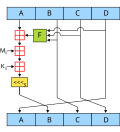
In cryptography, MDC-2 (Modification Detection Code 2, sometimes called Meyer–Schilling,[citation needed] standardized in ISO 10118-2) is a cryptographic...
4 KB (641 words) - 13:30, 4 October 2024
Metropolitan Detention Center, Brooklyn (redirect from Brooklyn MDC)
The Metropolitan Detention Center, Brooklyn (MDC Brooklyn) is a United States federal administrative detention facility in the Sunset Park neighborhood...
44 KB (2,546 words) - 10:54, 1 October 2024
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published...
51 KB (4,970 words) - 12:36, 1 October 2024
MDC is an American punk rock band formed in 1979 in Austin, Texas, subsequently based in San Francisco, and currently Portland, Oregon. Among the first...
21 KB (2,323 words) - 23:34, 9 May 2024
One-way compression function (redirect from MDC-4)
and MDC-2/Meyer–Schilling, MDC-4, Hirose (double-block-length compression functions). These methods are described in detail further down. (MDC-2 is also...
24 KB (3,977 words) - 03:22, 7 June 2024
cryptography, PBKDF1 and PBKDF2 (Password-Based Key Derivation Function 1 and 2) are key derivation functions with a sliding computational cost, used to reduce...
13 KB (1,341 words) - 15:37, 30 May 2024
nodes under each node. Usually, a cryptographic hash function such as SHA-2 is used for the hashing. If the hash tree only needs to protect against unintentional...
15 KB (1,788 words) - 20:42, 10 September 2024
CubeHash ECOH FSB Fugue GOST HAS-160 HAVAL Kupyna LSH Lane MASH-1 MASH-2 MD2 MD4 MD6 MDC-2 N-hash RIPEMD RadioGatún SIMD SM3 SWIFFT Shabal Snefru Streebog Tiger...
13 KB (1,533 words) - 16:00, 29 August 2024
standard was no longer approved for most cryptographic uses after 2010. SHA-2: A family of two similar hash functions, with different block sizes, known...
3 KB (464 words) - 07:05, 4 October 2024
CubeHash ECOH FSB Fugue GOST HAS-160 HAVAL Kupyna LSH Lane MASH-1 MASH-2 MD2 MD4 MD6 MDC-2 N-hash RIPEMD RadioGatún SIMD SM3 SWIFFT Shabal Snefru Streebog Tiger...
5 KB (568 words) - 17:23, 14 December 2023
Cryptographic hash function (section SHA-2)
output result (hash value) for a random input string ("message") is 2 − n {\displaystyle 2^{-n}} (as for any good hash), so the hash value can be used as a...
48 KB (6,237 words) - 11:39, 3 October 2024
and 96-bit nonce) and a variant of the original Poly1305 (authenticating 2 strings) being combined in an IETF draft to be used in TLS and DTLS, and chosen...
13 KB (1,511 words) - 08:51, 12 September 2024
CubeHash ECOH FSB Fugue GOST HAS-160 HAVAL Kupyna LSH Lane MASH-1 MASH-2 MD2 MD4 MD6 MDC-2 N-hash RIPEMD RadioGatún SIMD SM3 SWIFFT Shabal Snefru Streebog Tiger...
2 KB (102 words) - 08:19, 12 July 2024
which differs from RFC 4648 Base64 encoding. $2$ (1999) The original bcrypt specification defined a prefix of $2$. This follows the Modular Crypt Format format...
26 KB (2,753 words) - 08:57, 25 September 2024
Movement for Democratic Change – Tsvangirai (redirect from MDC Tsvangirai)
The Movement for Democratic Change – Tsvangirai (MDC–T) is a centre-left political party and was the main opposition party in the House of Assembly of...
24 KB (2,041 words) - 01:45, 27 September 2024
represent the reduction functions, a rainbow appears in the rainbow table. Figure 2 of Oechslin's paper contains a black-and-white graphic that illustrates how...
24 KB (3,488 words) - 11:19, 3 October 2024
key prior to communication. Any cryptographic hash function, such as SHA-2 or SHA-3, may be used in the calculation of an HMAC; the resulting MAC algorithm...
18 KB (2,335 words) - 00:41, 4 October 2024
a Creative Commons CC0 license (i.e. public domain) or the Apache License 2.0, and provides three related versions: Argon2d maximizes resistance to GPU...
14 KB (1,491 words) - 06:28, 21 August 2024
and most of SHA-2 that are based on the Merkle–Damgård construction are susceptible to this kind of attack. Truncated versions of SHA-2, including SHA-384...
7 KB (1,046 words) - 12:26, 6 June 2024
Practical Embedded Security, Elsevier, pp. 83–114, doi:10.1016/b978-075068215-2.50006-9, ISBN 9780750682152, retrieved 2021-12-08 Schneier, Bruce. "Cryptanalysis...
9 KB (1,130 words) - 16:51, 9 August 2024
a lower limit on the energy required to perform a computation of kT · ln 2 per bit erased in a computation, where T is the temperature of the computing...
21 KB (2,238 words) - 08:30, 28 September 2024
for the next message is insecure (for example, this method was used by SSL 2.0). If an attacker knows the IV (or the previous block of ciphertext) before...
52 KB (5,878 words) - 15:11, 20 September 2024
CubeHash ECOH FSB Fugue GOST HAS-160 HAVAL Kupyna LSH Lane MASH-1 MASH-2 MD2 MD4 MD6 MDC-2 N-hash RIPEMD RadioGatún SIMD SM3 SWIFFT Shabal Snefru Streebog Tiger...
3 KB (254 words) - 01:08, 11 October 2023
CubeHash ECOH FSB Fugue GOST HAS-160 HAVAL Kupyna LSH Lane MASH-1 MASH-2 MD2 MD4 MD6 MDC-2 N-hash RIPEMD RadioGatún SIMD SM3 SWIFFT Shabal Snefru Streebog Tiger...
8 KB (840 words) - 12:10, 18 February 2024
Crypto++ benchmarks, AES CCM requires 28.6 cycles per byte on an Intel Core 2 processor in 32-bit mode. Notable inefficiencies: CCM is not an "on-line"...
8 KB (924 words) - 10:55, 17 July 2024
Deriving a key from a password is as specified in [RFC1320] and [FIPS46-2]. Bert den Boer, Antoon Bosselaers (1991). "An Attack on the Last Two Rounds...
8 KB (837 words) - 01:10, 7 August 2024
is necessary. While RIPEMD functions are less popular than SHA-1 and SHA-2, they are used, among others, in Bitcoin and other cryptocurrencies based...
9 KB (857 words) - 20:38, 29 May 2024
approved algorithms: "Annex A: Approved Security Functions for FIPS PUB 140-2, Security Requirements for Cryptographic Modules" (PDF). National Institute...
24 KB (2,850 words) - 04:01, 30 September 2024
the number of finalization rounds. The recommended parameters are SipHash-2-4 for best performance, and SipHash-4-8 for conservative security. A few languages...
14 KB (1,342 words) - 05:08, 21 August 2024
Movement for Democratic Change – Ncube (redirect from MDC Mutambara)
Change – Mutambara (MDC–M) in contrast to the larger Movement for Democratic Change – Tsvangirai (MDC–T). The MDC–N and the MDC–T operated as separate...
9 KB (753 words) - 15:15, 21 June 2024