A hash chain is the successive application of a cryptographic hash function to a piece of data. In computer security, a hash chain is a method used to...
7 KB (1,005 words) - 23:12, 10 May 2024
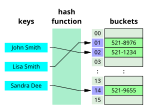
is hashed and the resulting hash indicates where the corresponding value is stored. A map implemented by a hash table is called a hash map. Most hash table...
52 KB (5,869 words) - 19:02, 24 August 2024
Merkle tree (redirect from Tiger-Tree Hash)
generalization of a hash list and a hash chain. Demonstrating that a leaf node is a part of a given binary hash tree requires computing a number of hashes proportional...
15 KB (1,788 words) - 20:42, 10 September 2024
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle...
48 KB (6,228 words) - 12:47, 4 September 2024
Look up hash in Wiktionary, the free dictionary. Hash, hashes, hash mark, or hashing may refer to: Hash (food), a coarse mixture of ingredients, often...
2 KB (283 words) - 21:49, 5 July 2024
Rainbow table (category Cryptographic hash functions)
cryptographic hash function, usually for cracking password hashes. Passwords are typically stored not in plain text form, but as hash values. If such...
24 KB (3,455 words) - 14:45, 12 September 2024
Bittorrent Hash tree Hash table Hash chain Ed2k: URI scheme, which uses an MD4 top hash of an MD4 hash list to uniquely identify a file Cryptographic hash function...
3 KB (457 words) - 15:59, 13 May 2024
output. The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to...
50 KB (7,536 words) - 08:38, 18 September 2024
computer science, a hash collision or hash clash is when two distinct pieces of data in a hash table share the same hash value. The hash value in this case...
9 KB (1,130 words) - 16:51, 9 August 2024
One-time password (section Hash chains)
pseudorandomness or randomness to generate a shared key or seed, and cryptographic hash functions, which can be used to derive a value but are hard to reverse and...
26 KB (3,542 words) - 22:09, 16 September 2024
Hash oil or cannabis oil is an oleoresin obtained by the extraction of cannabis or hashish. It is a cannabis concentrate containing many of its resins...
34 KB (3,454 words) - 14:03, 25 August 2024
authenticated data structure include: Linear hash chain Merkle tree (binary hash tree) Skip list The simplest linear hash chain-based time-stamping scheme is illustrated...
13 KB (1,661 words) - 03:20, 21 August 2023
Salt (cryptography) (redirect from Salted hash)
passwords to their hashes, or it might do something more complex, like store the start and end points of a set of precomputed hash chains. In either case...
13 KB (1,533 words) - 16:00, 29 August 2024
Key stretching (section Hash-based)
password hashes.) Key derivation function – often uses key stretching PBKDF2, bcrypt, scrypt, Argon2 – widely used key stretching algorithms Hash chain Kelsey...
14 KB (1,817 words) - 16:14, 17 July 2024
overview of hash function security/cryptanalysis can be found at hash function security summary. Basic general information about the cryptographic hash functions:...
16 KB (806 words) - 20:08, 6 August 2024
Hash House a go go is an American restaurant chain founded and headquartered in San Diego, California, in July 2000. Known for large portions of breakfast...
4 KB (259 words) - 20:41, 5 May 2024
Look up hash house in Wiktionary, the free dictionary. Hash House may refer to: Hash House a go go, a restaurant chain Hash House Bikers, an international...
426 bytes (101 words) - 20:36, 8 March 2024
"Maher-shalal-hash-baz" was the second prophetic name mentioned in Isaiah chapter 8–9. The name is mentioned twice in the Hebrew Bible, both times in the...
4 KB (411 words) - 08:41, 1 February 2024
S/KEY is compromised. A cryptographic hash function H is applied n times to W, thereby producing a hash chain of n one-time passwords. The passwords...
10 KB (1,301 words) - 06:02, 26 March 2024
BLAKE is a cryptographic hash function based on Daniel J. Bernstein's ChaCha stream cipher, but a permuted copy of the input block, XORed with round constants...
30 KB (2,848 words) - 05:59, 18 August 2024
any method that ensures unpredictability and uniqueness (e.g. using a hash chain of random seed). This is called a anti-forgery token in ASP.NET. The attacker...
30 KB (3,749 words) - 16:12, 5 September 2024
In computer science, tabulation hashing is a method for constructing universal families of hash functions by combining table lookup with exclusive or...
19 KB (2,762 words) - 13:24, 2 September 2024
Coalesced hashing, also called coalesced chaining, is a strategy of collision resolution in a hash table that forms a hybrid of separate chaining and open...
7 KB (918 words) - 14:13, 18 March 2024
Institute of Technology (BS) Brandeis University (MA, PhD) Known for LaTeX Hash chain (S/KEY) Sequential consistency Lamport's bakery algorithm Byzantine fault...
17 KB (1,543 words) - 17:21, 4 September 2024
are different algorithms that can be used to build a hash calendar and extract a relevant hash chain per second. The easiest is to imagine the calendar...
5 KB (621 words) - 16:45, 8 June 2024
Fusion tree (section Fusion hashing)
tree representing each hash chain. In hash chaining, in a hash table with a constant load factor, the average size of a chain is constant, but additionally...
18 KB (2,434 words) - 10:29, 22 July 2024
Merkle–Damgård construction (redirect from Merkle-Damgard hash function)
Merkle–Damgård construction or Merkle–Damgård hash function is a method of building collision-resistant cryptographic hash functions from collision-resistant one-way...
15 KB (1,904 words) - 00:58, 24 August 2024
Key derivation function (redirect from Password hash)
passphrase using a pseudorandom function (which typically uses a cryptographic hash function or block cipher). KDFs can be used to stretch keys into longer keys...
13 KB (1,645 words) - 14:47, 4 August 2024
creating ordinary public-key digital signatures, such as RSA. Clients use hash chain based authentication to send their messages to a signature server in an...
9 KB (1,187 words) - 04:24, 5 July 2023
mechanism where transactions are batched into blocks and chained together using a linked list of hash pointers (blockchain). Any server can produce a block...
8 KB (975 words) - 02:35, 2 August 2024