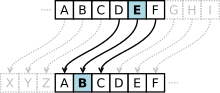
The Playfair cipher or Playfair square or Wheatstone–Playfair cipher is a manual symmetric encryption technique and was the first literal digram substitution...
20 KB (2,502 words) - 18:18, 12 September 2024
The Two-square cipher, also called double Playfair, is a manual symmetric encryption technique. It was developed to ease the cumbersome nature of the...
11 KB (1,673 words) - 19:08, 29 June 2024
succeeded by Hymn Playfair Project TS Playfair, a Canadian sail training vessel Playfair's axiom named after John Playfair Playfair cipher, a manual encryption...
917 bytes (159 words) - 04:58, 14 October 2023
bigram plaintext statistics. Other ciphers by Delastelle: four-square cipher (related to Playfair) trifid cipher (similar to bifid) "Practical Cryptography"...
3 KB (379 words) - 10:35, 3 September 2024
practical digraphic cipher (pairwise substitution), was the so-called Playfair cipher, invented by Sir Charles Wheatstone in 1854. In this cipher, a 5 x 5 grid...
30 KB (4,047 words) - 18:46, 28 October 2024
attempt to uncover the ciphertext matrices. Unlike the Playfair cipher, a four-square cipher will not show reversed ciphertext digraphs for reversed...
8 KB (1,528 words) - 04:51, 29 June 2024
ciphers, some of these ciphers are the Hill Cipher and Playfair Cipher. Homophonic ciphers can be decrypted to multiple messages. Ciphers that include multiple...
12 KB (1,236 words) - 18:24, 18 October 2024
Other practical "pencil-and-paper" polygraphic ciphers include: Playfair cipher Bifid cipher Trifid cipher Lester S. Hill, Cryptography in an Algebraic...
13 KB (2,241 words) - 21:56, 17 October 2024
said to have rejected the Playfair cipher because, even if school boys could cope successfully as Wheatstone and Playfair had shown, "our attachés could...
16 KB (1,663 words) - 06:05, 8 April 2024
1897. Playfair is also remembered for promoting a new cipher system invented by Charles Wheatstone, now known as the Playfair cipher. Lord Playfair died...
17 KB (1,556 words) - 05:49, 12 September 2024
Ciphertext (redirect from Cipher text)
substitution cipher: the unit of substitution is a sequence of two or more letters rather than just one (e.g., Playfair cipher) Transposition cipher: the ciphertext...
9 KB (1,139 words) - 23:45, 27 October 2024
The Vigenère cipher (French pronunciation: [viʒnɛːʁ]) is a method of encrypting alphabetic text where each letter of the plaintext is encoded with a different...
45 KB (5,937 words) - 19:57, 13 November 2024
Polygraphic substitution (section Specific ciphers)
falling into enemy hands. In 1854, Charles Wheatstone came up with the Playfair cipher, a keyword-based system that could be performed on paper in the field...
4 KB (580 words) - 07:39, 19 February 2023
polygraphic substitution ciphers included the trifid and four-square ciphers. The last of these is a variant on the earlier Playfair cipher: Delastelle may have...
2 KB (304 words) - 07:27, 1 April 2024
In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code, or Caesar shift, is one of the simplest and most widely...
19 KB (2,058 words) - 14:38, 20 October 2024
stereoscope (a device for displaying three-dimensional images), and the Playfair cipher (an encryption technique). However, Wheatstone is best known for his...
47 KB (6,398 words) - 16:15, 17 August 2024
substitution ciphers, including the Bacon cipher and Polybius square, before moving on to transposition ciphers, Playfair ciphers and polyalphabetic ciphers such...
4 KB (507 words) - 09:22, 5 July 2023
Playfair cipher Polyalphabetic substitution Polybius square ROT13, ROT47 Scytale Steganography Substitution cipher Tabula recta Transposition cipher Vigenère...
2 KB (154 words) - 22:12, 20 September 2023
message copied into Booth's diary. Thomas recognizes the message as a Playfair cipher, and translates it while Booth departs for Ford's Theatre to assassinate...
33 KB (3,608 words) - 04:37, 5 October 2024
pigpen cipher (alternatively referred to as the masonic cipher, Freemason's cipher, Rosicrucian cipher, Napoleon cipher, and tic-tac-toe cipher) is a geometric...
11 KB (1,303 words) - 21:54, 22 October 2024
Jim Lyon Playfair, 1st Baron Playfair (1818–1898), promoter of the Playfair cipher, manual symmetric encryption technique Sir Nigel Playfair (1874–1934)...
2 KB (316 words) - 00:02, 23 May 2023
double Transposition cipher (German: Doppelwürfel) 4-S-40 This system was used until 1926 or 1927 The Playfair cipher in Single Playfair (German: Kastenschlüssel)...
31 KB (4,418 words) - 22:28, 4 November 2024
null cipher, also known as concealment cipher, is an ancient form of encryption where the plaintext is mixed with a large amount of non-cipher material...
11 KB (1,496 words) - 22:12, 28 June 2024
Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. In steganograhy, a message is concealed...
8 KB (775 words) - 13:36, 18 October 2024
The rail fence cipher (also called a zigzag cipher) is a classical type of transposition cipher. It derives its name from the manner in which encryption...
7 KB (1,103 words) - 16:01, 16 September 2023
In cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. In contrast to modern...
15 KB (2,528 words) - 02:24, 15 June 2024
In cryptography, a transposition cipher (also known as a permutation cipher) is a method of encryption which scrambles the positions of characters (transposition)...
25 KB (3,604 words) - 15:23, 5 November 2024
Enigma machine (redirect from Enigma cipher machine)
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication...
92 KB (11,246 words) - 09:07, 15 November 2024
Bell Labs. In 1914 he published the first recorded solution of the Playfair cipher. Mauborgne became a Major General in the United States Army, and from...
9 KB (887 words) - 20:25, 23 April 2024
A book cipher is a cipher in which each word or letter in the plaintext of a message is replaced by some code that locates it in another text, the key...
14 KB (1,947 words) - 09:19, 9 November 2024