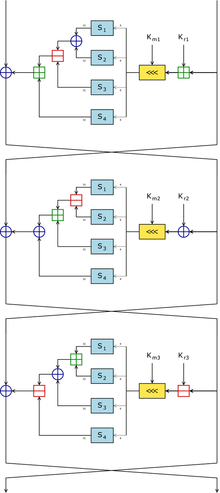
In cryptography, CAST-128 (alternatively CAST5) is a symmetric-key block cipher used in a number of products, notably as the default cipher in some versions...
4 KB (378 words) - 19:55, 13 April 2024
finalists. It is an extension of an earlier cipher, CAST-128; both were designed according to the "CAST" design methodology invented by Carlisle Adams and...
3 KB (331 words) - 04:48, 18 March 2024
Advanced Encryption Standard (redirect from Aes-128)
members of the Rijndael family, each with a block size of 128 bits, but three different key lengths: 128, 192 and 256 bits. AES has been adopted by the U.S....
49 KB (5,564 words) - 02:48, 16 September 2024
printable) A 128-bit integer can represent up to 3.40282366...e+38 values (2128 = 340,282,366,920,938,463,463,374,607,431,768,211,456). CAST-128 is a block...
7 KB (870 words) - 05:51, 30 August 2024
DNA CAST (gene), which encodes the protein calpastatin CAST (race), a fictional race of androids in the Phantasy Star series of video games CAST-128, a...
2 KB (316 words) - 22:00, 6 February 2024
Feistel-like MIX function. Feistel or modified Feistel: Generalised Feistel: CAST-256 CLEFIA MacGuffin RC2 RC6 Skipjack SMS4 Cryptography Stream cipher...
10 KB (1,316 words) - 23:55, 19 August 2024
Encryption Standard (AES) algorithm, approved by NIST in December 2001, uses 128-bit blocks. Examples of popular symmetric-key algorithms include Twofish...
15 KB (1,544 words) - 02:53, 7 June 2024
their initials CAST-256 (CAST6) – 128-bit block; the successor to CAST-128 and a candidate for the AES competition CIPHERUNICORN-A – 128-bit block; CRYPTREC...
20 KB (1,890 words) - 03:11, 18 August 2024
cipher and uses large key-dependent S-boxes. In structure it resembles CAST-128, which uses fixed S-boxes. The adjacent diagram shows Blowfish's encryption...
18 KB (2,000 words) - 06:17, 22 September 2024
algorithms typically use computationally stronger 128- to 256-bit keys. There is a physical argument that a 128-bit symmetric key is computationally secure...
21 KB (2,250 words) - 15:26, 19 July 2024
data were tampered with. GCM uses a block cipher with block size 128 bits (commonly AES-128) operated in counter mode for encryption, and uses arithmetic...
23 KB (2,996 words) - 08:23, 11 September 2024
of operation of the cipher. The simplest mode encrypts and decrypts each 128-bit block separately. In this mode, called electronic code book (ECB), blocks...
12 KB (1,295 words) - 08:30, 9 August 2024
problems led them to eschew patents entirely. PGP 3 introduced the use of the CAST-128 (a.k.a. CAST5) symmetric key algorithm, and the DSA and ElGamal asymmetric...
47 KB (5,673 words) - 20:49, 21 September 2024
algorithms were all to be block ciphers, supporting a block size of 128 bits and key sizes of 128, 192, and 256 bits. Such ciphers were rare at the time of the...
10 KB (1,040 words) - 02:50, 11 January 2024
February 2023, the Ascon suite contained seven ciphers, including: Ascon-128 and Ascon-128a authenticated ciphers; Ascon-Hash cryptographic hash; Ascon-Xof...
8 KB (848 words) - 03:29, 28 April 2024
single invocation of the AES algorithm transforms a 128-bit plaintext block into a ciphertext block of 128 bits in size. The key, which is given as one input...
14 KB (1,797 words) - 08:53, 7 September 2024
a one bit change in CFB-128 with an underlying 128 bit block cipher, will re-synchronize after two blocks. (However, CFB-128 etc. will not handle bit...
52 KB (5,878 words) - 15:11, 20 September 2024
(2009-08-23). "New Linear Cryptanalytic Results of Reduced-Round of CAST-128 and CAST-256". Selected Areas in Cryptography. Lecture Notes in Computer Science...
15 KB (801 words) - 01:34, 22 August 2024
what the bits are. KASUMI is an eight round, 64-bit block cipher with a 128-bit key. It is based upon MISTY1 and was designed to form the basis of the...
5 KB (688 words) - 07:27, 20 November 2023
confidentiality. CCM mode is only defined for block ciphers with a block length of 128 bits. The nonce of CCM must be carefully chosen to never be used more than...
8 KB (924 words) - 10:55, 17 July 2024
have simple key schedules. For example, the block cipher TEA splits the 128-bit key into four 32-bit pieces and uses them repeatedly in successive rounds...
3 KB (402 words) - 17:31, 15 March 2023
x 128 + x 127 + x 126 + x 121 + 1 {\displaystyle x^{128}+x^{127}+x^{126}+x^{121}+1} Note that GHASH is defined over the "reverse" polynomial: x 128 +...
4 KB (397 words) - 18:19, 16 September 2024
a key size of 64 bits. There was some demand for a version with a larger 128-bit key, and the following year Massey published such a variant incorporating...
7 KB (838 words) - 06:46, 27 April 2022
algorithms: Ciphers AES, Blowfish, Camellia, Chacha20, Poly1305, SEED, CAST-128, DES, IDEA, RC2, RC4, RC5, Triple DES, GOST 28147-89, SM4 Cryptographic...
51 KB (4,697 words) - 00:56, 15 August 2024
cryptography, Twofish is a symmetric key block cipher with a block size of 128 bits and key sizes up to 256 bits. It was one of the five finalists of the...
9 KB (839 words) - 23:27, 24 September 2024
a 128-bit key and operates on 128-bit blocks. Sorkin (1984) described a later Lucifer as a 16-round Feistel network, also on 128-bit blocks and 128-bit...
6 KB (749 words) - 15:35, 22 November 2023
less than one day, using 128 Spartan-3 5000's. SciEngines RIVYERA held the record in brute-force breaking DES, having utilized 128 Spartan-3 5000 FPGAs....
59 KB (6,543 words) - 01:44, 20 September 2024
files to be stored using an encryption algorithm such as Triple DES or CAST-128. Email messages can be protected by using cryptography in various ways...
25 KB (2,781 words) - 04:05, 19 September 2024
Create and mount a virtual drive encrypted using AES, Blowfish, Twofish, CAST-128 and various other encryption methods. BestCrypt v.8 and higher can alternatively...
6 KB (371 words) - 14:21, 5 July 2023
3.0, WAKE, WAKE-OFB, DESX (DES-XEX3), RC2, SAFER, 3-WAY, GOST, SHARK, CAST-128, and Square. In a 2007 ECRYPT workshop paper focusing on public key implementations...
19 KB (1,314 words) - 22:18, 14 July 2024