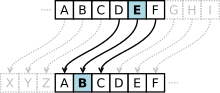
different types of substitution cipher. If the cipher operates on single letters, it is termed a simple substitution cipher; a cipher that operates on larger...
30 KB (4,021 words) - 22:15, 14 July 2024
message, so the cipher is classed as a type of monoalphabetic substitution, as opposed to polyalphabetic substitution. The Caesar cipher is named after...
19 KB (2,031 words) - 00:56, 12 August 2024
polyalphabetic cipher is a substitution, using multiple substitution alphabets. The Vigenère cipher is probably the best-known example of a polyalphabetic cipher, though...
6 KB (683 words) - 07:58, 14 March 2024
ciphers used in the past are sometimes known as classical ciphers. They include simple substitution ciphers (such as ROT13) and transposition ciphers...
17 KB (2,099 words) - 21:11, 28 July 2024
Playfair cipher or Playfair square or Wheatstone–Playfair cipher is a manual symmetric encryption technique and was the first literal digram substitution cipher...
20 KB (2,503 words) - 05:22, 27 August 2024
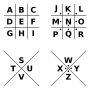
Napoleon cipher, and tic-tac-toe cipher) is a geometric simple substitution cipher, which exchanges letters for symbols which are fragments of a grid...
11 KB (1,303 words) - 15:15, 28 August 2024
between transposition and substitution operations, they are often combined, as in historical ciphers like the ADFGVX cipher or complex high-quality encryption...
25 KB (3,604 words) - 03:23, 21 March 2024
Classical ciphers are often divided into transposition ciphers and substitution ciphers, but there are also concealment ciphers. In a substitution cipher, letters...
15 KB (2,528 words) - 02:24, 15 June 2024
one of three categories of cipher used in classical cryptography along with substitution ciphers and transposition ciphers. In classical cryptography...
11 KB (1,496 words) - 22:12, 28 June 2024
The affine cipher is a type of monoalphabetic substitution cipher, where each letter in an alphabet is mapped to its numeric equivalent, encrypted using...
10 KB (1,143 words) - 22:04, 6 May 2024
than its content. Baconian ciphers are categorized as both a substitution cipher (in plain code) and a concealment cipher (using the two typefaces). To...
8 KB (773 words) - 15:51, 6 March 2024
Atbash (redirect from Atbash cipher)
Atbash (Hebrew: אתבש; also transliterated Atbaš) is a monoalphabetic substitution cipher originally used to encrypt the Hebrew alphabet. It can be modified...
7 KB (645 words) - 11:15, 24 April 2024
Hill cipher is a polygraphic substitution cipher based on linear algebra. Invented by Lester S. Hill in 1929, it was the first polygraphic cipher in which...
13 KB (2,241 words) - 19:55, 25 April 2024
Beaufort cipher, invented by some Giovanni Sestri in early 18th century but widely attributed to Sir Francis Beaufort, is a substitution cipher similar...
7 KB (861 words) - 19:28, 10 January 2024
of ciphers known as polygraphic substitution ciphers. This adds significant strength to the encryption when compared with monographic substitution ciphers...
11 KB (1,673 words) - 19:08, 29 June 2024
Ciphertext (redirect from Cipher text)
Caesar cipher and one-time pad) Polyalphabetic substitution cipher: a substitution cipher using multiple substitution alphabets (e.g., Vigenère cipher and...
9 KB (1,214 words) - 14:50, 1 September 2024
In classical cryptography, the running key cipher is a type of polyalphabetic substitution cipher in which a text, typically from a book, is used to provide...
10 KB (1,294 words) - 19:13, 30 July 2024
music ciphers that utilize homophonic substitution (one-to-many), polyphonic substitution (many-to-one), compound cipher symbols, and/or cipher keys;...
26 KB (3,585 words) - 04:04, 27 August 2024
potential to be exploited in a ciphertext-only attack. In a simple substitution cipher, each letter of the plaintext is replaced with another, and any particular...
16 KB (1,663 words) - 06:05, 8 April 2024
are used: for instance, a cipher in which pairs of letters are substituted is bigraphic. As a concept, polygraphic substitution contrasts with monoalphabetic...
4 KB (580 words) - 07:39, 19 February 2023
provide him with an important clue—he realizes that they form a substitution cipher and cracks the code by frequency analysis. The last of the messages...
16 KB (1,907 words) - 15:52, 8 August 2024
Vigenère cipher is therefore a special case of a polyalphabetic substitution. First described by Giovan Battista Bellaso in 1553, the cipher is easy to...
45 KB (5,937 words) - 02:39, 5 September 2024
Enigma machine (redirect from Enigma cipher machine)
The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication...
93 KB (11,252 words) - 08:58, 31 August 2024
Symmetric-key algorithm (redirect from Symmetric cipher)
use either stream ciphers or block ciphers. Stream ciphers encrypt the digits (typically bytes), or letters (in substitution ciphers) of a message one...
15 KB (1,544 words) - 02:53, 7 June 2024
This method was used in the second Beale cipher. This variant is more properly called a substitution cipher, specifically a homophonic one. Both methods...
15 KB (2,011 words) - 21:25, 31 August 2024
in Sweden, found the cipher to be an encrypted German text. The manuscript is a homophonic cipher that uses a complex substitution code, including symbols...
9 KB (988 words) - 21:46, 3 June 2024
Rotor machine (redirect from Rotor cipher machine)
advance positions, changing the substitution. By this means, a rotor machine produces a complex polyalphabetic substitution cipher, which changes with every...
17 KB (2,460 words) - 12:53, 17 April 2024
cryptography, an SP-network, or substitution–permutation network (SPN), is a series of linked mathematical operations used in block cipher algorithms such as AES...
7 KB (958 words) - 08:48, 28 February 2024
of ciphers known as polygraphic substitution ciphers. This adds significant strength to the encryption when compared with monographic substitution ciphers...
8 KB (1,528 words) - 04:51, 29 June 2024
cryptography, a block cipher is a deterministic algorithm that operates on fixed-length groups of bits, called blocks. Block ciphers are the elementary building...
50 KB (6,475 words) - 03:59, 22 August 2024