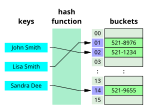
output. The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. The values are usually used to...
50 KB (7,536 words) - 16:10, 29 August 2024
Look up hash in Wiktionary, the free dictionary. Hash, hashes, hash mark, or hashing may refer to: Hash (food), a coarse mixture of ingredients, often...
2 KB (283 words) - 21:49, 5 July 2024
A cryptographic hash function (CHF) is a hash algorithm (a map of an arbitrary binary string to a binary string with a fixed size of n {\displaystyle...
48 KB (6,228 words) - 12:47, 4 September 2024
is hashed and the resulting hash indicates where the corresponding value is stored. A map implemented by a hash table is called a hash map. Most hash table...
52 KB (5,869 words) - 19:02, 24 August 2024
Hash browns, also spelled hashed browns and hashbrowns, are a popular American breakfast dish consisting of finely julienned potatoes that have been fried...
7 KB (674 words) - 08:05, 25 August 2024
Number sign (redirect from Hash sign)
symbol # is known variously in English-speaking regions as the number sign, hash, or pound sign. The symbol has historically been used for a wide range of...
43 KB (4,419 words) - 09:07, 30 August 2024
Hash oil or cannabis oil is an oleoresin obtained by the extraction of cannabis or hashish. It is a cannabis concentrate containing many of its resins...
34 KB (3,454 words) - 14:03, 25 August 2024
Hashish (redirect from Finger hash)
(Persian: حشیش, romanized: ḥašiš, IPA: [ħæʃiːʃ]), usually abbreviated as hash, is a compressed form of powdered marijuana. As a psychoactive substance...
37 KB (4,290 words) - 17:30, 2 September 2024
a Hash or Run, or a Hash Run. A common denominal verb for this activity is Hashing, with participants calling themselves Hashers. Male members are referred...
30 KB (3,866 words) - 00:22, 3 September 2024
The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S...
3 KB (464 words) - 13:15, 22 July 2024
a checksum. Hash function security summary Secure Hash Algorithms NIST hash function competition Key derivation functions (category) "Hash functions"....
10 KB (280 words) - 10:21, 23 June 2024
Hash is a dish consisting of chopped meat, potatoes, and fried onions. The name is derived from French: hacher, meaning 'to chop'. It originated as a way...
15 KB (1,533 words) - 01:11, 26 August 2024
computer science, a hash collision or hash clash is when two distinct pieces of data in a hash table share the same hash value. The hash value in this case...
9 KB (1,130 words) - 16:51, 9 August 2024
Merkle tree (redirect from Tiger-Tree Hash)
the above picture hash 0 is the result of hashing the concatenation of hash 0-0 and hash 0-1. That is, hash 0 = hash( hash 0-0 + hash 0-1 ) where "+" denotes...
15 KB (1,788 words) - 18:26, 28 July 2024
[#] (read as "hash") is the second extended play by South Korean girl group Loona. It was released on February 5, 2020, by Blockberry Creative and distributed...
13 KB (871 words) - 19:33, 3 September 2024
HMAC (redirect from Keyed-Hashing Message Authentication)
cryptography, an HMAC (sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of...
18 KB (2,336 words) - 19:01, 3 September 2024
The hash join is an example of a join algorithm and is used in the implementation of a relational database management system. All variants of hash join...
8 KB (1,173 words) - 06:50, 29 July 2024
SHA-2 (category Cryptographic hash functions)
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA) and first published...
51 KB (4,951 words) - 09:05, 3 September 2024
A hash chain is the successive application of a cryptographic hash function to a piece of data. In computer security, a hash chain is a method used to...
7 KB (1,005 words) - 23:12, 10 May 2024
Hash fossils are groups of fossils in the same rock. The term hash fossil describes the fossil formed when all the organic material in an environment falls...
1,016 bytes (95 words) - 20:47, 1 September 2024
In computer science, locality-sensitive hashing (LSH) is a fuzzy hashing technique that hashes similar input items into the same "buckets" with high probability...
30 KB (4,013 words) - 13:50, 25 June 2024
fnv-1 is hash := FNV_offset_basis for each byte_of_data to be hashed do hash := hash × FNV_prime hash := hash XOR byte_of_data return hash In the above...
14 KB (1,342 words) - 15:52, 2 September 2024
Hash key may refer to: Number sign, also known as the number, pound or hash key, a key on a telephone keypad For its use in data structure, database and...
249 bytes (70 words) - 12:42, 27 June 2020
Cryptography (section Cryptographic hash functions)
digital signature. For good hash functions, an attacker cannot find two messages that produce the same hash. MD4 is a long-used hash function that is now broken;...
98 KB (10,713 words) - 13:13, 22 August 2024
Look up hash tree in Wiktionary, the free dictionary. In computer science, hash tree may refer to: Hashed array tree Hash tree (persistent data structure)...
256 bytes (68 words) - 13:36, 29 April 2017
standard for identifying files (URN) by their content, via cryptographic hash value rather than by their location. Although magnet links can be used in...
20 KB (1,304 words) - 15:57, 4 August 2024
In computer science, a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers, with no collisions...
24 KB (2,956 words) - 14:27, 22 July 2024
SHA-1 (redirect from SHA-1 hash)
cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest...
51 KB (5,762 words) - 21:53, 22 July 2024