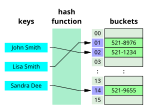
Pearson hashing is a non-cryptographic hash function designed for fast execution on processors with 8-bit registers. Given an input consisting of any...
4 KB (511 words) - 17:23, 17 December 2024
Bloom filter Consistent hashing Distributed hash table Extendible hashing Hash array mapped trie Lazy deletion Pearson hashing PhotoDNA Rabin–Karp string...
52 KB (5,874 words) - 13:50, 1 January 2025
a checksum. Hash function security summary Secure Hash Algorithms NIST hash function competition Key derivation functions (category) "Hash functions"....
10 KB (280 words) - 12:41, 17 October 2024
Merkle–Damgård construction N-Hash Negative-acknowledge character One-way compression function Parity bit Pearson hashing Perfect code Quantum fingerprinting...
3 KB (9 words) - 23:09, 3 June 2023
Hashish (redirect from Finger hash)
Hashish (/həˈʃiːʃ/ ; from Arabic ḥašiš 'hay'), usually abbreviated as hash, is a compressed form of powdered marijuana. As a psychoactive substance, it...
38 KB (4,323 words) - 12:24, 2 January 2025
Fowler–Noll–Vo hash function: fast with low collision rate Pearson hashing: computes 8-bit value only, optimized for 8-bit computers Zobrist hashing: used in...
71 KB (7,830 words) - 10:14, 6 January 2025
pattern element P-complete PCP theorem Peano curve Pearson's hashing perfect binary tree perfect hashing perfect k-ary tree perfect matching perfect shuffle...
35 KB (3,134 words) - 15:35, 20 December 2024
Key stretching (section Hash-based)
straight SHA-1 hash would be able to try 300,000÷216 ≈ 4.578 keys/second.[citation needed] Similarly, modern consumer GPUs can speed up hashing considerably...
14 KB (1,817 words) - 01:01, 24 December 2024
algorithm Cryptographic hash function Hash collision List of hash functions Comparison of cryptographic hash functions Hash-based cryptography SHA-1...
19 KB (1,781 words) - 14:01, 4 September 2024
partitions, VeraCrypt uses 500,000 iterations by default regardless of the hashing algorithm chosen (which is customizable by user to be as low as 16,000)...
37 KB (3,218 words) - 10:14, 10 December 2024
2021-11-16. Baden-Powell, Robert (1908). Scouting for Boys (PDF). London: Pearson. p. 76. ISBN 0-665-98794-3. Barnes, Lovisa Ellen (1890). How to Become...
9 KB (1,009 words) - 19:48, 14 December 2024
actual events, it also has a speculative element. In 2003, author John Pearson, while researching a book about the former Clermont Club, becomes interested...
11 KB (1,247 words) - 13:18, 1 January 2025
diffusion. These concepts are also important in the design of cryptographic hash functions, and pseudorandom number generators, where decorrelation of the...
12 KB (1,496 words) - 18:05, 29 July 2024
curve scheduling Hilbert R-tree Locality of reference Locality-sensitive hashing Moore curve Murray polygon Sierpiński curve List of fractals by Hausdorff...
11 KB (1,236 words) - 10:14, 25 September 2024
passes it to Danny for his wife. Jen finds the other woman, Nora (Andrea C. Pearson), hiding in Charlie's wardrobe. Charlie suggests they all continue dating...
185 KB (3,335 words) - 18:24, 4 January 2025
MIRC scripting language (section Hash tables)
bot) Peter Szor (2005). The Art of Computer Virus Research and Defense. Pearson Education. Ch. 3.7.7. David Harley, Robert S. Vibert (2007). AVIEN Malware...
14 KB (1,476 words) - 00:50, 29 December 2024
drug design. He is also one of the originators of the Locality-sensitive hashing algorithm. Motwani was one of the co-authors (with Larry Page and Sergey...
12 KB (919 words) - 03:30, 6 September 2024
A popular method to find the similar users is the Locality-sensitive hashing, which implements the nearest neighbor mechanism in linear time. The advantages...
39 KB (4,798 words) - 05:38, 12 December 2024
Man" Jack Hively Herbert Purdom January 2, 1970 (1970-01-02) Stars Jesse Pearson and Royal Dano. 438 12 "Pioneer Pluck" Jean Yarbrough William Davis Jr...
128 KB (183 words) - 18:21, 4 January 2025
Cannabis (drug) (section Hash oil)
S2CID 16313727. Oltmanns T, Emery R (2015). Abnormal Psychology. New Jersey: Pearson. p. 294. ISBN 978-0205970742. D'Souza DC, Sewell RA, Ranganathan M (October...
165 KB (17,248 words) - 02:50, 20 December 2024
local lemma Stein's lemma Wald's lemma Glivenko–Cantelli lemma Neyman–Pearson lemma Robbins lemma Factorization lemma Fatou's lemma Frostman's lemma...
8 KB (524 words) - 11:06, 2 August 2024
2.3. Balanced trees 6.2.4. Multiway trees 6.3. Digital searching 6.4. Hashing 6.5. Retrieval on secondary keys Chapter 7 – Combinatorial searching 7...
38 KB (4,044 words) - 04:58, 3 January 2025
and Haskell Springer (eds), Herman Melville, Moby-Dick. New York Boston: Pearson Longman (A Longman Critical Edition). ISBN 0-321-22800-6. Buell, Lawrence...
118 KB (16,810 words) - 15:54, 18 December 2024
MAXEkSAT. k-wise independence is used in the proof that k-independent hashing functions are secure unforgeable message authentication codes. Pairwise...
12 KB (1,670 words) - 02:39, 9 March 2024
two-year contract extension until the summer of 2016. 2 June 2014 – James Pearson signs a one-year contract extension until the summer of 2015. 4 June 2014...
94 KB (1,735 words) - 19:12, 2 May 2024
(January 1911). "Every Day Foods That Injure Health". Pearson's Magazine. 25. New York: Pearson Pub. Co.: 249. you have probably noticed how nice and...
28 KB (3,032 words) - 19:51, 25 December 2024
Associative Arrays". Developer's Guide to Collections in Microsoft .NET. Pearson Education. p. 191. ISBN 9780735665279. McCarthy, John; Abrahams, Paul W...
8 KB (897 words) - 16:36, 9 September 2024
July 2017, Think and Learn acquired TutorVista (including Edurite) from Pearson. In January 2019, Byju's acquired American-based Osmo, a maker of educational...
68 KB (5,688 words) - 01:59, 29 December 2024
it, and for identifying candidates to be sharded separately. Consistent hashing is a technique used in sharding to spread large loads across multiple smaller...
19 KB (2,053 words) - 07:43, 3 December 2024
William (2012). Computer security : principles and practice. Boston: Pearson. p. 182. ISBN 978-0-13-277506-9. "Worm vs. Virus: What's the Difference...
91 KB (9,456 words) - 23:03, 30 December 2024