A logic bomb is a piece of code intentionally inserted into a software system that will set off a malicious function when specified conditions are met...
17 KB (1,998 words) - 22:41, 29 April 2024
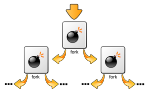
way logic bombs deliver their payloads to the target. The main difference between both time and logic bombs, and fork bombs, is that a fork bomb has no...
5 KB (633 words) - 19:53, 22 May 2024
produces the maximum possible output before terminating E-mail bomb Fork bomb Logic bomb Online algorithm, limit discovered rather than declared at 14:35...
4 KB (427 words) - 20:24, 27 August 2024
Operation Logic Bomb: The Ultimate Search & Destroy, known in Japan as Ikari no Yōsai (怒りの要塞, "The Fortress of Fury") is a 1993 overhead action video game...
7 KB (686 words) - 23:19, 9 July 2024
finer-grained fork bomb prevention through cgroups and process number (PID) controllers. Deadlock (computer science) Logic bomb Time bomb (software) Raymond...
8 KB (816 words) - 19:11, 20 August 2024
"eps2.3_logic-b0mb.hc" is the fifth episode of the second season of the American drama thriller television series Mr. Robot. It is the fifteenth overall...
14 KB (1,501 words) - 13:23, 7 September 2024
Jerusalem is a logic bomb DOS virus first detected at Hebrew University of Jerusalem, in October 1987. On infection, the Jerusalem virus becomes memory...
18 KB (2,398 words) - 09:10, 20 June 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
5 KB (525 words) - 23:04, 21 August 2024
Auditore, Kassandra, and Connor to find the fragments, but secretly plants logic bombs across the memories to destroy them and prevent Abstergo from obtaining...
14 KB (1,306 words) - 06:19, 1 September 2024
Look up bomb, bombed, bomber, or bombing in Wiktionary, the free dictionary. A bomb is an explosive device. Bomb or its variants may also refer to: Box-office...
3 KB (390 words) - 18:06, 24 August 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
7 KB (630 words) - 14:38, 27 August 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
17 KB (1,784 words) - 03:01, 5 September 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
6 KB (559 words) - 06:44, 19 March 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
37 KB (3,229 words) - 05:08, 17 August 2024
back to the computer inside the company's network. The malware had a logic bomb which triggered the master boot record and data wiping payload at 11:08 am...
18 KB (1,971 words) - 05:48, 12 August 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
20 KB (1,903 words) - 09:42, 8 September 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
76 KB (7,588 words) - 08:41, 25 August 2024
that he wrote for her company. While Anton is in jail, he triggers a logic bomb that he left in Eva's software as an insurance policy; this results in...
16 KB (1,569 words) - 02:37, 17 August 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
2 KB (170 words) - 18:58, 24 June 2024
Government Saving Privacy in the Digital Age. Penguin. ISBN 0-14-024432-8. Logik Bomb: Hacker's Encyclopedia Archived 2007-07-08 at the Wayback Machine (1997)...
40 KB (4,246 words) - 07:50, 2 August 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
13 KB (1,505 words) - 13:29, 22 August 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
58 KB (6,546 words) - 02:15, 1 September 2024
computers that were infected. Blaster Lovesan, MSBLAST Mass DoS attacks Logic bomb (payload set to activate August 15) August 11, 2003 Hopkins, Minnesota...
10 KB (196 words) - 17:51, 6 July 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
174 KB (15,617 words) - 02:48, 3 September 2024
system component. "Malicious logic" In the context of incapacitation, any hardware, firmware, or software (e.g., logic bomb) intentionally introduced into...
39 KB (4,698 words) - 19:45, 14 August 2024
Zone-H Malware Rootkit Backdoor Trojan horse Virus Worm Spyware Ransomware Logic bomb Botnet Keystroke logging HIDS Web shell RCE Infostealer Computer security...
19 KB (2,158 words) - 12:28, 4 September 2024
they are run, such as the Jerusalem DOS virus. Trigger Also known as a logic bomb, this is the part of the virus that determines the condition for which...
90 KB (9,371 words) - 09:52, 4 September 2024
Brothers (SNES) City Connection (NES) The Ignition Factor (SNES) Operation Logic Bomb (SNES) Rival Turf! (SNES) Super E.D.F.: Earth Defense Force (SNES) Super...
30 KB (427 words) - 02:33, 8 September 2024
its own coding sequence the query of the attacker and the necessary PIR logic to apply the query to host systems. The first cryptovirology attack and...
14 KB (1,458 words) - 07:19, 31 August 2024
of the server. Business logic vulnerability occurs when programmers do not consider unexpected cases arising in business logic. There is little evidence...
26 KB (3,257 words) - 02:58, 19 July 2024