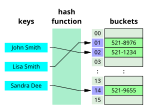
output. The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to...
49 KB (7,868 words) - 14:03, 13 July 2024
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle...
48 KB (6,228 words) - 08:01, 25 June 2024
checksum. Hash function security summary Secure Hash Algorithms NIST hash function competition Key derivation functions (category) "Hash functions". www.azillionmonkeys...
10 KB (280 words) - 10:21, 23 June 2024
In computer science, a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers, with no collisions...
24 KB (2,956 words) - 14:27, 22 July 2024
cryptography, Whirlpool (sometimes styled WHIRLPOOL) is a cryptographic hash function. It was designed by Vincent Rijmen (co-creator of the Advanced Encryption...
11 KB (1,054 words) - 03:57, 19 March 2024
BLAKE is a cryptographic hash function based on Daniel J. Bernstein's ChaCha stream cipher, but a permuted copy of the input block, XORed with round constants...
30 KB (2,848 words) - 08:36, 2 July 2024
The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S...
3 KB (464 words) - 13:15, 22 July 2024
The MD2 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1989. The algorithm is optimized for 8-bit computers....
9 KB (1,014 words) - 10:18, 12 July 2024
hash >> 6; } hash += hash << 3; hash ^= hash >> 11; hash += hash << 15; return hash; } Sample hash values for one_at_a_time hash function. one_at_a_time("a"...
7 KB (852 words) - 21:39, 4 May 2024
password, or a passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch...
13 KB (1,625 words) - 12:36, 12 July 2024
non-cryptographic hash functions (NCHFs) are hash functions intended for applications that do not need the rigorous security requirements of the cryptographic hash functions...
7 KB (801 words) - 21:59, 4 May 2024
is a non-cryptographic hash function created by Glenn Fowler, Landon Curt Noll, and Kiem-Phong Vo. The basis of the FNV hash algorithm was taken from...
14 KB (1,410 words) - 09:11, 25 March 2024
is hashed and the resulting hash indicates where the corresponding value is stored. Most hash table designs employ an imperfect hash function. Hash collisions...
52 KB (5,814 words) - 03:48, 27 July 2024
HMAC (redirect from Keyed-Hashing Message Authentication)
type of message authentication code (MAC) involving a cryptographic hash function and a secret cryptographic key. As with any MAC, it may be used to simultaneously...
18 KB (2,305 words) - 16:02, 27 July 2024
cryptographic hash function designed by Ross Anderson and Eli Biham in 1995 for efficiency on 64-bit platforms. The size of a Tiger hash value is 192 bits...
9 KB (910 words) - 14:47, 30 September 2023
Skein is a cryptographic hash function and one of five finalists in the NIST hash function competition. Entered as a candidate to become the SHA-3 standard...
9 KB (836 words) - 02:45, 11 July 2024
universal hashing (in a randomized algorithm or data structure) refers to selecting a hash function at random from a family of hash functions with a certain...
29 KB (4,875 words) - 10:36, 18 April 2024
to compute multiple hash functions, but a related version of MinHash scheme avoids this penalty by using only a single hash function and uses it to select...
25 KB (3,184 words) - 23:20, 4 December 2023
cryptographic hash functions. Note that not all entries may be up to date. For a summary of other hash function parameters, see comparison of cryptographic hash functions...
17 KB (1,055 words) - 12:18, 2 March 2023
Rainbow table (redirect from Reduction function)
cryptographic hash function, usually for cracking password hashes. Passwords are typically stored not in plain text form, but as hash values. If such...
24 KB (3,446 words) - 08:05, 23 June 2024
derived from a hash function which takes a data input and returns a fixed length of bits. Although hash algorithms, especially cryptographic hash algorithms...
12 KB (1,463 words) - 03:47, 20 June 2024
hash function security/cryptanalysis can be found at hash function security summary. Basic general information about the cryptographic hash functions:...
16 KB (785 words) - 15:03, 26 January 2024
ShangMi 3 (SM3) is a cryptographic hash function used in the Chinese National Standard. It was published by the National Cryptography Administration (Chinese:...
3 KB (287 words) - 17:06, 16 November 2023
Salt (cryptography) (redirect from Salted hash)
cryptography, a salt is random data fed as an additional input to a one-way function that hashes data, a password or passphrase. Salting helps defend against attacks...
13 KB (1,482 words) - 20:08, 22 May 2024
Look up hash in Wiktionary, the free dictionary. Hash, hashes, hash mark, or hashing may refer to: Hash (food), a coarse mixture of ingredients, often...
2 KB (283 words) - 21:49, 5 July 2024
Preimage attack (redirect from Hash function preimage)
attack on cryptographic hash functions tries to find a message that has a specific hash value. A cryptographic hash function should resist attacks on...
7 KB (895 words) - 15:44, 13 April 2024
In computer science, locality-sensitive hashing (LSH) is a fuzzy hashing technique that hashes similar input items into the same "buckets" with high probability...
30 KB (4,013 words) - 13:50, 25 June 2024
JH is a cryptographic hash function submitted to the NIST hash function competition by Hongjun Wu. Though chosen as one of the five finalists of the competition...
4 KB (355 words) - 02:36, 11 January 2024
multi-block-length hash function based on block ciphers" and typically achieves (asymptotic) rates between 1 and 2 independent of the hash size (only with...
24 KB (3,977 words) - 03:22, 7 June 2024