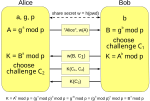
In cryptography, a key-agreement protocol is a protocol whereby two (or more) parties generate a cryptographic key as a function of information provided...
12 KB (1,478 words) - 05:28, 29 October 2024
how public-key cryptography could be achieved. Although Diffie–Hellman key exchange itself is a non-authenticated key-agreement protocol, it provides...
48 KB (5,262 words) - 08:24, 14 November 2024
password-authenticated key agreement (PAK) method is an interactive method for two or more parties to establish cryptographic keys based on one or more...
17 KB (1,799 words) - 23:21, 29 December 2024
cash, password-authenticated key agreement, time-stamping services and non-repudiation protocols. Because asymmetric key algorithms are nearly always...
40 KB (4,512 words) - 00:53, 4 December 2024
Elliptic-curve Diffie–Hellman (category Key-agreement protocols)
Diffie–Hellman (ECDH) is a key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, to establish a shared...
14 KB (2,165 words) - 23:47, 14 December 2024
MQV (category Key-agreement protocols)
MQV (Menezes–Qu–Vanstone) is an authenticated protocol for key agreement based on the Diffie–Hellman scheme. Like other authenticated Diffie–Hellman schemes...
13 KB (1,743 words) - 17:24, 4 September 2024
ZRTP (redirect from Z Real-time Transport Protocol)
(composed of Z and Real-time Transport Protocol) is a cryptographic key-agreement protocol to negotiate the keys for encryption between two end points...
12 KB (1,256 words) - 22:39, 20 October 2024
Authentication and Key Agreement (AKA) is a security protocol used in 3G networks. AKA is also used for one-time password generation mechanism for digest...
3 KB (380 words) - 03:34, 17 April 2022
protocols as well, and even the term itself has various readings; Cryptographic application protocols often use one or more underlying key agreement methods...
9 KB (1,009 words) - 16:37, 1 January 2025
The Secure Remote Password protocol (SRP) is an augmented password-authenticated key exchange (PAKE) protocol, specifically designed to work around existing...
28 KB (3,404 words) - 16:06, 8 December 2024
Skype security (section Key agreement protocol)
public keys are certified by the Skype server at login with 1536-bit or 2048-bit RSA certificates. Skype's encryption is inherent in the Skype Protocol and...
24 KB (2,779 words) - 02:30, 18 August 2024
Encrypted Key Exchange (also known as EKE) is a family of password-authenticated key agreement methods described by Steven M. Bellovin and Michael Merritt...
3 KB (389 words) - 16:17, 17 July 2022
Internet Key Exchange (IKE, versioned as IKEv1 and IKEv2) is the protocol used to set up a security association (SA) in the IPsec protocol suite. IKE...
20 KB (2,352 words) - 18:44, 14 September 2024
In public-key cryptography, the Station-to-Station (STS) protocol is a cryptographic key agreement scheme. The protocol is based on classic Diffie–Hellman...
10 KB (1,213 words) - 17:23, 29 March 2024
Simultaneous Authentication of Equals (category Key-agreement protocols)
knowing the user's password." Extensible Authentication Protocol (EAP) Key-agreement protocol KRACK IEEE 802.1X Harkins, Dan (Aug 20, 2008). "Simultaneous...
6 KB (631 words) - 22:04, 10 November 2024
signing party Key stretching Key-agreement protocol glossary Password psychology Public key fingerprint Random number generator Session key Tripcode Machine-readable...
13 KB (1,506 words) - 19:24, 28 November 2024
Post-Quantum Extended Diffie–Hellman (category Public-key cryptography)
to the Diffie–Hellman key exchange. It is notably being incorporated into the Signal Protocol, an end-to-end encryption protocol. In September 2023, the...
3 KB (266 words) - 22:37, 29 September 2024
delivering secure voice. ZRTP – a cryptographic key-agreement protocol used in Voice over Internet Protocol (VoIP) phone telephony. Telecommunications portal...
5 KB (446 words) - 21:24, 28 August 2024
information (such as public keys) in addition to the message over a secure channel. Such protocols, often using key-agreement protocols, have been developed...
23 KB (2,558 words) - 16:40, 30 December 2024
Signal (software) (section Encryption protocols)
2017, Signal's voice calls were encrypted with SRTP and the ZRTP key-agreement protocol, which was developed by Phil Zimmermann. In March 2017, Signal transitioned...
137 KB (11,757 words) - 21:57, 11 December 2024
(band), an English rock band YAK (cryptography) is a public-key authenticated key agreement protocol Yak (Thailand), a mythical ogre of the Yasha kind Yak (instrument)...
1 KB (203 words) - 14:43, 13 February 2022
Algebraic Eraser (category Key-agreement protocols)
Algebraic Eraser (AE) is an anonymous key agreement protocol that allows two parties, each having an AE public–private key pair, to establish a shared secret...
11 KB (1,622 words) - 23:27, 18 October 2022
Accordingly, key authentication methods are being actively researched. Public-key infrastructure (PKI) Public-key cryptography Key-agreement protocol Access...
4 KB (584 words) - 20:34, 18 October 2024
Forward secrecy (redirect from Key erasure)
specific key-agreement protocols that gives assurances that session keys will not be compromised even if long-term secrets used in the session key exchange...
25 KB (2,976 words) - 20:15, 26 October 2024
Merkle's Puzzles (category Key-agreement protocols)
cryptography, Merkle's Puzzles is an early construction for a public-key cryptosystem, a protocol devised by Ralph Merkle in 1974 and published in 1978. It allows...
5 KB (771 words) - 23:11, 17 February 2024
Authenticated Key Exchange by Juggling (or J-PAKE) is a password-authenticated key agreement protocol, proposed by Feng Hao and Peter Ryan. This protocol allows...
10 KB (1,501 words) - 04:36, 31 July 2024
of Minsk Protocol After the conclusion of Protocol and Memorandum, a fragile ceasefire was established. However, even although the agreement met Russian...
87 KB (8,983 words) - 22:16, 2 January 2025
Shared secret (category Key management)
pre-shared key, or it is created at the start of the communication session by using a key-agreement protocol, for instance using public-key cryptography...
2 KB (239 words) - 22:37, 3 December 2023
One-time password (redirect from One-time key)
Google Authenticator FreeOTP Initiative For Open Authentication Key-agreement protocol KYPS One-time pad Code (cryptography) § One-time code OPIE Authentication...
26 KB (3,542 words) - 05:34, 17 December 2024
The Oakley Key Determination Protocol is a key-agreement protocol that allows authenticated parties to exchange keying material across an insecure connection...
1 KB (128 words) - 06:07, 22 May 2023