cryptography, a password-authenticated key agreement (PAK) method is an interactive method for two or more parties to establish cryptographic keys based on one...
17 KB (1,799 words) - 23:21, 29 December 2024
integrity, authentication, and non-repudiation). Password-authenticated key agreement protocols require the separate establishment of a password (which may...
12 KB (1,478 words) - 05:28, 29 October 2024
of password-authenticated key agreement schemes, and a password-authenticated key retrieval scheme. BPKAS-PAK (Balanced Password-Authenticated Key Agreement...
6 KB (629 words) - 03:54, 31 July 2024
Password-authenticated key agreement protocols etc. Crypto systems using asymmetric key algorithms do not evade the problem either. That a public key can be...
4 KB (584 words) - 20:34, 18 October 2024
The Secure Remote Password protocol (SRP) is an augmented password-authenticated key exchange (PAKE) protocol, specifically designed to work around existing...
28 KB (3,404 words) - 16:06, 8 December 2024
cryptography, Simultaneous Authentication of Equals (SAE) is a password-based authentication and password-authenticated key agreement method. SAE is a variant...
6 KB (631 words) - 22:04, 10 November 2024
Encrypted Key Exchange (also known as EKE) is a family of password-authenticated key agreement methods described by Steven M. Bellovin and Michael Merritt...
3 KB (389 words) - 16:17, 17 July 2022
two-factor authentication (something a user has and something the user knows). Using encrypted tunnels or password-authenticated key agreement to prevent...
79 KB (8,967 words) - 21:49, 30 December 2024
The Password Authenticated Key Exchange by Juggling (or J-PAKE) is a password-authenticated key agreement protocol, proposed by Feng Hao and Peter Ryan...
10 KB (1,501 words) - 04:36, 31 July 2024
password-authenticated key agreement techniques Paillier cryptosystem RSA encryption algorithm (PKCS#1) Cramer–Shoup cryptosystem YAK authenticated key...
40 KB (4,512 words) - 00:53, 4 December 2024
be authenticated. The simplest example of a challenge-response protocol is password authentication, where the challenge is asking for the password and...
11 KB (1,540 words) - 19:04, 12 December 2024
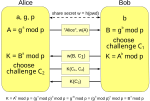
protocols, because of its fast key generation. When Alice and Bob share a password, they may use a password-authenticated key agreement (PK) form of Diffie–Hellman...
48 KB (5,262 words) - 08:24, 14 November 2024
mechanism. Password-authenticated key agreement algorithms can perform a cryptographic key exchange utilizing knowledge of a user's password. Quantum key distribution...
12 KB (1,397 words) - 04:01, 30 November 2024
Authentication and Key Agreement (AKA) is a security protocol used in 3G networks. AKA is also used for one-time password generation mechanism for digest...
3 KB (380 words) - 03:34, 17 April 2022
IEEE P1363.2, in reference to one of the benefits of using a password-authenticated key exchange (PAKE) protocol that is secure against off-line dictionary...
3 KB (331 words) - 14:44, 1 July 2022
password algorithm Two-factor authentication Paterson, Kenneth G.; Stebila, Douglas (2010). "One-Time-Password-Authenticated Key Exchange" (PDF). In Steinfeld...
26 KB (3,542 words) - 05:34, 17 December 2024
SPEKE (redirect from Simple Password Exponential Key Exchange)
SPEKE (Simple Password Exponential Key Exchange) is a cryptographic method for password-authenticated key agreement. The protocol consists of little more...
7 KB (1,005 words) - 19:54, 26 August 2023
protocol Password-authenticated key agreement protocols Protocol for Carrying Authentication for Network Access (PANA) Secure Remote Password protocol...
10 KB (1,192 words) - 23:19, 10 July 2024
Man-in-the-middle attack (section Authentication)
channel. Mutual authentication – how communicating parties establish confidence in one another's identities. Password-authenticated key agreement – a protocol...
23 KB (2,558 words) - 16:40, 30 December 2024
Passphrase (category Password authentication)
Negotiating keys in an interactive setting such as using password-authenticated key agreement Enabling a smart-card or PIN for an ATM card where the password data...
13 KB (1,629 words) - 00:47, 24 December 2024
password. Password Passphrase Password-authenticated key agreement Halevi, Shai; Krawczyk, Hugo (August 1999). "Public-key cryptography and password protocols"...
2 KB (210 words) - 19:42, 15 October 2024
key derivation function (KDF) is a cryptographic algorithm that derives one or more secret keys from a secret value such as a master key, a password,...
13 KB (1,640 words) - 07:44, 9 December 2024
specifies a password-authenticated key agreement protocol that ensures mutual authentication of two parties by using a Diffie–Hellman key exchange to...
3 KB (230 words) - 01:38, 26 April 2024
Outline of cryptography (section Key authentication)
key Wide Mouth Frog Brute force attack Dictionary attack Related key attack Key derivation function Key strengthening Password Password-authenticated...
20 KB (1,899 words) - 15:57, 22 November 2024
Forward secrecy (redirect from Key erasure)
the analogous property of password-authenticated key agreement protocols where the long-term secret is a (shared) password. In 2000 the IEEE first ratified...
25 KB (2,976 words) - 20:15, 26 October 2024
signing party Key stretching Key-agreement protocol glossary Password psychology Public key fingerprint Random number generator Session key Tripcode Machine-readable...
13 KB (1,506 words) - 19:24, 28 November 2024
CRAM-MD5 (category Email authentication)
hardware, or even just standard CPUs. Proxy-ability: Unlike a password-authenticated key agreement (PAKE) scheme, CRAM-MD5 does not establish a secret shared...
7 KB (839 words) - 21:00, 14 May 2023
one-time password. EAP with the encrypted key exchange, or EAP-EKE, is one of the few EAP methods that provide secure mutual authentication using short...
34 KB (4,172 words) - 21:59, 11 November 2024
OPRF is used in some implementations of password-authenticated key agreement. An OPRF is used in the Password Monitor functionality in Microsoft Edge...
8 KB (1,023 words) - 14:10, 31 January 2024
specified by the authenticator, and either accepted or not by the authenticated: A cryptographic hash method H (default is SHA-1) A secret key K, which is...
11 KB (1,150 words) - 23:24, 3 October 2024