, MD4, MD5, SHA-family and Unix Crypt formats as well as algorithms used in MySQL and...
9 KB (891 words) - 12:14, 29 May 2024
layer offering data integrity and data confidentiality services. DIGEST-MD5 provides an example of mechanisms which can provide a data-security layer...
7 KB (694 words) - 09:42, 13 March 2024
Extensible Authentication Protocol (redirect from EAP-MD5)
about 40 different methods defined. Methods defined in IETF RFCs include EAP-MD5, EAP-POTP, EAP-GTC, EAP-TLS, EAP-IKEv2, EAP-SIM, EAP-AKA, and EAP-AKA'. Additionally...
34 KB (4,172 words) - 23:18, 24 April 2024
Windows PWL files Cisco IOS – MD5 hashes Cisco PIX – MD5 hashes APOP – MD5 hashes CRAM-MD5 MD5 hashes OSPF – MD5 hashes RIPv2 MD5 hashes VRRP – HMAC hashes...
7 KB (547 words) - 00:46, 25 July 2024
Hash collision (section MD5)
specific collisions. Take into account the following hash algorithms – CRC-32, MD5, and SHA-1. These are common hash algorithms with varying levels of collision...
12 KB (1,463 words) - 03:47, 20 June 2024
Alice sends a hashed version of her password instead, like in CRAM-MD5 or DIGEST-MD5. As it is a hash, Mallory doesn't get the password itself. And because...
15 KB (1,892 words) - 14:00, 27 May 2024
length is 128 bits. The algorithm has influenced later designs, such as the MD5, SHA-1 and RIPEMD algorithms. The initialism "MD" stands for "Message Digest"...
8 KB (823 words) - 02:45, 11 July 2024
Enhancements "Password hashing with MD5-crypt in relation to MD5 – Vidar's Blog". "Implementation of SHA512-crypt vs MD5-crypt – Vidar's Blog". "Modular Crypt...
15 KB (1,941 words) - 11:36, 15 July 2024
to demonstrate that the MD5 message digest algorithm is insecure by finding a collision – two messages that produce the same MD5 hash. The project went...
4 KB (506 words) - 20:19, 25 September 2022
clear-text, but the body including passwords is obfuscated with an MD5-based method. The MD5-based obfuscation method is similar to that used for the RADIUS...
11 KB (1,193 words) - 13:44, 7 May 2024
Id Tech 4 (redirect from MD5 (file format))
id Tech 4, popularly known as the Doom 3 engine, is a game engine developed by id Software and first used in the video game Doom 3. The engine was designed...
27 KB (2,516 words) - 01:36, 22 July 2024
Gravatars are loaded from the Gravatar web server, using a URL containing an MD5 hash of the associated email address. This method has, however, been shown...
9 KB (995 words) - 08:57, 9 July 2024