In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable...
100 KB (11,581 words) - 21:08, 30 September 2024
The Bluetooth Low Energy denial of service attacks are a series of denial-of-service attacks against mobile phones and iPads via Bluetooth Low Energy...
4 KB (413 words) - 13:04, 23 May 2024
ReDoS (redirect from Regular expression Denial of Service - ReDoS)
A regular expression denial of service (ReDoS) is an algorithmic complexity attack that produces a denial-of-service by providing a regular expression...
16 KB (1,762 words) - 07:31, 2 June 2024
computer security, a billion laughs attack is a type of denial-of-service (DoS) attack which is aimed at parsers of XML documents. It is also referred...
7 KB (870 words) - 02:43, 7 September 2024
Distributed denial-of-service attacks on root nameservers are Internet events in which distributed denial-of-service attacks target one or more of the thirteen...
8 KB (911 words) - 11:37, 1 July 2024
A Wi-Fi deauthentication attack is a type of denial-of-service attack that targets communication between a user and a Wi-Fi wireless access point. Unlike...
9 KB (873 words) - 17:00, 14 June 2024
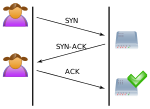
SYN flood (redirect from SYN attack)
A SYN flood is a form of denial-of-service attack on data communications in which an attacker rapidly initiates a connection to a server without finalizing...
4 KB (430 words) - 19:29, 16 October 2023
A Smurf attack is a distributed denial-of-service attack in which large numbers of Internet Control Message Protocol (ICMP) packets with the intended victim's...
9 KB (1,269 words) - 13:35, 2 October 2024
Evernote (section Denial-of-service attacks)
The service has experienced several cases of losing customer data. On June 11, 2014, Evernote suffered a distributed denial-of-service attack that prevented...
38 KB (3,105 words) - 00:43, 17 September 2024
held that the sole purpose of the worm was to perpetrate a distributed denial-of-service attack against SCO Group. 25 percent of Mydoom.A-infected hosts...
15 KB (1,633 words) - 07:00, 17 August 2024
Cyberwarfare (redirect from Cyber security attack)
consequences. In computing, a denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a machine...
149 KB (15,869 words) - 15:57, 26 September 2024
distributed denial-of-service attacks were launched against the Domain Name System (DNS) provider Dyn. The attack caused major Internet platforms and services to...
23 KB (1,617 words) - 13:49, 9 May 2024
Slowloris is a type of denial of service attack tool which allows a single machine to take down another machine's web server with minimal bandwidth and...
17 KB (1,456 words) - 21:10, 30 September 2024
A UDP flood attack is a volumetric denial-of-service (DoS) attack using the User Datagram Protocol (UDP), a sessionless/connectionless computer networking...
3 KB (383 words) - 02:42, 25 April 2024
much of the loot as he could carry. Denial-of-service attack Digest access authentication Man-in-the-middle attack Pre-play attack Relay attack Session...
15 KB (2,103 words) - 18:02, 2 October 2024
(CVE-2002-20001) disclosed a denial-of-service attack (DoS) against the protocol variants use ephemeral keys, called D(HE)at attack. The attack exploits that the...
47 KB (5,184 words) - 10:44, 29 September 2024
Zombie (computing) (category Denial-of-service attacks)
such as spreading e-mail spam and launching distributed denial-of-service attacks (DDoS attacks) against web servers. Most victims are unaware that their...
8 KB (920 words) - 07:58, 26 April 2024
system. They are a form of denial-of-service attack but are different from distributed denial-of-service attacks, which involve overwhelming a network...
2 KB (231 words) - 15:18, 7 January 2024
Trinoo (category Denial-of-service attacks)
trinoo attacks are described in CERT Incident Note 99–04. A trinoo network has been connected to the February 2000 distributed denial of service attack on...
4 KB (375 words) - 11:34, 24 July 2022
High Orbit Ion Cannon (category Denial-of-service attacks)
(HOIC) is an open-source network stress testing and denial-of-service attack application designed to attack as many as 256 URLs at the same time. It was designed...
16 KB (1,747 words) - 15:58, 5 July 2024
Email bomb (category Denial-of-service attacks)
mailbox, overwhelm the server where the email address is hosted in a denial-of-service attack or as a smoke screen to distract the attention from important email...
9 KB (1,074 words) - 15:08, 28 July 2024
Computer security (redirect from Car cyber attack)
firewall rule, many forms of distributed denial-of-service (DDoS) attacks are possible, where the attack comes from a large number of points. In this case...
219 KB (22,241 words) - 18:23, 29 September 2024
Stresser (category Denial-of-service attacks)
Stresser (or booter) services provide denial-of-service attack as a service, usually as a criminal enterprise. They have simple front ends, and accept...
4 KB (360 words) - 10:58, 2 March 2024
normal traffic fails to reach the system (a basic denial-of-service attack). The ping of death attack has been largely neutralized by advancements in technology...
9 KB (1,145 words) - 15:00, 5 July 2024
Spybot worm (section Denial of service attack)
antispyware software. Early detection of the Spybot worm usually comes from network engineers detecting the Denial of Service attack generated when the worm tried...
2 KB (313 words) - 22:22, 22 January 2024
Ferguson & D. Senie (May 2000). Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing]. doi:10.17487/RFC2827...
9 KB (1,275 words) - 03:38, 31 July 2024
CyberBunker (category Denial-of-service attacks)
exceptionally large distributed denial of service attack launched against them in March 2013. Because of the size of this attack it received considerable mainstream...
26 KB (2,298 words) - 12:12, 20 July 2024
Freedom Hosting (category Defunct Tor hidden services)
activities on the dark web. One of the largest sites, Lolita City, hosted by Freedom Hosting, was subject to a denial-of-service attack (DDoS), and later had its...
15 KB (1,295 words) - 15:56, 18 April 2024
becomes the prominent victim of a new type of hack that attacks the domain name server. In these denial-of-service attacks, the DNS paths that take users...
148 KB (15,340 words) - 21:36, 29 September 2024
Black fax (category Denial-of-service attacks)
as well as denying the recipient use of their own machine (similar to computer-based denial of service attacks). This is made easier because fax transmission...
4 KB (433 words) - 13:09, 7 January 2024