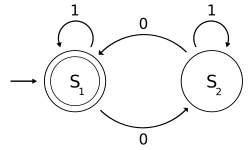
In cryptography, the clock was a method devised by Polish mathematician-cryptologist Jerzy Różycki, at the Polish General Staff's Cipher Bureau, to facilitate...
19 KB (2,730 words) - 11:31, 13 September 2022
need high quality random numbers, especially for cryptography. There are several similar ways clock drift can be used to build random number generators...
8 KB (1,073 words) - 02:12, 9 February 2025
In cryptography, a nonce is an arbitrary number that can be used just once in a cryptographic communication. It is often a random or pseudo-random number...
7 KB (881 words) - 16:27, 15 April 2025
Clifford Cocks • Clipper chip • Clock (cryptography) • Clock drift • CMVP • COCONUT98 • Codebook • Code (cryptography) • Code talker • Codress message...
67 KB (2,933 words) - 10:14, 4 January 2025
operation. Clock (cryptography), a method to facilitate decrypting German Enigma ciphers Clock (Apple), a bundled iPhone app Windows Clock, a bundled...
2 KB (274 words) - 21:16, 27 December 2024
Symmetric-key algorithm (redirect from Symmetric key cryptography)
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of...
15 KB (1,540 words) - 08:38, 29 March 2025
Network Time Protocol (redirect from NTP clock strata)
attack can be used to alter clocks on client computers and allow a number of attacks based on bypassing of cryptographic key expiration. Some of the services...
62 KB (6,428 words) - 17:05, 7 April 2025
Kerberos builds on symmetric-key cryptography and requires a trusted third party, and optionally may use public-key cryptography during certain phases of authentication...
27 KB (3,023 words) - 18:22, 15 April 2025
Timing attack (redirect from Constant-time cryptography)
In cryptography, a timing attack is a side-channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute...
13 KB (1,609 words) - 21:43, 19 February 2025
for use in cryptography. Random number generators have applications in gambling, statistical sampling, computer simulation, cryptography, completely...
36 KB (4,422 words) - 19:27, 29 March 2025
Encryption software (redirect from Cryptographic software)
Encryption software is software that uses cryptography to prevent unauthorized access to digital information. Cryptography is used to protect digital information...
10 KB (1,108 words) - 04:35, 19 October 2024
problems in the areas of Bioinformatics, Biomedical engineering and cryptography. It is an open source project licensed under the GPL. List of volunteer...
1 KB (101 words) - 06:55, 8 January 2025
(India), SCU13 and SCU14. The cryptographic element of each SLU was supplied by the RAF and was based on the TYPEX cryptographic machine and one-time pad systems...
78 KB (10,349 words) - 06:44, 3 April 2025
Challenge–response authentication (redirect from Challenge (Cryptography))
impractical to implement a true nonce, a strong cryptographically secure pseudorandom number generator and cryptographic hash function can generate challenges that...
11 KB (1,540 words) - 19:04, 12 December 2024
A5/1 (redirect from A5 (cryptography))
registers are clocked in a stop/go fashion using a majority rule. Each register has an associated clocking bit. At each cycle, the clocking bit of all three...
23 KB (2,725 words) - 00:35, 9 August 2024
procedure, which seemed reasonably secure to the Germans, was nonetheless a cryptographic malpractice, since the first insights into Enigma encryption could be...
10 KB (1,312 words) - 20:15, 27 February 2024
SHA-2 (category National Security Agency cryptography)
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published...
51 KB (4,987 words) - 11:53, 11 April 2025
Modular arithmetic (redirect from Clock arithmetic)
A familiar example of modular arithmetic is the hour hand on a 12-hour clock. If the hour hand points to 7 now, then 8 hours later it will point to 3...
29 KB (3,643 words) - 22:30, 9 April 2025
Theoretical computer science (section Cryptography)
computation, quantum computation, automata theory, information theory, cryptography, program semantics and verification, algorithmic game theory, machine...
42 KB (4,803 words) - 18:20, 30 January 2025
In cryptography, a key derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master...
13 KB (1,640 words) - 13:55, 21 February 2025
Julius Caesar in the 1st century BC. An early entry on the Timeline of cryptography. ROT13 can be referred by "Rotate13", "rotate by 13 places", hyphenated...
19 KB (2,090 words) - 10:02, 9 April 2025
Advanced Encryption Standard (category Cryptography)
Agency (NSA) for top secret information when used in an NSA approved cryptographic module. The Advanced Encryption Standard (AES) is defined in each of:...
50 KB (5,675 words) - 11:39, 17 March 2025
Stream cipher (category Cryptographic primitives)
seed value using digital shift registers. The seed value serves as the cryptographic key for decrypting the ciphertext stream. Stream ciphers represent a...
23 KB (2,213 words) - 15:26, 19 August 2024
Enigma machine (redirect from Enigma cryptography machine)
German Enigma messages starting from January 1933. Over time, the German cryptographic procedures improved, and the Cipher Bureau developed techniques and...
93 KB (11,256 words) - 10:43, 5 April 2025
Pinwheel may refer to: Pinwheel (toy), a spinning children's toy Pinwheel (cryptography), a device for producing a short pseudo-random sequence of bits Pinwheel...
1 KB (227 words) - 19:53, 20 January 2025
Edwards curve (category Elliptic curve cryptography)
finite fields is widely used in elliptic curve cryptography. Applications of Edwards curves to cryptography were developed by Daniel J. Bernstein and Tanja...
18 KB (3,666 words) - 10:45, 10 January 2025
Software token (category Cryptography)
primary architectures for software tokens: shared secret and public-key cryptography. For a shared secret, an administrator will typically generate a configuration...
5 KB (567 words) - 06:06, 22 December 2024
military use, a superiority in elevation over an opposing force Advantage (cryptography), a measure of the effectiveness of an enemy's code-breaking effort Advantage...
2 KB (294 words) - 20:51, 8 April 2025
letters can be assigned to the grid. The Pigpen cipher offers little cryptographic security. It differentiates itself from other simple monoalphabetic...
13 KB (1,673 words) - 02:22, 26 February 2025
Hardware random number generator (category Cryptography)
sequence of numbers are crucial to the success of the implementation: in cryptography and gambling machines. The major use for hardware random number generators...
28 KB (3,317 words) - 05:30, 18 January 2025