In computer science, a mask or bitmask is data that is used for bitwise operations, particularly in a bit field. Using a mask, multiple bits in a byte...
12 KB (1,736 words) - 15:23, 20 October 2024
refer to: Mask (computing), in computer science, a bit pattern used to extract information from another bit pattern Affinity mask, a bit mask indicating...
4 KB (533 words) - 04:10, 20 August 2024
Bit blit (redirect from Blit (computing))
on. This technique is known as dirty rectangles. Alpha compositing Mask (computing), used here as a stencil Blitter Sanchez, Julio; Maria P. Canton (2007)...
7 KB (962 words) - 23:32, 3 September 2024
by another Temporal masking Simultaneous masking Visual masking Backward masking, in psychovisual or psychoacoustics Mask (computing), AND'ing or OR'ing...
2 KB (281 words) - 14:50, 6 May 2023
Word (computer architecture) – Base memory unit handled by a computer Mask (computing) – Data used for bitwise operations Program status word – control register...
12 KB (1,515 words) - 16:40, 29 July 2024
Umask (redirect from File mode creation mask)
In computing, umask is a command that determines the settings of a mask that controls how file permissions are set for newly created files. It may also...
20 KB (1,754 words) - 10:32, 22 June 2024
Interrupt (redirect from Interrupt mask)
implement computer multitasking and system calls, especially in real-time computing. Systems that use interrupts in these ways are said to be interrupt-driven...
42 KB (5,507 words) - 22:53, 21 September 2024
Computing is any goal-oriented activity requiring, benefiting from, or creating computing machinery. It includes the study and experimentation of algorithmic...
51 KB (5,368 words) - 20:03, 5 November 2024
parallel computing: bit-level, instruction-level, data, and task parallelism. Parallelism has long been employed in high-performance computing, but has...
74 KB (8,506 words) - 22:33, 21 September 2024
Data Mask or similar may mean: In computer science, "data mask" is another name for mask (computing), a bit pattern used to extract information from another...
294 bytes (79 words) - 22:31, 6 June 2013
Computer (redirect from Computing device)
of the analytical engine's computing unit (the mill) in 1888. He gave a successful demonstration of its use in computing tables in 1906. In his work...
138 KB (13,984 words) - 04:01, 6 November 2024
Internet Control Message Protocol (redirect from ICMP Address Mask Request)
with an Address mask reply message. Where: Type must be set to 17 Code must be set to 0 Address mask can be set to 0 ICMP Address Mask Request may be used...
31 KB (2,877 words) - 23:05, 15 October 2024
encoded in the alpha channel of an RGBA texture used for coloring instead of being a standalone greyscale texture. Mask (computing)#Image masks v t e...
934 bytes (115 words) - 16:14, 18 February 2023
Optical computing or photonic computing uses light waves produced by lasers or incoherent sources for data processing, data storage or data communication...
31 KB (3,432 words) - 17:11, 22 September 2024
The history of computing is longer than the history of computing hardware and modern computing technology and includes the history of methods intended...
59 KB (6,591 words) - 22:49, 29 October 2024
Security-focused operating system Security-Enhanced Linux "Hardening Your Computing Assets" (PDF). at globalsecurity.org "CIS Benchmark List". at globalsecurity...
3 KB (279 words) - 06:55, 29 August 2024
the U.S., spammers hop through open relays across political boundaries to mask their origin. Honeypot operators may use intercepted relay tests to recognize...
28 KB (3,253 words) - 17:37, 2 November 2024
creat(), and other operating system calls to provide their own permission masks and not to depend on the umask of the caller. Redirecting file descriptors...
11 KB (1,340 words) - 00:42, 3 October 2024
This is a list of computing and IT acronyms, initialisms and abbreviations. 0–9 A B C D E F G H I J K L M N O P Q R S T U V W X Y Z See also References...
92 KB (6,571 words) - 19:15, 31 October 2024
There can be many possible maskers at the same frequency. In this situation, it would be necessary to compute the global masking threshold using a high resolution...
3 KB (413 words) - 00:25, 15 October 2024
Read-only memory (redirect from Mask ROM)
read-only memory refers to hard-wired memory, such as diode matrix or a mask ROM integrated circuit (IC), that cannot be electronically changed after...
48 KB (5,573 words) - 14:57, 26 September 2024
In computing, a non-maskable interrupt (NMI) is a hardware interrupt that standard interrupt-masking techniques in the system cannot ignore. It typically...
8 KB (995 words) - 00:34, 30 September 2024
high computing performance. It was acquired by Hewlett-Packard in 2006, and began changing its brand name to Omen in 2014 using the same tribal mask logo...
5 KB (395 words) - 06:31, 9 July 2024
HCF, shows up as "Overextended Mnemonics" in the April 1980 Creative Computing flip-side parody issue. CPU designers sometimes incorporate one or more...
26 KB (2,674 words) - 02:40, 9 October 2024
Content-addressable memory (redirect from CAM (computing))
the binary CAM. This additional state is typically implemented by adding a mask bit (care or don't care bit) to every memory cell. In 2013, IBM fabricated...
14 KB (1,603 words) - 03:32, 27 September 2024
In computing, load balancing is the process of distributing a set of tasks over a set of resources (computing units), with the aim of making their overall...
46 KB (6,265 words) - 00:57, 20 September 2024
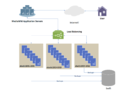
Data masking or data obfuscation is the process of modifying sensitive data in such a way that it is of no or little value to unauthorized intruders while...
22 KB (3,095 words) - 11:55, 26 March 2024
Hacker (redirect from Hacker (computing))
This could include using anonymity tools (such as a VPN or the dark web) to mask their identities online and pose as criminals. Hacking can also have a broader...
40 KB (4,246 words) - 17:34, 18 October 2024
AVX-512 (category SIMD computing)
The number of AVX registers is increased from 16 to 32, and eight new "mask registers" are added, which allow for variable selection and blending of...
87 KB (4,713 words) - 05:57, 9 October 2024
FLAGS register (redirect from Flags (computing))
registers retain compatibility with their smaller predecessors. Note: The mask column in the table is the AND bitmask (as hexadecimal value) to query the...
9 KB (805 words) - 10:31, 11 March 2024