Web Environment Integrity (WEI) is an abandoned API proposal previously under development for Google Chrome. A Web Environment Integrity prototype existed...
8 KB (834 words) - 21:30, 28 October 2024
Ethereum blockchain Wau Ecology Institute, Wau, Papua New Guinea Web Environment Integrity, a Web API proposed by Google Windows Experience Index (WEI) score...
2 KB (294 words) - 11:19, 25 June 2024
both desktop (java/swing) and web client interfaces. It provides software development organizations with a environment in which they can manage the end-to-end...
5 KB (327 words) - 06:55, 5 September 2024
protection dongle Secure Digital Music Initiative Trusted Computing Web Environment Integrity "The pros, cons, and future of DRM". Cbc.ca. 7 August 2009. Archived...
118 KB (11,453 words) - 02:14, 4 January 2025
Semantic Web, sometimes known as Web 3.0 (not to be confused with Web3), is an extension of the World Wide Web through standards set by the World Wide Web Consortium...
52 KB (6,269 words) - 15:54, 11 October 2024
Platform Module Unified Extensible Firmware Interface § Secure Boot Web Environment Integrity Chris Mitchell (2005). Trusted Computing. IET. ISBN 978-0-86341-525-8...
42 KB (5,186 words) - 10:20, 24 November 2024
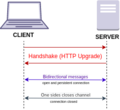
connections), which is beneficial for environments that block non-web Internet connections using a firewall. Additionally, WebSocket enables streams of messages...
49 KB (3,684 words) - 20:39, 27 December 2024
Integrity Virtual Machines is a hypervisor from Hewlett Packard Enterprise for HPE Integrity Servers running HP-UX. It is part of HP's Virtual Server Environment...
11 KB (1,087 words) - 19:02, 4 July 2024
WebKit is a browser engine primarily used in Apple's Safari web browser, as well as all web browsers on iOS and iPadOS. WebKit is also used by the PlayStation...
47 KB (3,964 words) - 14:08, 25 December 2024
Planetary boundaries (redirect from Ecological integrity)
of planetary integrity.: 142 There are many negative human impacts on the environment that are causing a reduction in planetary integrity.: 142 The idea...
101 KB (10,096 words) - 11:51, 16 December 2024
management. Security is paramount in web development to protect against cyber threats and ensure the confidentiality and integrity of user data. Best practices...
39 KB (4,682 words) - 09:53, 3 January 2025
HP-UX (section HP-UX 11i operating environments)
developed by Hewlett Packard Enterprise; current versions support HPE Integrity Servers, based on Intel's Itanium architecture. It is based on Unix System...
28 KB (2,998 words) - 20:24, 21 November 2024
Parks Canada (category Environment and Climate Change Canada)
its behalf, rather than have Environment Canada responded from a farther office. According to Panel on Ecological Integrity Report in 2000, "the idea of...
31 KB (3,148 words) - 03:58, 28 December 2024
Software. Load testing tool WebLOAD combines performance, scalability, and integrity as a single process for the verification of web and mobile applications...
6 KB (375 words) - 01:06, 27 December 2024
Mandatory Integrity Control (MIC) is a core security feature of Windows Vista and later that adds mandatory access control to running processes based...
9 KB (1,020 words) - 07:16, 26 November 2024
possible to implement support for WebAuthn purely in software, making use of a processor's trusted execution environment or a Trusted Platform Module (TPM)...
28 KB (2,861 words) - 14:31, 21 December 2024
Another possible barrier created by web mapping that may challenge web map security is data integrity and quality. Web maps rely entirely on data sources...
40 KB (4,672 words) - 14:42, 24 December 2024
Common Vulnerability Scoring System (section Integrity)
vulnerable systems in the environment. Three further metrics assess the specific security requirements for confidentiality (CR), integrity (IR) and availability...
35 KB (3,329 words) - 13:11, 21 November 2024
The Center for Public Integrity (CPI) is an American nonprofit investigative journalism organization whose stated mission is "to counter the corrosive...
80 KB (7,887 words) - 11:31, 24 December 2024
Human impact on the environment (or anthropogenic environmental impact) refers to changes to biophysical environments and to ecosystems, biodiversity...
158 KB (21,243 words) - 01:34, 21 December 2024
Information security (redirect from Confidentiality, Integrity, and Availability)
Kim, Bonn-Oh (September 21, 2000), "Referential Integrity for Database Design", High-Performance Web Databases, Auerbach Publications, pp. 427–434, doi:10...
158 KB (18,233 words) - 22:02, 12 December 2024
Application security (redirect from Web application security)
components Identification and authentification failures Software and data integrity failures Security logging and monitoring failures* Server-side request...
10 KB (1,094 words) - 17:53, 24 November 2024
Elisabeth Bik (redirect from Science Integrity Digest)
Margaretha Harbers-Bik (born 1966) is a Dutch microbiologist and scientific integrity consultant. Bik is known for her work detecting photo manipulation in...
31 KB (3,007 words) - 21:30, 31 December 2024
maintaining the integrity of a community is reflected in its influence on the growth rates of other populations.": 511 Within these categories, food webs can be...
82 KB (8,605 words) - 22:22, 30 December 2024
supporting Windows and Linux environments with features from HP-UX within the next two years. "HP Integrity Servers". Web site. Archived from the original...
15 KB (2,059 words) - 20:24, 23 July 2024
Research integrity or scientific integrity is an aspect of research ethics that deals with best practice or rules of professional practice of scientists...
53 KB (6,326 words) - 17:30, 9 August 2024
WhatsApp (redirect from WhatsApp Web)
through a web client, under the name WhatsApp Web, in late January 2015 through an announcement made by Koum on his Facebook page: "Our web client is...
213 KB (18,502 words) - 09:03, 4 January 2025
Transport Layer Security (section Data integrity)
aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of...
179 KB (17,621 words) - 02:19, 5 January 2025
In situations where multiple web servers must share knowledge of session state (as is typical in a cluster environment) session information must be shared...
14 KB (1,962 words) - 07:19, 28 September 2024
Safari is a web browser developed by Apple. It is built into several of Apple's operating systems, including macOS, iOS, iPadOS and visionOS, and uses...
132 KB (10,972 words) - 19:53, 26 December 2024