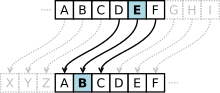
Cryptography (redirect from CryptologY)
Cryptography, or cryptology (from Ancient Greek: κρυπτός, romanized: kryptós "hidden, secret"; and γράφειν graphein, "to write", or -λογία -logia, "study"...
100 KB (10,952 words) - 16:31, 9 November 2024
The Journal of Cryptology (ISSN 0933-2790) is a scientific journal in the field of cryptology and cryptography. The journal is published quarterly by the...
1 KB (56 words) - 18:22, 29 April 2024
International Association for Cryptologic Research (redirect from International Cryptology Conference)
(IACR) is a non-profit scientific organization that furthers research in cryptology and related fields. The IACR was organized at the initiative of David...
26 KB (1,420 words) - 15:07, 26 January 2024
Cryptology is an album by jazz saxophonist David S. Ware, recorded in 1994 and released by Homestead Records. In fall 1992, Steven Joerg took over as Homestead...
4 KB (334 words) - 13:32, 21 April 2024
Cryptology Research Society of India (CRSI) is a scientific organisation that supports research in India on cryptography, data security, and related fields...
7 KB (396 words) - 22:26, 3 November 2024
Key (cryptography) (redirect from Key (cryptology))
A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic...
13 KB (1,506 words) - 20:06, 18 October 2024
with Errors Problem". Cryptology ePrint Archive. Peikert, Chris (2014-01-01). "Lattice Cryptography for the Internet". Cryptology ePrint Archive. Singh...
62 KB (6,467 words) - 14:01, 8 November 2024
The Cryptology ePrint Archive is an electronic archive (eprint) of new results in the field of cryptography, maintained by the International Association...
1 KB (67 words) - 22:37, 27 May 2024
Retrieved 2024-10-20. Luciano, Dennis; Gordon Prichett (January 1987). "Cryptology: From Caesar Ciphers to Public-Key Cryptosystems". The College Mathematics...
19 KB (2,058 words) - 14:38, 20 October 2024
Quantum cryptography (redirect from Quantum cryptology)
Charles H.; et al. (1992). "Experimental quantum cryptography". Journal of Cryptology. 5 (1): 3–28. doi:10.1007/bf00191318. S2CID 206771454. Wiesner, Stephen...
81 KB (9,042 words) - 15:37, 28 October 2024
Dr. ir. Marc Stevens is a cryptology researcher most known for his work on cryptographic hash collisions and for the creation of the chosen-prefix hash...
4 KB (279 words) - 20:34, 13 May 2024
Texas Cryptologic Center (redirect from Texas Cryptology Center)
The NSA/CSS Texas Cryptologic Center (TCC), also known as the Texas Cryptology Center, Texas Cryptographic Center or NSA Texas, is a satellite campus at...
9 KB (460 words) - 00:30, 22 August 2023
Chaotic cryptology is the application of mathematical chaos theory to the practice of cryptography, the study or techniques used to privately and securely...
15 KB (1,794 words) - 19:35, 6 November 2024
Plugboard (redirect from Commutator (cryptology))
A plugboard or control panel (the term used depends on the application area) is an array of jacks or sockets (often called hubs) into which patch cords...
19 KB (2,672 words) - 20:22, 25 August 2024
for NSA cryptanalysts. Friedman, William F., Six Lectures on Cryptology, National Cryptology School, U.S. National Security Agency, 1965, declassified 1977...
28 KB (3,604 words) - 08:21, 14 October 2024
Lucks, Stefan (2004). "Design Principles for Iterated Hash Functions". Cryptology ePrint Archive. Report 2004/253. Archived from the original on 2017-05-21...
48 KB (6,237 words) - 00:38, 5 November 2024
Clock (cryptography) (redirect from Clock (cryptology))
In cryptography, the clock was a method devised by Polish mathematician-cryptologist Jerzy Różycki, at the Polish General Staff's Cipher Bureau, to facilitate...
19 KB (2,730 words) - 11:31, 13 September 2022
Fanbao Liu; Dengguo Feng (2013). "Fast Collision Attack on MD5" (PDF). Cryptology ePrint Archive. Archived (PDF) from the original on 2 February 2021. Retrieved...
47 KB (4,712 words) - 21:30, 30 August 2024
Yuliang (ed.). Advances in Cryptology – ASIACRYPT 2002: 8th International Conference on the Theory and Application of Cryptology and Information Security...
49 KB (5,566 words) - 15:08, 9 November 2024
Hurt. During this period Elizebeth Friedman continued her own work in cryptology, and became famous in a number of trials involving rum-runners and the...
26 KB (2,837 words) - 23:49, 24 October 2024
National Institute of Cryptology Research and Development (NICRD) is an Indian national-level research centre for cryptologic education and research. The...
3 KB (127 words) - 01:29, 13 September 2024
The grill method (Polish: metoda rusztu), in cryptology, was a method used chiefly early on, before the advent of the cyclometer, by the mathematician-cryptologists...
64 KB (10,533 words) - 16:40, 27 October 2024
’99: Proceedings of the 19th Annual International Cryptology Conference on Advances in Cryptology, pages 288–304, London, UK, 1999. Springer-Verlag....
23 KB (2,793 words) - 23:26, 17 September 2024
for Preimages: Attacks on Skein-512 and the SHA-2 family" (PDF). IACR Cryptology ePrint Archive. 2011 (286). Archived (PDF) from the original on 2022-02-15...
51 KB (4,970 words) - 22:27, 11 November 2024
Dunkelman (20 July 2007). "A Framework for Iterative Hash Functions – HAIFA". Cryptology ePrint Archive. Jean-Philippe Aumasson, Samuel Neves, Zooko Wilcox-O’Hearn...
10 KB (280 words) - 12:41, 17 October 2024
doi:10.1080/0161-117891853270. Thomas R. Johnson (2009-12-18). "American Cryptology during the Cold War, 1945-1989.Book III: Retrenchment and Reform, 1972-1980...
59 KB (6,543 words) - 16:59, 10 November 2024
Hacking: The Art of Exploitation (section Cryptology)
sniffing, connection hijacking, denial of service, and port scanning. The cryptology section of Hacking covers basic information theory, in addition to symmetric...
7 KB (698 words) - 09:02, 23 August 2024
Polish Enigma double (redirect from Polish copies of Enigma (cryptology))
A Polish Enigma "double" was a machine produced by the Polish Biuro Szyfrów that replicated the German Enigma machine. The Enigma double was one result...
8 KB (866 words) - 13:16, 26 May 2024
Hovav (eds.). The First Collision for Full SHA-1 (PDF). Advances in Cryptology – CRYPTO 2017. Lecture Notes in Computer Science. Vol. 10401. Springer...
50 KB (5,744 words) - 19:28, 20 October 2024
SIGABA F.L. Bauer (9 March 2013). Decrypted Secrets: Methods and Maxims of Cryptology. Springer Science & Business Media. pp. 133–. ISBN 978-3-662-03452-1....
3 KB (237 words) - 05:32, 10 January 2022