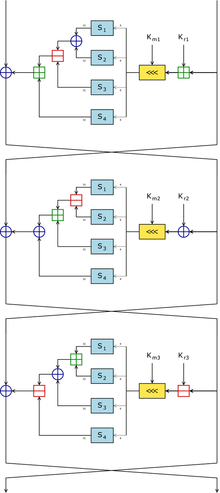
In cryptography, CAST-256 (or CAST6) is a symmetric-key block cipher published in June 1998. It was submitted as a candidate for the Advanced Encryption...
3 KB (331 words) - 04:48, 18 March 2024
Advanced Encryption Standard (redirect from AES-256)
a block size of 128 bits, but three different key lengths: 128, 192 and 256 bits. AES has been adopted by the U.S. government. It supersedes the Data...
50 KB (5,656 words) - 17:43, 13 February 2025
Tavares using the CAST design procedure. Another member of the CAST family of ciphers, CAST-256 (a former AES candidate) was derived from CAST-128. According...
4 KB (378 words) - 19:55, 13 April 2024
Feistel-like MIX function. Feistel or modified Feistel: Generalised Feistel: CAST-256 CLEFIA MacGuffin RC2 RC6 Skipjack SMS4 Cryptography Stream cipher...
10 KB (1,316 words) - 19:41, 2 February 2025
and submitted from several countries. They were, in alphabetical order: CAST-256, CRYPTON, DEAL, DFC, E2, FROG, HPC, LOKI97, MAGENTA, MARS, RC6, Rijndael...
10 KB (1,040 words) - 10:14, 4 January 2025
cryptography CAST-256, a block cipher in cryptography Cast (disambiguation) This disambiguation page lists articles associated with the title CAST. If an internal...
2 KB (316 words) - 22:00, 6 February 2024
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
8 KB (849 words) - 09:53, 27 November 2024
tiny-AES-c Small portable AES128/192/256 in C (suitable for embedded systems) AES-256 A byte-oriented portable AES-256 implementation in C Solaris Cryptographic...
12 KB (1,295 words) - 02:53, 21 December 2024
all-zero. For CFB-8, an all-zero IV and an all-zero plaintext, causes 1/256 of keys to generate no encryption, plaintext is returned as ciphertext. For...
52 KB (5,877 words) - 03:03, 6 March 2025
of time to decode a 256 bit AES cipher as it would a conventional computer to decode a 128 bit AES cipher. For this reason, AES-256 is believed to be "quantum...
15 KB (1,540 words) - 01:32, 23 January 2025
key and initialization vector value, GCM is limited to encrypting 239 − 256 bits of plain text (64 GiB). NIST Special Publication 800-38D includes guidelines...
23 KB (3,051 words) - 02:16, 23 February 2025
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
4 KB (398 words) - 12:58, 8 January 2025
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
99 KB (10,944 words) - 13:35, 20 January 2025
(2009-08-23). "New Linear Cryptanalytic Results of Reduced-Round of CAST-128 and CAST-256". Selected Areas in Cryptography. Lecture Notes in Computer Science...
15 KB (801 words) - 01:34, 22 August 2024
Camellia (cipher) (redirect from Camellia-256)
block cipher with a block size of 128 bits and key sizes of 128, 192 and 256 bits. It was jointly developed by Mitsubishi Electric and NTT of Japan. The...
18 KB (1,796 words) - 01:06, 17 September 2024
DES AES Blowfish Triple DES Serpent Twofish CAST-128 DES-X IDEA RC2 RC5 SEED Skipjack TEA XTEA CAST-256 RC4 Camellia Anubis KHAZAD Salsa20 FCrypt DragonFly...
82 KB (1,368 words) - 17:35, 6 March 2025
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
12 KB (1,222 words) - 11:18, 7 February 2025
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
13 KB (1,609 words) - 21:43, 19 February 2025
quantum-resistant cryptography. The suite includes: Advanced Encryption Standard with 256 bit keys Elliptic-curve Diffie–Hellman and Elliptic Curve Digital Signature...
9 KB (635 words) - 11:42, 28 November 2024
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
14 KB (1,797 words) - 08:53, 7 September 2024
Advanced Encryption Standard (AES) permits the use of 256-bit keys. Breaking a symmetric 256-bit key by brute-force requires 2128 times more computational...
21 KB (2,245 words) - 04:58, 22 February 2025
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
6 KB (749 words) - 15:35, 22 November 2023
longer than 448 bits. P[18] // P-array of 18 elements S[4][256] // S-boxes: 4 arrays of 256 elements function f(x): // Calculates a function f on a 32-bit...
18 KB (1,997 words) - 14:37, 12 December 2024
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
8 KB (934 words) - 10:33, 6 January 2025
SEAL 3.0, WAKE, WAKE-OFB, DESX (DES-XEX3), RC2, SAFER, 3-WAY, GOST, SHARK, CAST-128, and Square. In a 2007 ECRYPT workshop paper focusing on public key implementations...
19 KB (1,341 words) - 23:57, 18 November 2024
computer via OCR by readers. DES uses a 56-bit key, meaning that there are 256 possible keys under which a message can be encrypted. This is exactly 72...
10 KB (1,031 words) - 05:27, 28 February 2023
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
7 KB (958 words) - 10:15, 4 January 2025
MD-5, SHA-1, and SHA-2 family such as SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256 Cipher-block chaining (CBC) mode is an example of...
23 KB (3,307 words) - 14:54, 5 February 2025
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
6 KB (659 words) - 17:22, 19 June 2024
Adiantum Akelarre Anubis Ascon BaseKing BassOmatic BATON BEAR and LION CAST-256 Chiasmus CIKS-1 CIPHERUNICORN-A CIPHERUNICORN-E CLEFIA CMEA Cobra COCONUT98...
8 KB (843 words) - 15:52, 12 June 2024