Trusted Computing (TC) is a technology developed and promoted by the Trusted Computing Group. The term is taken from the field of trusted systems and...
42 KB (5,186 words) - 19:55, 10 October 2024
enable trusted computing features in computers and mobile devices. Related efforts involved Trusted Network Connect, to bring trusted computing to network...
6 KB (610 words) - 20:27, 25 August 2024
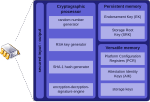
random number generation. Trusted Platform Module (TPM) was conceived by a computer industry consortium called Trusted Computing Group (TCG). It evolved...
80 KB (6,672 words) - 08:00, 28 October 2024
secure upgrades of the trusted computing base poses bootstrap problems of its own. As stated above, trust in the trusted computing base is required to make...
12 KB (1,629 words) - 11:22, 20 August 2024
The Next-Generation Secure Computing Base (NGSCB; codenamed Palladium and also known as Trusted Windows) is a software architecture designed by Microsoft...
78 KB (7,356 words) - 06:39, 28 September 2024
secure multi-party computation, and Trusted Computing. Confidential computing is promoted by the Confidential Computing Consortium (CCC) industry group,...
45 KB (4,302 words) - 18:33, 9 October 2024
authentic operating system starts in a trusted environment, which can then be considered trusted. Provision of a trusted operating system with additional security...
13 KB (1,545 words) - 04:33, 31 August 2024
In computing, a trusted client is a device or program controlled by the user of a service, but with restrictions designed to prevent its use in ways not...
3 KB (320 words) - 01:47, 17 October 2022
trusted system is one that is relied upon to a specified extent to enforce a specified security policy. This is equivalent to saying that a trusted system...
17 KB (2,358 words) - 22:49, 30 July 2023
The term Trustworthy Computing (TwC) has been applied to computing systems that are inherently secure, available, and reliable. It is particularly associated...
9 KB (752 words) - 13:30, 12 October 2024
provers. The implementation of the underlying ML compiler adds to the trusted computing base. Work on CakeML resulted in a formally verified ML compiler,...
5 KB (614 words) - 12:41, 25 July 2024
based on ARM TrustZone technology, conforming to the TR1 standard, were later launched, such as Trusted Foundations developed by Trusted Logic. Work on...
35 KB (3,185 words) - 05:13, 31 July 2024
Kingdom independent charity Trusted Computing Platform Alliance, former computer industry group succeeded by the Trusted Computing Group This disambiguation...
454 bytes (87 words) - 00:50, 16 October 2024
verification methods where feasible. Trusted Design Environment is where the TCB is designed in a trusted facility with only trusted (cleared) personnel. The publication...
18 KB (2,101 words) - 21:38, 25 February 2024
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security...
22 KB (2,318 words) - 18:53, 20 October 2024
complex as well as error-prone. The Trusted Computer System Evaluation Criteria (TCSEC) concept of trusted computing base (TCB) minimization is a far more...
15 KB (1,760 words) - 23:33, 8 October 2024
received from any non-trusted source, like any peer in the P2P network. Then, the received hash tree is checked against the trusted top hash, and if the...
15 KB (1,788 words) - 20:42, 10 September 2024
need a third-party repository service of some kind. 'Trusted' means that a system needs to be trusted to act in your interests, but it has the option (either...
6 KB (843 words) - 18:05, 16 October 2024
self-encrypting drives (SED). The specification is published by the Trusted Computing Group Storage Workgroup. The Opal SSC (Security Subsystem Class) is...
11 KB (822 words) - 22:43, 29 April 2024
Trusted Network Connect (TNC) is an open architecture for Network Access Control, promulgated by the Trusted Network Connect Work Group (TNC-WG) of the...
9 KB (691 words) - 20:23, 20 August 2022
VeraCrypt (section Trusted Platform Module)
original on June 11, 2014. Retrieved December 18, 2013. Autonomic and Trusted Computing: 4th International Conference (Google Books). ATC. 2007. ISBN 9783540735465...
37 KB (3,203 words) - 08:02, 15 September 2024
IP services,” NetworkWorld, November 3, 2003, retrieved 11/27/13. Trusted Computing Group Members list,(contributors), retrieved 11/1/13 "Infoblox Joins...
13 KB (1,174 words) - 17:33, 29 October 2024
Inouye (D-HI) Bill Nelson (D-FL) Ted Stevens (R-AK) Trusted Computing Trusted Computing Group Trusted Platform Module 107th Congress, 2nd session, S. 2048...
3 KB (287 words) - 08:35, 30 August 2023
Easter egg (media) (redirect from Easter eggs (computing))
could also bypass testing. Kabay asserts that this undermined the Trusted Computing Base, a paradigm of trustworthy hardware and software in place since...
52 KB (5,567 words) - 19:52, 4 November 2024
intended to ensure that only trusted software and hardware can be used while still retaining flexibility. A chain of trust is designed to allow multiple...
4 KB (465 words) - 10:02, 4 September 2024
Intel Management Engine (redirect from Trusted Execution Engine)
Base Samsung Knox Spectre (security vulnerability) Trusted Computing Trusted Execution Technology Trusted Platform Module Oster, Joseph E. (September 3, 2019)...
47 KB (4,481 words) - 18:55, 22 September 2024
on a phone using letters and symbols Trusted Execution Technology, Intel's implementation of Trusted Computing TXT records, a type of Domain Name System...
975 bytes (148 words) - 18:08, 25 April 2024
centralized computing exists when the majority of functions are carried out, or obtained from a remote centralized location. Decentralized computing is a trend...
8 KB (856 words) - 21:32, 14 October 2024
Security kernel (category Computing terminology)
programs can be accessed. Hardware, firmware, and software elements of a trusted computing base that implement the reference monitor concept. This article incorporates...
962 bytes (127 words) - 00:00, 16 September 2024