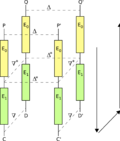
cryptography, the eXtended Sparse Linearization (XSL) attack is a method of cryptanalysis for block ciphers. The attack was first published in 2002 by researchers...
15 KB (1,777 words) - 09:31, 18 June 2024
document transformation and presentation XSL Formatting Objects The XSL attack (eXtended Sparse Linearisation attack), a method for breaking ciphers The Xtreme...
445 bytes (85 words) - 02:13, 10 November 2013
Advanced Encryption Standard (section Known attacks)
a fairly simple algebraic framework. In 2002, a theoretical attack, named the "XSL attack", was announced by Nicolas Courtois and Josef Pieprzyk, purporting...
49 KB (5,595 words) - 00:02, 27 August 2024
Brisbane, Australia. He has worked on cryptography, in particular the XSL attack. He collaborated in the invention of the LOKI and LOKI97 block ciphers...
941 bytes (51 words) - 16:26, 14 May 2024
XSL attack would be more expensive than a brute force attack.[citation needed] In 2000, a paper by Kohno et al. presents a meet-in-the-middle attack against...
16 KB (1,912 words) - 12:54, 8 June 2024
Cryptanalysis (redirect from Cryptanalytic attack)
cryptanalysis Meet-in-the-middle attack Mod-n cryptanalysis Related-key attack Sandwich attack Slide attack XSL attack Asymmetric cryptography (or public-key...
44 KB (5,202 words) - 13:26, 19 August 2024
Block cipher (section Brute-force attacks)
square and integral attacks, slide attacks, boomerang attacks, the XSL attack, impossible differential cryptanalysis, and algebraic attacks. For a new block...
50 KB (6,475 words) - 03:59, 22 August 2024
University College London. Courtois was one of the co-authors of both the XSL attack against block ciphers, such as the Advanced Encryption Standard, and the...
5 KB (368 words) - 05:46, 14 May 2024
cryptanalysis Meet-in-the-middle attack Mod-n cryptanalysis Related-key attack Slide attack XSL attack Hash functions: Birthday attack Attack models Chosen-ciphertext...
20 KB (1,890 words) - 03:11, 18 August 2024
brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically...
21 KB (2,250 words) - 15:26, 19 July 2024
In cryptography, a timing attack is a side-channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute...
12 KB (1,524 words) - 20:12, 19 July 2024
XDH assumption • Xiaoyun Wang • XML Encryption • XML Signature • xmx • XSL attack • XTEA • XTR • Xuejia Lai • XXTEA 10-00-00-00-00 Yarrow algorithm • Y-stations...
67 KB (2,933 words) - 23:58, 6 June 2024
Submarine aircraft carrier (redirect from Loening XSL-1)
1923. Later, Cox-Klemm built the improved XS-2 model, and Loening built the XSL, but the Navy had lost interest in the concept by then. Problems with launching...
21 KB (2,767 words) - 16:59, 13 August 2024
In cryptography, a related-key attack is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys...
5 KB (688 words) - 07:27, 20 November 2023
Differential cryptanalysis (redirect from Differential attack)
resistant to this attack and many including the Advanced Encryption Standard, have been proven secure against the attack. The attack relies primarily on...
13 KB (1,688 words) - 22:44, 29 October 2023
Correlation attacks are a class of cryptographic known-plaintext attacks for breaking stream ciphers whose keystreams are generated by combining the output...
15 KB (2,299 words) - 17:59, 30 July 2024
The meet-in-the-middle attack (MITM), a known plaintext attack, is a generic space–time tradeoff cryptographic attack against encryption schemes that rely...
17 KB (3,219 words) - 03:07, 18 August 2024
The rebound attack is a tool in the cryptanalysis of cryptographic hash functions. The attack was first published in 2009 by Florian Mendel, Christian...
14 KB (1,939 words) - 19:32, 23 September 2020
cryptography, the Davies attack is a dedicated statistical cryptanalysis method for attacking the Data Encryption Standard (DES). The attack was originally created...
3 KB (257 words) - 04:10, 5 July 2023
technique that can be used with a MITM attack. Partial-matching is where the intermediate values of the MITM attack, i {\displaystyle i} and j {\displaystyle...
4 KB (704 words) - 08:23, 30 June 2020
KeeLoq (section Replay attack)
button press. This provides protection against brute-force attack and capture and replay attack, known as RollJam for Samy Kamkar's work. For simplicity...
13 KB (1,561 words) - 23:57, 27 May 2024
cryptography, an interpolation attack is a type of cryptanalytic attack against block ciphers. After the two attacks, differential cryptanalysis and...
12 KB (2,288 words) - 21:31, 30 July 2024
extend the number of possibly attacked rounds by the MITM attack. Since biclique cryptanalysis is based on MITM attacks, it is applicable to both block...
18 KB (3,173 words) - 22:38, 29 October 2023
Cipher security summary (section Best attack)
to date. No known successful attacks — attack only breaks a reduced version of the cipher Theoretical break — attack breaks all rounds and has lower...
15 KB (801 words) - 01:34, 22 August 2024
cryptography, the boomerang attack is a method for the cryptanalysis of block ciphers based on differential cryptanalysis. The attack was published in 1999...
9 KB (864 words) - 04:16, 17 October 2023
Data Encryption Standard (section Brute-force attack)
(strengthened against differential cryptanalysis, but weakened against brute-force attacks), which was published as an official Federal Information Processing Standard...
59 KB (6,541 words) - 09:32, 30 July 2024
Side-channel Timing Power-monitoring Electromagnetic Acoustic Differential-fault XSL Interpolation Partitioning Rubber-hose Black-bag Davies Rebound Weak key...
8 KB (848 words) - 03:29, 28 April 2024
Impossible differential cryptanalysis (redirect from Impossible differential attack)
cipher algorithm. Lars Knudsen appears to be the first to use a form of this attack, in the 1998 paper where he introduced his AES candidate, DEAL. The first...
10 KB (850 words) - 11:20, 13 February 2024
edu/saxon/servlet/SaxonServlet?source=xwomen/texts/hanfei.xml&style=xwomen/xsl/dynaxml.xsl&chunk.id=d1.4&toc.depth=1&toc.id=0&doc.lang=bilingual Tae Hyun KIM...
12 KB (1,498 words) - 17:16, 20 August 2024
The slide attack is a form of cryptanalysis designed to deal with the prevailing idea that even weak ciphers can become very strong by increasing the number...
7 KB (1,135 words) - 08:49, 25 July 2023