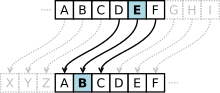
In cryptography, encryption is the process of transforming (more specifically, encoding) information in a way that, ideally, only authorized parties can...
35 KB (3,687 words) - 11:44, 15 November 2024
Public-key cryptography (redirect from Asymmetric key encryption algorithm)
public-key cryptosystems, with different security goals, including public-key encryption, public-key key encapsulation, Diffie-Hellman key exchange, and digital...
40 KB (4,507 words) - 23:07, 24 November 2024
Advanced Encryption Standard (AES), also known by its original name Rijndael (Dutch pronunciation: [ˈrɛindaːl]), is a specification for the encryption of electronic...
50 KB (5,624 words) - 02:56, 23 November 2024
Homomorphic encryption is a form of encryption that allows computations to be performed on encrypted data without first having to decrypt it. The resulting...
40 KB (4,409 words) - 00:38, 14 November 2024
Authenticated Encryption (AE) is an encryption scheme which simultaneously assures the data confidentiality (also known as privacy: the encrypted message...
19 KB (2,086 words) - 19:19, 8 November 2024
Symmetric-key algorithm (redirect from Symmetric encryption)
algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical...
15 KB (1,544 words) - 20:48, 3 November 2024
In cryptography, the ElGamal encryption system is an asymmetric key encryption algorithm for public-key cryptography which is based on the Diffie–Hellman...
10 KB (1,476 words) - 20:38, 7 September 2024
Cryptography prior to the modern age was effectively synonymous with encryption, converting readable information (plaintext) to unintelligible nonsense...
99 KB (10,936 words) - 05:39, 24 November 2024
End-to-end encryption (E2EE) is a private communication system in which only communicating users can participate. As such, no one else, including the communication...
29 KB (3,041 words) - 20:31, 19 November 2024
RSA (cryptosystem) (redirect from RSA encryption)
That system was declassified in 1997. In a public-key cryptosystem, the encryption key is public and distinct from the decryption key, which is kept secret...
60 KB (7,790 words) - 07:32, 21 November 2024
Link encryption is an approach to communications security that encrypts and decrypts all network traffic at each network routing point (e.g. network switch...
2 KB (205 words) - 12:57, 24 October 2023
Block cipher mode of operation (redirect from Encryption mode)
itself is only suitable for the secure cryptographic transformation (encryption or decryption) of one fixed-length group of bits called a block. A mode...
52 KB (5,878 words) - 15:11, 20 September 2024
In cryptography and steganography, plausibly deniable encryption describes encryption techniques where the existence of an encrypted file or message is...
24 KB (2,832 words) - 16:35, 5 September 2024
BitLocker (redirect from Bitlocker Drive Encryption)
volume encryption feature included with Microsoft Windows versions starting with Windows Vista. It is designed to protect data by providing encryption for...
37 KB (3,499 words) - 05:01, 16 November 2024
Disk encryption is a technology which protects information by converting it into code that cannot be deciphered easily by unauthorized people or processes...
17 KB (2,194 words) - 03:24, 4 September 2024
cryptography, null encryption (or selecting null cipher or NONE cipher) is choosing not to use encryption in a system where various encryption options are offered...
1 KB (120 words) - 07:06, 15 July 2024
Pretty Good Privacy (redirect from Pgp encryption)
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing...
55 KB (6,148 words) - 17:35, 22 November 2024
Transport Layer Security (redirect from Transport layer encryption)
authenticated encryption ciphers, used mainly for Galois/Counter Mode (GCM) and CCM mode of Advanced Encryption Standard (AES) encryption. TLS Extensions...
179 KB (17,618 words) - 14:07, 15 November 2024
The Data Encryption Standard (DES /ˌdiːˌiːˈɛs, dɛz/) is a symmetric-key algorithm for the encryption of digital data. Although its short key length of...
59 KB (6,543 words) - 16:59, 10 November 2024
as cascade encryption, cascade ciphering, multiple encryption, and superencipherment. Superencryption refers to the outer-level encryption of a multiple...
10 KB (1,396 words) - 11:50, 4 October 2024
Probabilistic encryption is the use of randomness in an encryption algorithm, so that when encrypting the same message several times it will, in general...
4 KB (583 words) - 10:12, 1 April 2022
Caesar cipher (redirect from Caesar encryption)
Caesar's code, or Caesar shift, is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in...
19 KB (2,058 words) - 14:38, 20 October 2024
Email encryption is encryption of email messages to protect the content from being read by entities other than the intended recipients. Email encryption may...
14 KB (1,671 words) - 14:27, 30 June 2024
Dynamic Encryption is a cryptographic principle that enables two parties to change the encryption algorithm for every transaction. The principle of Dynamic...
4 KB (358 words) - 14:24, 8 July 2024
Triple DES (redirect from Triple Data Encryption Standard)
In cryptography, Triple DES (3DES or TDES), officially the Triple Data Encryption Algorithm (TDEA or Triple DEA), is a symmetric-key block cipher, which...
23 KB (2,946 words) - 08:30, 25 November 2024
Database encryption can generally be defined as a process that uses an algorithm to transform data stored in a database into "cipher text" that is incomprehensible...
27 KB (3,217 words) - 06:06, 15 September 2024
A deterministic encryption scheme (as opposed to a probabilistic encryption scheme) is a cryptosystem which always produces the same ciphertext for a...
7 KB (853 words) - 03:46, 23 September 2023
Key size (redirect from 128 bit encryption)
therefore, be large enough that a brute-force attack (possible against any encryption algorithm) is infeasible – i.e. would take too long and/or would take...
29 KB (3,213 words) - 18:15, 18 September 2024
Honey encryption is a type of data encryption that "produces a ciphertext, which, when decrypted with an incorrect key as guessed by the attacker, presents...
5 KB (652 words) - 17:41, 19 August 2024
Functional encryption (FE) is a generalization of public-key encryption in which possessing a secret key allows one to learn a function of what the ciphertext...
5 KB (536 words) - 03:14, 4 January 2024