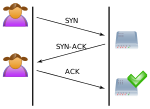
A SYN flood is a form of denial-of-service attack on data communications in which an attacker rapidly initiates a connection to a server without finalizing...
4 KB (430 words) - 19:29, 16 October 2023
SYN cookie is a technique used to resist SYN flood attacks. The technique's primary inventor Daniel J. Bernstein defines SYN cookies as "particular choices...
9 KB (1,213 words) - 05:13, 18 July 2024
Denial-of-service attack (redirect from Network flood)
be the first DoS attack. On September 6, 1996, Panix was subject to a SYN flood attack, which brought down its services for several days while hardware...
101 KB (11,660 words) - 02:06, 19 November 2024
Transmission Control Protocol (redirect from SYN (TCP))
This is known as a SYN flood attack. Proposed solutions to this problem include SYN cookies and cryptographic puzzles, though SYN cookies come with their...
109 KB (12,956 words) - 22:36, 15 November 2024
The Tribe Flood Network or TFN is a set of computer programs to conduct various DDoS attacks such as ICMP flood, SYN flood, UDP flood and Smurf attack...
2 KB (85 words) - 06:45, 19 August 2023
traffic filtering security feature that protects TCP servers from TCP SYN flood attacks, which are a type of denial-of-service attack. TCP Intercept is...
47 KB (5,573 words) - 13:08, 16 November 2024
discovered in underground forums in May 2012. Zemra is capable of HTTP and SYN Flood flooding and also has a simple Command & Control panel that is protected with...
3 KB (220 words) - 21:46, 27 August 2024
connection is fully open. Both endpoints are now in an established state. SYN flood SYN cookies Stateful firewall Transmission Control Protocol DARPA Internet...
3 KB (386 words) - 04:30, 25 September 2024
set when the system is considered to be under attack.[failed verification] SYN flood "PUSH and ACK Flood". Archived from the original on 2022-04-07....
886 bytes (73 words) - 21:19, 3 March 2024
different denial-of-service (DoS) attack methods, including Ping flood, UDP flood, TCP SYN flood, and Smurf attack. Further, it can detect and automatically...
3 KB (180 words) - 03:32, 29 May 2024
did not see as much media attention. The worm was programmed to start a SYN flood against port 80 of windowsupdate.com if the system date is after August...
18 KB (1,741 words) - 10:19, 29 September 2024
virus) 1260 (computer virus) SCA (computer virus) ReDoS SYN flood Billion laughs attack UDP flood attack Wi-Fi deauthentication attack Smurf attack Mydoom...
19 KB (1,781 words) - 14:01, 4 September 2024
(2022-06-30). "G-Core Labs' stand-alone solution offers protection against SYN Flood DDoS attacks". Help Net Security. Retrieved 2023-04-06. PDF. "G-Core Labs:...
9 KB (719 words) - 19:44, 7 November 2024
Unfortunately, this initial effort had to be suspended as the result of SYN flood attacks by participants upon the server. A new independent effort, named...
17 KB (1,564 words) - 15:26, 20 September 2024
(syssrv.sys) DDoS attack commands (e.g. ICMP flood, TCP SYN flood, UDP flood, HTTP get flood, DNS flood, etc.)[clarification needed] Download commands...
7 KB (760 words) - 18:20, 8 November 2024
internet access. Panix was one of the first sites to identify the 1996 SYN flood Denial of service. In 2005, the "panix.com" domain name was hijacked over...
3 KB (248 words) - 09:22, 17 November 2024
to reply to itself continuously. It is, however, distinct from the TCP SYN Flood vulnerability. Other LAND attacks have since been found in services like...
3 KB (350 words) - 18:40, 2 November 2024
Provisioning Services, better IPv6 support, and new protections against SYN flood TCP attacks. Post-Setup Security Updates, a panel which is shown only...
61 KB (5,988 words) - 14:24, 21 October 2024
such as SYN cookies and delayed-binding (the back-end servers don't see the client until it finishes its TCP handshake) to mitigate SYN flood attacks...
46 KB (6,265 words) - 00:57, 20 September 2024
"Syn attack protection on Windows Vista, Windows 2008, Windows 7, Windows 2008 R2, Windows 8/8.1, Windows 2012 and Windows 2012 R2". June 2010. SynAttack...
74 KB (1,235 words) - 22:37, 14 November 2024
attacks from reaching their targets. Free and open-source software portal SYN flood Aircrack BackTrack Nmap Packet sniffer Snort Wireshark Bellovin, S.M....
4 KB (540 words) - 07:52, 9 October 2024
messages that can be forged or state that can be misused, like that in a SYN flood. The synchronization mechanism also makes aberrant behavior more correlated...
31 KB (4,124 words) - 15:48, 14 November 2024
4-way handshake (compared to TCP 3-way handshake) to protect against SYN flooding attacks, and large "cookies" for association verification and authenticity...
23 KB (2,466 words) - 07:42, 3 November 2024
until late in the day. Other groups using supercomputers withdrew after SYN flood attacks on their networks.[citation needed] With the software that was...
4 KB (549 words) - 01:46, 17 October 2023
IMPACT Cybertrust. in the case of a TCP SYN flood attack with a spoofed source IP, the victim will reply with a TCP SYN-ACK to the spoofed IP; if the spoofed...
15 KB (1,442 words) - 19:25, 15 October 2024
Coastal flooding occurs when dry and low-lying land is submerged (flooded) by seawater. The range of a coastal flooding is a result of the elevation of...
33 KB (4,592 words) - 23:03, 12 September 2024
timing out half open connections with greater hostility. One can also set SYN, ICMP, and UDP at lower levels to prevent such DDoS attacks from harming...
2 KB (255 words) - 02:27, 20 March 2024
network layer attacks including Denial of Service (DoS) from ICMP and SYN floods. As a result, the ADN must necessarily protect not only itself but the...
17 KB (2,327 words) - 16:14, 6 July 2024