Honeypot (computing) (redirect from Honeynet)
maintained for each honeypot, which can be exorbitantly expensive. Example: Honeynet. Low-interaction honeypots simulate only the services frequently requested...
28 KB (3,253 words) - 22:26, 8 November 2024
The Honeynet Project is an international cybersecurity non-profit research organization that investigates new cyber attacks and develops open-source tools...
6 KB (407 words) - 18:06, 19 August 2024
Exploits of Hackers, Intruders and Deceivers (2005) ISBN 978-0471782667 Honeynet.org - Know Your Enemy (Essay about script kiddies) preserved at Internet...
5 KB (542 words) - 22:21, 31 January 2025
technical papers about network security. He is a founding member of the Honeynet Project and was Vice President of Computer Professionals for Social Responsibility...
6 KB (444 words) - 12:02, 11 September 2024
their attention from the data on the real server. Similar to a honeypot, a honeynet is a network set up with intentional vulnerabilities. Its purpose is also...
13 KB (1,651 words) - 10:15, 4 March 2025
Wayback Machine, Damballa, 8 June 2009. "Uses of botnets | The Honeynet Project". www.honeynet.org. Archived from the original on 20 March 2019. Retrieved...
58 KB (5,434 words) - 04:21, 15 February 2025
M. A. Know Your Enemy: Malicious Web Servers. The Honeynet Project. 2007. (available at honeynet.org) Seifert, C., Welch, I. and Komisarczuk, P. HoneyC:...
19 KB (2,601 words) - 22:56, 8 November 2024
by the security researchers William Salusky and Robert Danford of The Honeynet Project in 2007; the following year, they released a systematic study of...
15 KB (1,660 words) - 03:59, 17 December 2023
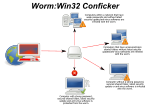
next reboot. On 27 March 2009, Felix Leder and Tillmann Werner from the Honeynet Project discovered that Conficker-infected hosts have a detectable signature...
59 KB (4,807 words) - 19:11, 14 January 2025
many network security books and web sites. He is a founding member of the Honeynet Project and Vice President of Computer Professionals for Social Responsibility...
55 KB (5,959 words) - 17:27, 22 January 2025
street Honeytokens and honeypots for web ID and IH White Paper: "Honeypot, Honeynet, Honeytoken: Terminological issues" Abdel-Basset, Mohamed; Gamal, Abduallah;...
4 KB (469 words) - 01:38, 22 December 2024
representations governing the NSD advisory panel at a national level include the HoneyNet India Chapter, Microsoft India and the country's oldest security conference...
8 KB (812 words) - 07:59, 22 November 2024
member of IMPACT. Since 2014, work has been underway to integrate into the HoneyNet Project. The activities of CERT-UA are envisaged by the Law of Ukraine...
6 KB (462 words) - 18:32, 3 June 2024
New Year's holidays bridging 2007–2008, the researchers of the German Honeynet Project reported that the Storm botnet may have increased in size by up...
46 KB (4,551 words) - 16:19, 6 November 2024
by the enemy are simply discarded or disconnected from the IoMT, and honeynets that mislead enemy eavesdroppers. Since adversary forces are expected...
38 KB (4,469 words) - 22:09, 25 November 2024