In computer science, brute-force search or exhaustive search, also known as generate and test, is a very general problem-solving technique and algorithmic...
14 KB (1,973 words) - 00:28, 15 November 2024
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly...
21 KB (2,238 words) - 15:21, 21 November 2024
mathematical proof Brute-force attack, a cryptanalytic attack Brute-force search, a computer problem-solving technique Brute Force (musician) (born 1940)...
1 KB (211 words) - 06:46, 9 March 2023
security failure because it's no faster than brute force search, after all, it is the brute force search. Pseudorandom-function advantage Key-recovery...
6 KB (875 words) - 12:05, 9 April 2024
Algorithms for these problems include the basic brute-force search (also called "naïve" or "uninformed" search), and a variety of heuristics that try to exploit...
12 KB (1,574 words) - 07:35, 9 July 2024
clique, one can systematically inspect all subsets, but this sort of brute-force search is too time-consuming to be practical for networks comprising more...
84 KB (9,905 words) - 17:15, 23 September 2024
permutations (ordered combinations) and see which one is cheapest (using brute-force search). The running time for this approach lies within a polynomial factor...
86 KB (11,528 words) - 05:20, 22 November 2024
Sudoku solving algorithms (category Search algorithms)
algorithm, which is a type of brute force search. Backtracking is a depth-first search (in contrast to a breadth-first search), because it will completely...
15 KB (1,917 words) - 19:10, 20 November 2024
different keys, at the same time. This significantly speeds up a brute force search implemented in software, although the factor is too low for a practical...
9 KB (1,222 words) - 00:48, 24 May 2024
by the Electronic Frontier Foundation (EFF) in 1998, to perform a brute force search of the Data Encryption Standard (DES) cipher's key space – that is...
10 KB (1,031 words) - 05:27, 28 February 2023
solution can be verified quickly (namely, in polynomial time) and a brute-force search algorithm can find a solution by trying all possible solutions. The...
30 KB (3,617 words) - 17:49, 12 November 2024
algorithm searches for occurrences of P in T by performing explicit character comparisons at different alignments. Instead of a brute-force search of all...
22 KB (2,769 words) - 09:51, 24 September 2024
count can be increased to make it slower, so it remains resistant to brute-force search attacks even with increasing computation power. The bcrypt function...
27 KB (2,833 words) - 15:52, 8 November 2024
depth searched or some type of average. Brute-force search Combinatorial explosion Combinatorial optimization Search algorithm State space search Russell...
3 KB (342 words) - 19:42, 19 July 2024
cryptanalysis can break the revised version with less complexity than brute force search (a certificational weakness), the attack requires 2 88.5 {\displaystyle...
2 KB (241 words) - 12:27, 1 October 2024
Knight's tour (section Brute-force algorithms)
Some of these methods are algorithms, while others are heuristics. A brute-force search for a knight's tour is impractical on all but the smallest boards...
21 KB (2,317 words) - 23:38, 15 November 2024
Backtracking Branch and bound Brute-force search Divide and conquer Dynamic programming Greedy algorithm Recursion Prune and search Kernelization Iterative...
1 KB (80 words) - 08:18, 27 February 2024
to decrease the probability of obtaining a valid one by means of a brute-force search. Many servers perform additional verification of the client, in case...
3 KB (375 words) - 12:24, 12 April 2023
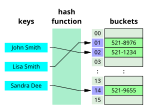
function assumes that the set of possible hash inputs is too large for a brute force search. However if a given hash value is known to have been produced from...
7 KB (895 words) - 15:44, 13 April 2024
against keys, the brute force key space search attack. A sufficiently long, randomly chosen, key can resist any practical brute force attack, though not...
3 KB (416 words) - 23:00, 17 September 2024
Data Encryption Standard (section Brute-force attack)
(strengthened against differential cryptanalysis, but weakened against brute-force attacks), which was published as an official Federal Information Processing...
59 KB (6,543 words) - 16:59, 10 November 2024
Key size (section Brute-force attack)
in what is known as a brute-force attack. Because longer symmetric keys require exponentially more work to brute force search, a sufficiently long symmetric...
29 KB (3,213 words) - 18:15, 18 September 2024
Rainbow table (category Search algorithms)
tradeoff: they use less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing...
24 KB (3,485 words) - 20:31, 22 November 2024
the British Museum." Bogosort Branch and bound Breadth-first search Brute-force search This article incorporates public domain material from Paul E...
1 KB (136 words) - 00:05, 28 February 2023
combination with another mode Free and open-source software portal Brute-force search Brute-force attack Crack (password software) "john-users – Re: When was...
8 KB (777 words) - 19:25, 21 November 2024
Hamiltonian path problem (section Brute force)
paths in a given n-vertex graph (and are, in a complete graph), so a brute force search algorithm that tests all possible sequences would be very slow. An...
21 KB (2,518 words) - 19:02, 20 August 2024
Branch and bound (redirect from Least discrepancy search)
would amount to brute-force enumeration of candidate solutions and testing them all. To improve on the performance of brute-force search, a B&B algorithm...
20 KB (2,426 words) - 15:24, 7 August 2024
{\displaystyle 2^{3}=8} possibilities. In this small example, one can use brute-force search to try all possible assignments and check if they satisfy the formula...
10 KB (1,328 words) - 08:01, 8 August 2024
determined from the UUID, even if one of them is specified, except by brute-force search. RFC 4122 recommends version 5 (SHA-1) over version 3 (MD5), and warns...
37 KB (4,510 words) - 07:02, 8 November 2024
data cannot masquerade as the client unless they first perform a brute force search for the password. In layman's terms, during SRP (or any other PAKE...
28 KB (3,404 words) - 05:29, 27 October 2024