In security engineering, security through obscurity is the practice of concealing the details or mechanisms of a system to enhance its security. This approach...
14 KB (1,396 words) - 17:18, 10 November 2024
Kerckhoffs's principle (redirect from Security through transparency)
concept is widely embraced by cryptographers, in contrast to security through obscurity, which is not. Kerckhoffs's principle was phrased by American...
15 KB (1,719 words) - 11:26, 27 October 2024
Secure by design (redirect from Security through design)
Computer security Cyber security standards Hardening Multiple Independent Levels of Security Security through obscurity Software Security Assurance Santos...
9 KB (1,082 words) - 01:52, 3 November 2024
Look up obscurity in Wiktionary, the free dictionary. Obscurity may refer to: Security through obscurity, a controversial principle in security engineering...
357 bytes (77 words) - 05:30, 14 May 2021
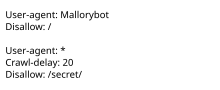
Robots.txt (section Security)
visit, though standards bodies discourage countering this with security through obscurity. Some archival sites ignore robots.txt. The standard was used...
32 KB (2,877 words) - 02:59, 21 November 2024
concern about the software's closed-source nature and alleged security through obscurity design. In 2001, UltraReach was founded by members of Falun Gong...
14 KB (1,464 words) - 15:40, 6 October 2024
algorithm itself. Analysis of the algorithm shows that it relies on security through obscurity. For example, this renders RTMPE vulnerable to Man in the Middle...
5 KB (680 words) - 13:12, 3 July 2023
users' privacy Security engineering – Process of incorporating security controls into an information system Security through obscurity – Reliance on design...
222 KB (22,527 words) - 14:55, 19 November 2024
Programmers may deliberately obfuscate code to conceal its purpose (security through obscurity) or its logic or implicit values embedded in it, primarily, in...
18 KB (1,693 words) - 05:05, 9 November 2024
Trojan horse Antivirus software Computer insecurity Cryptovirology Security through obscurity Cyberwarfare Computer worm Spyware Virus hoax Zombie computer...
17 KB (423 words) - 20:11, 5 October 2024
technical. Usable security also sits opposite the idea of security through obscurity by working to ensure that users are aware of the security implications...
7 KB (801 words) - 17:30, 1 September 2024
application security is based on the premise that any application or service (whether it is malware or desirable) relies on security through obscurity. Open...
4 KB (370 words) - 14:17, 21 November 2024
forum for disseminating advisories, explains "We don't believe in security by obscurity, and as far as we know, full disclosure is the only way to ensure...
15 KB (1,594 words) - 10:35, 3 November 2024
speaker at the security conference SAINTCON 2021, where he lambasted locksmiths' complacency and reliance on security through obscurity. LockPickingLawyer...
7 KB (587 words) - 09:00, 8 November 2024
MAC filtering (redirect from Port security (networking))
using that address. MAC address filtering can be considered as security through obscurity because the effectiveness is based on "the secrecy of the implementation...
3 KB (328 words) - 04:11, 25 September 2024
of steganography that lack a formal shared secret are forms of security through obscurity, while key-dependent steganographic schemes try to adhere to Kerckhoffs's...
52 KB (6,073 words) - 11:50, 21 November 2024
SCADA (redirect from SCADA Security)
networks The belief that SCADA systems have the benefit of security through obscurity through the use of specialized protocols and proprietary interfaces...
39 KB (4,703 words) - 15:12, 19 November 2024
Security engineering is the process of incorporating security controls into an information system so that the controls become an integral part of the...
13 KB (1,188 words) - 21:28, 20 October 2024
secret algorithm, technique, or device; this is categorized as security through obscurity. Criticisms of this are twofold. First, a 19th century rule known...
5 KB (545 words) - 17:56, 14 November 2024
His ideas were the basis for many modern security practices, and followed that security through obscurity is a bad practice. Simply making source code...
8 KB (1,027 words) - 01:13, 27 January 2024
Obfuscation (section Network security)
is sometimes referred to as "talking around" and is a form of security through obscurity. A notable example of obfuscation of written communication is...
7 KB (825 words) - 20:47, 1 November 2024
this way, soft zoning is similar to the computing concept of security through obscurity. In contrast, hard zoning restricts actual communication across...
3 KB (516 words) - 19:43, 22 May 2024
DREAD (risk assessment model) (category Computer security)
different issues. Some security experts feel that including the "Discoverability" element as the last D rewards security through obscurity, so some organizations...
3 KB (273 words) - 01:28, 25 April 2024
ASCF fell into obscurity, and other organizations continued to promote the slogan. The Heritage Foundation and the Center for Security Policy (CSP) have...
24 KB (2,102 words) - 22:01, 19 November 2024
drives. As a closed source product, Share partially relies on security through obscurity. Like many other P2P applications, Share downloads files in blocks...
11 KB (1,131 words) - 21:57, 25 July 2023
system in use. Since cryptographic security should never depend on the obscurity of either (see security through obscurity, specifically both Shannon's Maxim...
12 KB (1,544 words) - 06:28, 11 November 2024
a tendency of manufacturers to adopt a "security through obscurity" methodology rather than robust security methods. He also argued that as functions...
18 KB (1,947 words) - 14:10, 26 October 2024
Free software (redirect from Security of free software)
debate over the security of free software in comparison to proprietary software, with a major issue being security through obscurity. A popular quantitative...
52 KB (5,522 words) - 10:13, 21 November 2024
Need to know (category Computer security procedures)
privilege – Security by granting only essential access Security through obscurity – Reliance on design or implementation secrecy for security Feynman, Richard...
6 KB (774 words) - 15:13, 28 August 2024
belong to the family of algorithms called A5. Due to the policy of security through obscurity, it has not been possible to openly test the robustness of these...
90 KB (10,980 words) - 14:47, 5 November 2024