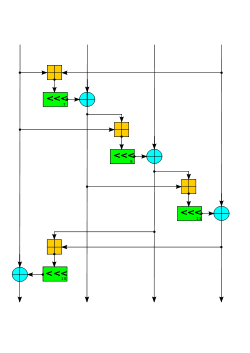
ChaCha20-Poly1305 is an authenticated encryption with associated data (AEAD) algorithm, that combines the ChaCha20 stream cipher with the Poly1305 message...
13 KB (1,506 words) - 14:10, 12 October 2024
Poly1305 is a universal hash family designed by Daniel J. Bernstein in 2002 for use in cryptography. As with any universal hash family, Poly1305 can be...
17 KB (2,513 words) - 19:16, 19 February 2025
construction combining both algorithms, which is called ChaCha20-Poly1305. ChaCha20 and Poly1305 are now used in the QUIC protocol, which replaces SPDY and...
31 KB (3,577 words) - 20:06, 24 October 2024
AES-192-GCM; AES-128-GCM; AES-256-CBC; AES-192-CBC; AES-128-CBC; ChaCha20-Poly1305; ARIA-256-CBC; CAMELLIA-256-CBC). You cannot use encryption at all (this...
7 KB (696 words) - 18:37, 11 April 2025
cryptanalytic advantage. Google selected ChaCha20 along with Bernstein's Poly1305 message authentication code for use in TLS, which is widely used for Internet...
22 KB (1,973 words) - 03:58, 16 March 2025
PMAC). However many of the fastest MAC algorithms, like UMAC-VMAC and Poly1305-AES, are constructed based on universal hashing. Intrinsically keyed hash...
16 KB (1,918 words) - 17:55, 22 January 2025
encourage design of authenticated encryption modes. In 2015, ChaCha20-Poly1305 is added as an alternative AE construction to GCM in IETF protocols. Authenticated...
19 KB (2,104 words) - 04:46, 19 March 2025
different cryptographic algorithms: Ciphers AES, Blowfish, Camellia, ChaCha20, Poly1305, SEED, CAST-128, DES, IDEA, RC2, RC4, RC5, Triple DES, GOST 28147-89, SM4...
64 KB (5,479 words) - 01:17, 7 April 2025
revision in 2013, there are several updates such as addition of ChaCha20-Poly1305, EdDSA and SHA-3, move of Triple DES to Monitored list, and deletion of...
8 KB (974 words) - 00:22, 19 August 2023
encryption. Key agreement happens via X25519; encryption is done by Salsa20-Poly1305. crypto_scalarmult, scalar multiplication on X25519. This function can...
10 KB (745 words) - 15:07, 3 March 2025
for key exchange, EdDSA for signatures, as well as XSalsa20-Poly1305 or XChaCha20-Poly1305 for authenticated encryption.: §11 As of 2023, there are no...
10 KB (943 words) - 13:35, 4 July 2024
following: Curve25519 for key exchange ChaCha20 for symmetric encryption Poly1305 for message authentication codes SipHash24 for hashtable keys BLAKE2s for...
23 KB (2,191 words) - 16:14, 25 March 2025
performance-sensitive devices. Specialized hardware accelerators for ChaCha20-Poly1305 are less complex compared to AES accelerators. According to the authors'...
23 KB (3,051 words) - 20:21, 24 March 2025
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
24 KB (3,485 words) - 19:40, 2 April 2025
IETF ChaCha20 stream cipher (256-bit key) and authenticated with the IETF Poly1305 authenticator. Outline is free and open-source, licensed under the Apache...
7 KB (620 words) - 13:16, 29 December 2024
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
18 KB (2,314 words) - 18:51, 16 April 2025
NH, 256-bit Advanced Encryption Standard (AES-256), ChaCha12/ChaCha20, Poly1305 for the four elements. HPolyC is an earlier variant which does not use...
4 KB (317 words) - 21:37, 11 February 2025
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
3 KB (464 words) - 07:05, 4 October 2024
WireGuard utilizes the Curve25519 protocol for key exchange and ChaCha20-Poly1305 for encryption and message authentication, but also includes the ability...
33 KB (3,659 words) - 09:29, 14 April 2025
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
13 KB (1,337 words) - 20:06, 7 March 2025
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
13 KB (1,533 words) - 12:18, 19 January 2025
Camellia, CAST5, CAST6, Serpent, Twofish, MORUS-1280, and other primitives: Poly1305, SHA-1, SHA-256, SHA-512, ChaCha20. liboqs utilizes AVX, AVX2, and AVX-512...
55 KB (4,557 words) - 23:41, 2 April 2025
HC-128, ChaCha20, MD2, MD4, MD5, SHA-1, SHA-2, SHA-3, BLAKE2, RIPEMD-160, Poly1305, Random Number Generation, Large Integer support, base 16/64 encoding/decoding...
20 KB (1,039 words) - 13:26, 3 February 2025
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
27 KB (2,858 words) - 22:16, 9 April 2025
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
15 KB (1,790 words) - 06:31, 3 March 2025
features: the ChaCha and Poly1305 algorithm, the Brainpool and ANSSI elliptic curves, and the AES-GCM and ChaCha20-Poly1305 AEAD modes. Later versions...
27 KB (2,287 words) - 21:45, 5 April 2025
Developments since then have included the addition of ciphers (e.g., ChaCha20-Poly1305 in 6.5 of January 2014), cutting the dependency on OpenSSL (6.7, October...
26 KB (2,781 words) - 08:09, 9 March 2025
deprecated RC4, 3DES, DES) for symmetric encryption. AES-GCM and ChaCha20-Poly1305 for AEAD encryption. SHA (and deprecated MD5) for key fingerprint. In 1998...
41 KB (4,503 words) - 17:19, 16 April 2025
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
51 KB (4,982 words) - 17:12, 16 April 2025
DAA GMAC HMAC NMAC OMAC/CMAC PMAC Poly1305 SipHash UMAC VMAC Authenticated encryption modes CCM ChaCha20-Poly1305 CWC EAX GCM IAPM OCB Attacks Collision...
47 KB (4,724 words) - 12:29, 2 April 2025