Cipher System is a Swedish melodic death metal band from Tjörn. The band formed under the name Eternal Grief in 1995. They changed their name in 2001...
6 KB (249 words) - 23:27, 15 October 2023
Cryptanalysis (redirect from Cipher System Identification)
indicator systems allowed first Polish cryptographers and then the British cryptographers at Bletchley Park to break the Enigma cipher system. Similar...
44 KB (5,202 words) - 13:26, 19 August 2024
The Vigenère cipher (French pronunciation: [viʒnɛːʁ]) is a method of encrypting alphabetic text where each letter of the plaintext is encoded with a different...
44 KB (5,934 words) - 03:37, 19 August 2024
In cryptography, a cipher (or cypher) is an algorithm for performing encryption or decryption—a series of well-defined steps that can be followed as a...
17 KB (2,099 words) - 21:11, 28 July 2024
as in the simple substitution cipher and rather more complex Vigenère cipher systems then in use. The Playfair cipher is thus significantly harder to...
20 KB (2,503 words) - 16:11, 28 July 2024
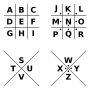
pigpen cipher (alternatively referred to as the masonic cipher, Freemason's cipher, Rosicrucian cipher, Napoleon cipher, and tic-tac-toe cipher) is a geometric...
10 KB (1,226 words) - 23:22, 25 June 2024
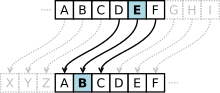
In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code, or Caesar shift, is one of the simplest and most widely...
19 KB (2,031 words) - 00:56, 12 August 2024
In cryptography, a product cipher combines two or more transformations in a manner intending that the resulting cipher is more secure than the individual...
2 KB (278 words) - 23:01, 22 April 2023
In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with...
30 KB (4,021 words) - 22:15, 14 July 2024
themselves. Transposition ciphers reorder units of plaintext (typically characters or groups of characters) according to a regular system to produce a ciphertext...
25 KB (3,604 words) - 03:23, 21 March 2024
Jefferson disk (redirect from Wheel cipher)
Jefferson disk, also called the Bazeries cylinder or wheel cypher, was a cipher system commonly attributed to Thomas Jefferson that uses a set of wheels or...
13 KB (1,595 words) - 07:21, 12 August 2024
Cipher System / By Night is an EP by the Swedish metal bands Cipher System and By Night. Released in 2004. "What If" - 3:30 "Receive, Retrieve and Escalate"...
2 KB (100 words) - 21:14, 24 May 2024
The Lorenz SZ40, SZ42a and SZ42b were German rotor stream cipher machines used by the German Army during World War II. They were developed by C. Lorenz...
34 KB (3,764 words) - 18:39, 13 April 2024
A cipher suite is a set of algorithms that help secure a network connection. Suites typically use Transport Layer Security (TLS) or its deprecated predecessor...
19 KB (2,358 words) - 22:21, 6 June 2024
In cryptography, the ADFGVX cipher was a manually applied field cipher used by the Imperial German Army during World War I. It was used to transmit messages...
13 KB (1,696 words) - 18:27, 12 February 2024
stream cipher is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream). In a stream cipher, each...
23 KB (2,213 words) - 15:26, 19 August 2024
The affine cipher is a type of monoalphabetic substitution cipher, where each letter in an alphabet is mapped to its numeric equivalent, encrypted using...
10 KB (1,143 words) - 22:04, 6 May 2024
Cryptography (redirect from Codes and ciphers)
Shannon's Maxim—'the enemy knows the system'. Different physical devices and aids have been used to assist with ciphers. One of the earliest may have been...
98 KB (10,713 words) - 13:13, 22 August 2024
Hill cipher is a polygraphic substitution cipher based on linear algebra. Invented by Lester S. Hill in 1929, it was the first polygraphic cipher in which...
13 KB (2,241 words) - 19:55, 25 April 2024
Voynich manuscript (category Undeciphered historical codes and ciphers)
"ee", "eee", among others) does suggest that its cipher system may make use of a "verbose cipher", where single letters in a plaintext get enciphered...
140 KB (13,826 words) - 02:05, 15 August 2024
United States Army Ordnance Corps. In 1817, he developed a progressive cipher system based on a 1790 design by Thomas Jefferson, establishing a method that...
2 KB (213 words) - 14:16, 23 July 2024
An autokey cipher (also known as the autoclave cipher) is a cipher that incorporates the message (the plaintext) into the key. The key is generated from...
9 KB (1,276 words) - 15:02, 26 January 2024
Siemens and Halske T52 (redirect from Siemens Cipher Machine)
teleprinter"), or Schlüsselfernschreibmaschine (SFM), was a World War II German cipher machine and teleprinter produced by the electrical engineering firm Siemens...
7 KB (918 words) - 13:26, 18 June 2024
Symmetric-key algorithm (redirect from Symmetric cipher)
use either stream ciphers or block ciphers. Stream ciphers encrypt the digits (typically bytes), or letters (in substitution ciphers) of a message one...
15 KB (1,544 words) - 02:53, 7 June 2024
Rotor machine (redirect from Rotor cipher machine)
In cryptography, a rotor machine is an electro-mechanical stream cipher device used for encrypting and decrypting messages. Rotor machines were the cryptographic...
17 KB (2,460 words) - 12:53, 17 April 2024
In cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. In contrast to modern...
15 KB (2,528 words) - 02:24, 15 June 2024
The cipher was designed to be suitable for both software and hardware implementations, from low-cost smart cards to high-speed network systems. It is...
18 KB (1,768 words) - 18:34, 29 October 2023
cryptography, a block cipher is a deterministic algorithm that operates on fixed-length groups of bits, called blocks. Block ciphers are the elementary building...
50 KB (6,475 words) - 03:59, 22 August 2024
History of cryptography (redirect from Unsolved ciphers)
Cryptography, the use of codes and ciphers to protect secrets, began thousands of years ago. Until recent decades, it has been the story of what might...
51 KB (6,699 words) - 22:35, 17 August 2024
Ciphertext (redirect from Cipher text)
result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it...
9 KB (1,139 words) - 01:27, 4 April 2024