Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. In steganograhy, a message is concealed...
8 KB (775 words) - 13:36, 18 October 2024
Voynich manuscript (category Undeciphered historical codes and ciphers)
published Roger Bacon's Cipher: The Right Key Found, in which he claimed that the book was a scientific diary written by Roger Bacon. Feely's method posited...
142 KB (14,034 words) - 17:26, 20 October 2024
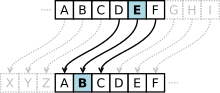
In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code, or Caesar shift, is one of the simplest and most widely...
19 KB (2,058 words) - 14:38, 20 October 2024
Orville Ward Owen (redirect from Word cipher)
Bacon's Cipher Story (1893–95). Owen's "cipher wheel" was a device for quickly collating printed pages from the works of Shakespeare, Francis Bacon,...
7 KB (972 words) - 04:22, 22 January 2024
The Vigenère cipher (French pronunciation: [viʒnɛːʁ]) is a method of encrypting alphabetic text where each letter of the plaintext is encoded with a different...
45 KB (5,937 words) - 15:15, 19 October 2024
Bacon baronets, three titles in the Baronetage of England, one extinct 2940 Bacon, an asteroid Bacon's, a chain of department stores Bacon's cipher,...
2 KB (332 words) - 09:34, 13 May 2024
technique used can recover the message and then decrypt it. Francis Bacon developed Bacon's cipher as such a technique. The ciphertext produced by most digital...
50 KB (5,804 words) - 23:21, 18 October 2024
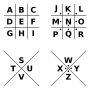
pigpen cipher (alternatively referred to as the masonic cipher, Freemason's cipher, Rosicrucian cipher, Napoleon cipher, and tic-tac-toe cipher) is a geometric...
11 KB (1,303 words) - 21:45, 9 October 2024
In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with...
30 KB (4,021 words) - 21:54, 7 October 2024
without actually being a music cipher. William F. Friedman embedded a secret message based on Francis Bacon's cipher into a sheet music arrangement of...
26 KB (3,617 words) - 18:04, 8 September 2024
philosophical ideas found in Bacon’s writings and the works of Shakespeare. Legal and autobiographical allusions and cryptographic ciphers and codes were later...
61 KB (8,134 words) - 22:47, 31 July 2024
by the report of Muskets, and any instruments of like nature". (See Bacon's cipher.) In 1617, John Napier described a system he called location arithmetic...
58 KB (7,028 words) - 09:42, 17 October 2024
null cipher, also known as concealment cipher, is an ancient form of encryption where the plaintext is mixed with a large amount of non-cipher material...
11 KB (1,496 words) - 22:12, 28 June 2024
technique used can recover the message and then decrypt it. Francis Bacon developed Bacon's cipher as such a technique. In the early days of the printing press...
30 KB (3,446 words) - 04:15, 31 July 2024
Enigma machine (redirect from Enigma cipher machine)
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication...
93 KB (11,246 words) - 18:55, 14 October 2024
upon manual and hand-written encoding and cyphering systems, such as Bacon's cipher, Braille, international maritime signal flags, and the 4-digit encoding...
32 KB (3,880 words) - 01:23, 7 October 2024
In cryptography, a transposition cipher (also known as a permutation cipher) is a method of encryption which scrambles the positions of characters (transposition)...
25 KB (3,604 words) - 03:23, 21 March 2024
Voynich was investigated by the FBI, in relation to his possession of Bacon's cipher. The report also noted that he dealt with manuscripts from the 13th...
10 KB (922 words) - 17:10, 19 October 2024
educators attacked by Bacon's 1271 Compendium Studii Philosophiae. Modern scholarship, however, notes that the first reference to Bacon's "imprisonment" dates...
101 KB (9,633 words) - 06:55, 18 October 2024
Hill cipher is a polygraphic substitution cipher based on linear algebra. Invented by Lester S. Hill in 1929, it was the first polygraphic cipher in which...
13 KB (2,241 words) - 21:56, 17 October 2024
clues in the text of the plays, in pictures, and in the alleged use of Bacon's cipher in the works. Manly Palmer Hall, in his The Secret Teachings of All...
60 KB (8,467 words) - 15:36, 11 October 2024
substitution ciphers, including the Bacon cipher and Polybius square, before moving on to transposition ciphers, Playfair ciphers and polyalphabetic ciphers such...
4 KB (507 words) - 09:22, 5 July 2023
Bacon's Cipher Story (1893), he claimed to have discovered Bacon's autobiography embedded in Shakespeare's plays, including the revelation that Bacon...
160 KB (18,572 words) - 13:47, 18 October 2024
secret history of the times. This type of cipher, also known as Bacon's cipher, had been discussed in Bacon's work. It depended on the use of two distinct...
5 KB (618 words) - 04:21, 22 January 2024
(1887) Essay on the Sonnets of Shakespeare The Great Cryptogram: Francis Bacon's Cipher in Shakespeare's Plays (1888), in which he maintained he had discovered...
18 KB (1,835 words) - 19:40, 2 September 2024
The Beaufort cipher, created by Sir Francis Beaufort, is a substitution cipher similar to the Vigenère cipher, with a slightly modified enciphering mechanism...
7 KB (835 words) - 15:43, 22 September 2024
The rail fence cipher (also called a zigzag cipher) is a classical type of transposition cipher. It derives its name from the manner in which encryption...
7 KB (1,103 words) - 16:01, 16 September 2023
In cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. In contrast to modern...
15 KB (2,528 words) - 02:24, 15 June 2024
Pegasus, and Orion systems The steganographic code, commonly known as Bacon's cipher uses groups of 5 binary-valued elements to represent letters of the...
7 KB (894 words) - 05:03, 22 April 2024
The Playfair cipher or Playfair square or Wheatstone–Playfair cipher is a manual symmetric encryption technique and was the first literal digram substitution...
20 KB (2,502 words) - 18:18, 12 September 2024