relational database management systems, a unique key is a candidate key. All the candidate keys of a relation can uniquely identify the records of the relation...
10 KB (1,172 words) - 18:41, 25 April 2024
A Universally Unique Identifier (UUID) is a 128-bit label used for information in computer systems. The term Globally Unique Identifier (GUID) is also...
37 KB (4,487 words) - 04:38, 4 October 2024
unique attribute or combination of attributes from the table (a natural key) to act as its primary key, or create a new attribute containing a unique...
7 KB (885 words) - 18:43, 7 September 2024
Unique Key Per Transaction (DUKPT) is a key management scheme in which for every transaction, a unique key is used which is derived from a fixed key....
12 KB (1,854 words) - 14:11, 15 May 2024
A natural key (also known as business key or domain key) is a type of unique key in a database formed of attributes that exist and are used in the external...
4 KB (630 words) - 06:43, 15 May 2024
database design, a composite key is a candidate key that consists of two or more attributes, (table columns) that together uniquely identify an entity occurrence...
5 KB (677 words) - 08:13, 4 June 2024
numbers assigned to any rows where sort_key is the same. When sort_key is unique, each row will always get a unique row number. The RANK() OVER window function...
33 KB (3,102 words) - 21:09, 3 October 2024
Look up key or Keys in Wiktionary, the free dictionary. Key, Keys, The Key or The Keys may refer to: Key (cryptography), a piece of information needed...
6 KB (796 words) - 13:52, 26 June 2024
or set of locks that are keyed alike, a lock/key system where each similarly keyed lock requires the same, unique key. The key serves as a security token...
34 KB (3,909 words) - 22:51, 17 August 2024
applications, see hash function or unique key This disambiguation page lists articles associated with the title Hash key. If an internal link led you here...
249 bytes (70 words) - 12:42, 27 June 2020
Hi/Lo is an algorithm and a key generation strategy used for generating unique keys for use in a database as a primary key. It uses a sequence-based hi-lo...
11 KB (1,229 words) - 14:22, 7 March 2024
entity that serve as unique identifiers are called primary keys. In mathematics, set theory uses the concept of element indices as unique identifiers. There...
8 KB (710 words) - 01:44, 29 July 2024
Relational database (section Primary key)
in a table has its own unique key. Rows in a table can be linked to rows in other tables by adding a column for the unique key of the linked row (such...
32 KB (3,839 words) - 20:18, 9 September 2024
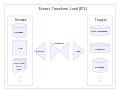
Extract, transform, load (section Uniqueness of keys)
transformation and update. Unique keys play an important part in all relational databases, as they tie everything together. A unique key is a column that identifies...
28 KB (3,873 words) - 15:33, 1 October 2024
generate the same key, CAS systems ensure that the files within them are unique, and because changing the file will result in a new key, CAS systems provide...
23 KB (3,217 words) - 22:26, 12 March 2024
surrogate key (or synthetic key, pseudokey, entity identifier, factless key, or technical key[citation needed]) in a database is a unique identifier...
18 KB (2,344 words) - 16:31, 8 August 2024
storage system.: 5 Each record in a KSDS data file is embedded with a unique key.: 20 A KSDS consists of two parts, the data component and a separate...
2 KB (262 words) - 20:39, 9 June 2024
Wi-Fi Protected Access (redirect from WPA key)
and 128-bit keys, combining user-configurable and factory-set bits. WEP used the RC4 algorithm for encrypting data, creating a unique key for each packet...
40 KB (4,696 words) - 10:45, 18 September 2024
natural key and Supplier_Key is a surrogate key. Technically, the surrogate key is not necessary, since the row will be unique by the natural key (Supplier_Code)...
21 KB (2,415 words) - 15:59, 2 October 2024
Associative array (redirect from Key-value association)
value must be associated with a unique key, and a second lookup operation takes a value as an argument and looks up the key associated with that value. The...
24 KB (2,773 words) - 12:03, 6 September 2024
Reverse lookup is a procedure of using a value to retrieve a unique key in an associative array. Applications of reverse lookup include reverse DNS lookup...
1 KB (119 words) - 01:24, 22 January 2024
and also has a unique relationship to the other pitches of the same key, their corresponding chords, and pitches and chords outside the key. Notes and chords...
14 KB (2,013 words) - 23:39, 14 August 2024
Aadhaar (redirect from National Authority for Unique Identity)
Aadhaar (Hindi: आधार, lit. 'base, foundation') is a twelve-digit unique identity number that can be obtained voluntarily by all residents of India, based...
187 KB (16,622 words) - 13:28, 2 October 2024
In marketing, the unique selling proposition (USP), also called the unique selling point or the unique value proposition (UVP) in the business model canvas...
15 KB (1,708 words) - 21:35, 27 September 2024
A Central Index Key or CIK number is a unique number assigned to an individual, company, filing agent or foreign government by the United States Securities...
1 KB (101 words) - 12:32, 1 June 2024
can share the same routing key. A routing key coupled with a unique identifier looks like this: This corresponds to the unique address of Terenure Post...
12 KB (231 words) - 15:37, 18 August 2024
An application programming interface (API) key is a secret unique identifier used to authenticate and authorize a user, developer, or calling program to...
5 KB (428 words) - 10:47, 1 September 2024
incorporated and processed in the National Database of the Unique Population Registration Key, are used as elements of support in the role of the Secretary...
8 KB (1,097 words) - 04:33, 11 June 2024
with a unique key, which is the part after its top-level domain name. For example, https://tinyurl.com/m3q2xt has a key of m3q2xt, these keys are case-sensitive...
37 KB (3,832 words) - 11:32, 29 August 2024
registered on the server with a unique key (e.g., a UUID). The server then fires the message against the unique key to deliver it to the client via an...
21 KB (2,450 words) - 14:21, 1 October 2024