cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known...
9 KB (1,139 words) - 01:27, 4 April 2024
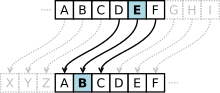
In cryptography, ciphertext stealing (CTS) is a general method of using a block cipher mode of operation that allows for processing of messages that are...
17 KB (2,269 words) - 14:13, 13 January 2024
A chosen-ciphertext attack (CCA) is an attack model for cryptanalysis where the cryptanalyst can gather information by obtaining the decryptions of chosen...
9 KB (1,105 words) - 16:37, 29 July 2024
Ciphertext indistinguishability is a property of many encryption schemes. Intuitively, if a cryptosystem possesses the property of indistinguishability...
15 KB (1,940 words) - 15:32, 17 July 2024
Block cipher mode of operation (redirect from Ciphertext feedback mode)
be random. The initialization vector is used to ensure that distinct ciphertexts are produced even when the same plaintext is encrypted multiple times...
52 KB (5,878 words) - 12:53, 24 August 2024
Some famous ciphertexts (or cryptograms), in chronological order by date, are: Undeciphered writing systems (cleartext, natural-language writing of unknown...
5 KB (76 words) - 06:32, 8 August 2024
chosen-ciphertext attack (abbreviated as CCA2) is an interactive form of chosen-ciphertext attack in which an attacker first sends a number of ciphertexts to...
6 KB (728 words) - 21:17, 24 July 2024
Encryption (redirect from Ciphertexts)
the information, known as plaintext, into an alternative form known as ciphertext. Despite its goal, encryption does not itself prevent interference but...
34 KB (3,646 words) - 05:09, 26 August 2024
In cryptography, a ciphertext-only attack (COA) or known ciphertext attack is an attack model for cryptanalysis where the attacker is assumed to have access...
5 KB (665 words) - 12:17, 5 September 2023
usually contain more repeated ciphertext segments. The following ciphertext has two segments that are repeated: Ciphertext: VHVSSPQUCEMRVBVBBBVHVSURQGI...
45 KB (5,937 words) - 16:44, 25 August 2024
corresponding bit or character from the pad using modular addition. The resulting ciphertext will be impossible to decrypt or break if the following four conditions...
57 KB (7,618 words) - 17:20, 19 July 2024
having a decoding device. A message-to-be-transferred is enciphered to ciphertext at the encoding terminal by encoding the message as a number M in a predetermined...
61 KB (7,877 words) - 15:19, 2 August 2024
first converting it into an unreadable form ("ciphertext") using an encryption algorithm. The ciphertext is sent through an insecure channel to the recipient...
44 KB (5,202 words) - 13:26, 19 August 2024
"cipher" line. Plaintext: THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG Ciphertext: QEB NRFZH YOLTK CLU GRJMP LSBO QEB IXWV ALD Deciphering is done in reverse...
19 KB (2,031 words) - 00:56, 12 August 2024
method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with the help of a key; the "units" may be single...
30 KB (4,021 words) - 22:15, 14 July 2024
authenticity protection. Output: ciphertext and authentication tag (message authentication code or MAC). Decryption Input: ciphertext, key, authentication tag...
19 KB (2,075 words) - 19:58, 14 August 2024
In cryptography, the term ciphertext expansion refers to the length increase of a message when it is encrypted. Many modern cryptosystems cause some degree...
3 KB (337 words) - 03:11, 18 July 2024
cryptographic keys for both the encryption of plaintext and the decryption of ciphertext. The keys may be identical, or there may be a simple transformation to...
15 KB (1,544 words) - 02:53, 7 June 2024
the plaintext using the key to produce ciphertext C, and computes an authentication tag T from the ciphertext and the associated data (which remains unencrypted)...
23 KB (2,999 words) - 05:42, 12 June 2024
with the corresponding digit of the keystream, to give a digit of the ciphertext stream. Since encryption of each digit is dependent on the current state...
23 KB (2,213 words) - 15:26, 19 August 2024
characters or groups of characters) according to a regular system to produce a ciphertext which is a permutation of the plaintext. They differ from substitution...
25 KB (3,604 words) - 03:23, 21 March 2024
QUEENLYATTACKATDAWN. Plaintext: attackatdawn Key: QUEENLYATTACKATDAWN Ciphertext: QNXEPVYTWTWP The ciphertext message would thus be "QNXEPVYTWTWP". To decrypt the message...
9 KB (1,276 words) - 15:02, 26 January 2024
letters) is the study of the frequency of letters or groups of letters in a ciphertext. The method is used as an aid to breaking classical ciphers. Frequency...
16 KB (1,663 words) - 06:05, 8 April 2024
letters as the ciphertext output. This is done by creating an "alphabet" of words (in practice multiple words can correspond to each ciphertext output character)...
10 KB (1,294 words) - 19:13, 30 July 2024
print('Key:', key) cipherText = xor_strings(message.encode('utf8'), key) print('cipherText:', cipherText) print('decrypted:', xor_strings(cipherText, key).decode('utf8'))...
9 KB (1,033 words) - 16:06, 30 December 2023
access to both the plaintext (called a crib) and its encrypted version (ciphertext). These can be used to reveal secret keys and code books. The term "crib"...
10 KB (1,286 words) - 22:00, 7 January 2024
into a ciphertext block of 128 bits in size. The key, which is given as one input to the cipher, defines the mapping between plaintext and ciphertext. If...
14 KB (1,785 words) - 20:10, 11 August 2024
converting readable information (plaintext) to unintelligible nonsense text (ciphertext), which can only be read by reversing the process (decryption). The sender...
98 KB (10,713 words) - 13:13, 22 August 2024
model for cryptanalysis which presumes that the attacker can obtain the ciphertexts for arbitrary plaintexts. The goal of the attack is to gain information...
11 KB (1,435 words) - 00:47, 29 December 2023
read M2. Bob forwards the ciphertext to Carl. Carl uses his key to decrypt M2 and isn't able to read M1. Normally, ciphertexts decrypt to a single plaintext...
24 KB (2,832 words) - 14:59, 17 August 2024