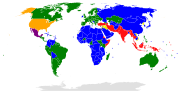
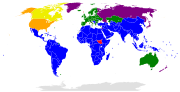
Protocol I (also Additional Protocol I and AP I) is a 1977 amendment protocol to the Geneva Conventions concerning the protection of civilian victims...
30 KB (1,911 words) - 23:03, 26 December 2024
Geneva Convention Fourth Geneva Convention Additional Protocols Protocol I Protocol II Protocol III The four 1949 Conventions have been ratified by 196...
39 KB (1,822 words) - 00:06, 11 December 2024
Mission: Impossible – Ghost Protocol is a 2011 American action spy film directed by Brad Bird (in his live-action directorial debut) from a screenplay...
68 KB (5,566 words) - 11:51, 25 December 2024
some of the five protocols, with two being the minimum required to be considered a party. The convention has five protocols: Protocol I restricts weapons...
23 KB (1,747 words) - 23:05, 9 December 2024
coherency protocols for cache memory are listed here. For simplicity, all "miss" Read and Write status transactions which obviously come from state "I" (or...
61 KB (7,280 words) - 02:49, 27 November 2024
Indiscriminate attack (section Protocol I)
Indiscriminate attacks are prohibited both by the Geneva Conventions Additional Protocol I (1977) and by customary international humanitarian law. They constitute...
45 KB (5,056 words) - 23:06, 21 November 2024
Interior Border Gateway Protocol (iBGP). In contrast, the Internet application of the protocol is called Exterior Border Gateway Protocol (EBGP). The genesis...
65 KB (7,969 words) - 16:02, 20 December 2024
This is a list of the IP protocol numbers found in the field Protocol of the IPv4 header and the Next Header field of the IPv6 header. It is an identifier...
20 KB (120 words) - 14:04, 21 December 2024
The Kyoto Protocol (Japanese: 京都議定書, Hepburn: Kyōto Giteisho) was an international treaty which extended the 1992 United Nations Framework Convention on...
154 KB (13,538 words) - 23:03, 26 December 2024
Protocol 1, First Protocol, or Additional Protocol may refer to: Protocol I to the Geneva Conventions Protocol 1 to the European Convention on Human Rights...
433 bytes (75 words) - 20:08, 18 May 2024
Protocol II is a 1977 amendment protocol to the Geneva Conventions relating to the protection of victims of non-international armed conflicts. It defines...
20 KB (653 words) - 23:03, 26 December 2024
Geneva Conventions (section Protocols)
international humanitarian laws consisting of four treaties and three additional protocols that establish international legal standards for humanitarian treatment...
72 KB (7,426 words) - 13:22, 24 December 2024
Two Additional Protocols were adopted in 1977 with the third one added in 2005, completing and updating the Geneva Conventions: Protocol I (1977) relating...
57 KB (5,908 words) - 01:05, 30 December 2024
Right to property (redirect from ECHR Protocol 1, article 1)
states enshrined the right to protection of property in Article 1 of Protocol I to the ECHR as the "right to peaceful enjoyment of possessions", where...
29 KB (3,868 words) - 22:57, 19 November 2024
Injurious or to Have Indiscriminate Effects (CCW) 1980 Protocol I on Non-Detectable Fragments 1980 Protocol II on Prohibitions or Restrictions on the Use of...
47 KB (5,729 words) - 07:03, 26 November 2024
the definition of "combatant" is found in Article 43 (2) of Additional Protocol I to the 1949 Geneva Conventions: "Members of the armed forces of a Party...
13 KB (1,650 words) - 14:42, 15 November 2024
surrender is a type of perfidy in the context of war. It is a war crime under Protocol I of the Geneva Convention. False surrenders are usually used to draw the...
10 KB (1,096 words) - 04:41, 7 December 2024
HTTP (redirect from Http protocol)
HTTP (Hypertext Transfer Protocol) is an application layer protocol in the Internet protocol suite model for distributed, collaborative, hypermedia information...
61 KB (7,773 words) - 03:15, 12 December 2024
1977 Protocol I Additional to the Geneva Conventions of 12 August 1949, which states: Wikisource has original text related to this article: Protocol I of...
12 KB (1,540 words) - 01:39, 26 December 2024
A communication protocol is a system of rules that allows two or more entities of a communications system to transmit information via any variation of...
65 KB (8,221 words) - 14:26, 31 December 2024
protected because of their specific duties (as currently described in Protocol I of the Geneva Conventions, adopted in June 1977); combatants who are placed...
19 KB (2,203 words) - 04:58, 24 November 2024
Third Convention and in Article 43 of the Protocol I are combatants. Therefore, the Commentary to the Protocol pointed that anyone who is not a member of...
33 KB (3,831 words) - 21:33, 9 December 2024
detaining power has such a punishment for the crimes they have committed). Protocol I to the Geneva Conventions defines a person as hors de combat if: (a) he...
2 KB (304 words) - 03:45, 25 December 2024
relating to the Protection of Victims of International Armed Conflicts" (Protocol I), combatants who do not wear a distinguishing mark still qualify as prisoners...
86 KB (11,394 words) - 04:31, 27 September 2024
In computer networks, a tunneling protocol is a communication protocol which allows for the movement of data from one network to another. They can, for...
15 KB (1,956 words) - 19:45, 7 December 2024
The File Transfer Protocol (FTP) is a standard communication protocol used for the transfer of computer files from a server to a client on a computer...
34 KB (4,019 words) - 20:33, 11 December 2024
Transport layer (redirect from Transport protocol)
the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. The protocols of this layer provide end-to-end...
16 KB (1,611 words) - 02:26, 18 September 2024
a "protocol". For example, the Kyoto Protocol was supplemental to the United Nations Framework Convention on Climate Change; Protocol I, Protocol II,...
2 KB (196 words) - 08:41, 16 August 2024
civilians has been considered a war crime since 1977, through Article 51 of Protocol I of the Geneva Conventions. The term obliteration bombing is sometimes...
28 KB (3,339 words) - 08:17, 30 November 2024
of Inquiry for the International War Crimes Tribunal. However Geneva Protocol I Article 41.2 states that to be considered "hors de combat" or "out of...
23 KB (2,507 words) - 14:50, 3 December 2024