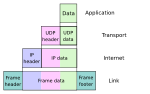
In computer networks, a tunneling protocol is a communication protocol which allows for the movement of data from one network to another. It can, for example...
15 KB (1,910 words) - 15:07, 15 June 2024
In computer networking, Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol used to support virtual private networks (VPNs) or as part of the delivery...
15 KB (1,825 words) - 14:10, 15 June 2024
(SASL) protocol Tunnel encapsulation for a variety of tunneling scenarios: IPv6 over IPv4 tunnels IPv4 over IPv6 tunnels IPv6 over UDP/IPv4 tunnels for built-in...
2 KB (302 words) - 01:24, 20 November 2023
Secure Socket Tunneling Protocol (SSTP) is a form of virtual private network (VPN) tunnel that provides a mechanism to transport PPP traffic through an...
7 KB (747 words) - 05:45, 28 September 2023
The Point-to-Point Tunneling Protocol (PPTP) is an obsolete method for implementing virtual private networks. PPTP has many well known security issues...
8 KB (847 words) - 01:32, 4 April 2024
GPRS Tunnelling Protocol (GTP) is a group of IP-based communications protocols used to carry general packet radio service (GPRS) within GSM, UMTS, LTE...
17 KB (2,229 words) - 10:26, 16 July 2024
port 3544. For 6to4, the most common IPv6 over IPv4 tunneling protocol, requires that the tunnel endpoint have a public IPv4 address. However, many hosts...
27 KB (3,433 words) - 14:36, 20 December 2023
between computing devices and computer networks by the use of network tunneling protocols. It is possible to make a VPN secure to use on top of insecure communication...
34 KB (3,734 words) - 21:40, 23 August 2024
Look up tunneling in Wiktionary, the free dictionary. Tunneling or tunnelling may refer to: Digging tunnels (the literal meaning) Hobby tunneling Quantum...
581 bytes (112 words) - 14:00, 6 June 2020
Generic Routing Encapsulation (redirect from GRE tunneling)
Encapsulation (GRE) is a tunneling protocol developed by Cisco Systems that can encapsulate a wide variety of network layer protocols inside virtual point-to-point...
15 KB (1,296 words) - 12:44, 22 July 2024
SCSI connector (redirect from Serial ATA Tunneling Protocol)
installed in an SAS drive bay, and the enclosure can use the Serial ATA Tunneling Protocol (STP) to make use of the drive.: 16, 17 There are keyed parts to...
21 KB (2,744 words) - 14:04, 15 April 2024
L2F, or Layer 2 Forwarding, is a tunneling protocol developed by Cisco Systems, Inc. to establish virtual private network connections over the Internet...
2 KB (132 words) - 08:29, 31 October 2023
Aggregation Control Protocol LattisNet LocalTalk L2F Layer 2 Forwarding Protocol L2TP Layer 2 Tunneling Protocol LLDP Link Layer Discovery Protocol LLDP-MED Link...
11 KB (970 words) - 19:15, 31 July 2024
to block IP tunnels. The first specification of IP tunneling was in RFC 1075, which described DVMRP, the first IP multicast routing protocol. Because multicast...
3 KB (467 words) - 04:21, 3 August 2021
tunnel is created by an intermediary called a proxy server which is usually located in a DMZ. Tunneling can also allow communication using a protocol...
5 KB (591 words) - 15:06, 12 November 2023
Tunneling Protocol) is a form of PPP between two hosts via GRE using encryption (MPPE) and compression (MPPC). Many protocols can be used to tunnel data...
21 KB (2,280 words) - 14:01, 20 August 2024
IPsec (redirect from Internet Protocol Security)
Information security NAT traversal Opportunistic encryption tcpcrypt Tunneling protocol Kent, S.; Atkinson, R. (November 1998). IP Encapsulating Security...
48 KB (5,081 words) - 17:09, 27 August 2024
This is a list of the IP protocol numbers found in the field Protocol of the IPv4 header and the Next Header field of the IPv6 header. It is an identifier...
20 KB (120 words) - 15:21, 21 August 2024
Virtual Extensible LAN (redirect from VXLAN tunnel endpoint)
Overlay Transport Virtualization (OTV) Virtual LAN (VLAN) Layer 2 Tunneling Protocol (L2TP) Steve Herrod (August 30, 2011). "Towards Virtualized Networking...
6 KB (555 words) - 13:33, 27 June 2024
ATM Point-to-Point Protocol daemon Point-to-Point Tunneling Protocol Point-to-Point Protocol over ATM (PPPoA) Point-to-Point Protocol over X (PPPoX) James...
44 KB (5,587 words) - 11:35, 7 July 2024
IP in IP (category Tunneling protocols)
IP in IP is an IP tunneling protocol that encapsulates one IP packet in another IP packet. To encapsulate an IP packet in another IP packet, an outer header...
4 KB (519 words) - 06:36, 8 September 2022
Multiprotocol Label Switching (redirect from Multi-protocol label switching)
paths between endpoints. MPLS can encapsulate packets of various network protocols, hence the multiprotocol component of the name. MPLS supports a range...
35 KB (4,534 words) - 15:21, 21 August 2024
packets. An example of this technique is tunneling complete TCP traffic over ping requests and replies. ICMP tunneling works by injecting arbitrary data into...
5 KB (559 words) - 03:28, 25 July 2023
GPRS core network (redirect from Packet Data Protocol)
network. All GSNs should have a Gn interface and support the GPRS tunneling protocol. There are two key variants of the GSN, namely gateway GPRS support...
15 KB (2,032 words) - 16:06, 4 April 2023
6in4 (category Tunneling protocols)
transition mechanism for migrating from Internet Protocol version 4 (IPv4) to IPv6. It is a tunneling protocol that encapsulates IPv6 packets on specially...
5 KB (557 words) - 11:56, 15 June 2024
example, protocols are often stacked in a tunneling arrangement to accommodate the connection of dissimilar networks. For example, IP may be tunneled across...
65 KB (8,221 words) - 06:05, 27 August 2024
Encapsulation (networking) (redirect from Upper layer protocol)
processes can also serve as malicious features like in the tunneling protocols. The physical layer is responsible for physical transmission of the...
6 KB (564 words) - 22:55, 31 July 2024
IP-HTTPS (category Network protocols)
Split Tunneling and Force Tunneling". Microsoft. The problem with IP-HTTPS is that it should be considered, and is instantiated as, a protocol of last...
2 KB (160 words) - 19:14, 31 December 2023
IPv6 (redirect from Internet Protocol Version 6)
backbone was IPv4-only, one of the frequently used tunneling protocols was 6to4. Teredo tunneling was also frequently used for integrating IPv6 LANs with...
61 KB (7,700 words) - 09:30, 27 August 2024
USB4 (section USB3 Gen X Tunneling)
by carrying virtualized "tunnels" of other connections. This includes tunneling of USB3 and DP connections. Other protocols, such as PCI Express and Ethernet...
64 KB (6,029 words) - 08:13, 22 August 2024