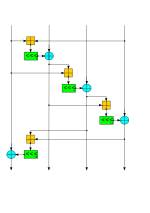
Triple DES (redirect from Triple Data Encryption Algorithm)
0E.FE, E0.1F.1F.E0.F1.0E.0E.F1, 1F.E0.E0.1F.0E.F1.F1.0E, 01.E0.1F.FE.01.F1.0E.FE, FE.1F.E0.01.FE.0E.F1.01, E0.1F.E0.1F.F1.0E.F1.0E, 1F.E0.1F.E0.0E.F1.0E...
23 KB (2,946 words) - 08:25, 17 May 2024
together. The algorithm XORs that sum with the value in the 2-bit register. The first bit of the result is output for the encoding. E0 is divided in three...
6 KB (802 words) - 03:54, 19 February 2024
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption...
15 KB (1,544 words) - 02:53, 7 June 2024
files? See media help. The μ-law algorithm (sometimes written mu-law, often approximated as u-law) is a companding algorithm, primarily used in 8-bit PCM...
10 KB (1,101 words) - 08:12, 1 May 2024
RC4 (redirect from RC4 decryption algorithm)
key-scheduling algorithm (KSA). Once this has been completed, the stream of bits is generated using the pseudo-random generation algorithm (PRGA). The key-scheduling...
44 KB (5,058 words) - 05:30, 15 April 2024
ciphertext E0. It then runs an exhaustive key search. The algorithm looks like this: E0 = oracle_query(0) for k in 0,1,...,256-1: if DESk(0) == E0: return...
6 KB (875 words) - 12:05, 9 April 2024
space–time tradeoffs. Various CRC standards extend the polynomial division algorithm by specifying an initial shift register value, a final Exclusive-Or step...
53 KB (4,876 words) - 14:36, 16 June 2024
octets. When data is sent over E0 (G.703), MSB (sign) is sent first and LSB is sent last. ITU-T STL defines the algorithm for decoding as follows (it puts...
15 KB (1,816 words) - 19:43, 11 June 2024
It has edges e0 = hv0,v1i, e1 = hv1,v2i, and e2 = hv2,v0i. The inverse connections are also known. Vertex v0 is adjacent to edges e0 and e2 and to triangle...
8 KB (1,047 words) - 20:58, 7 February 2024
Crypto1 is a proprietary encryption algorithm (stream cipher) and authentication protocol created by NXP Semiconductors for its MIFARE Classic RFID contactless...
6 KB (536 words) - 23:27, 18 November 2023
weaknesses when faced with chosen IV attacks. For instance, its key scheduling algorithm has the same secret key for different initialization vectors and this...
3 KB (328 words) - 01:12, 15 June 2024
redundancy (it expands the message without adding information) and the algorithm is based on cyclic codes. CRCs are popular because they are simple to...
72 KB (5,953 words) - 12:06, 4 May 2024
size, called the block size. For example, a single invocation of the AES algorithm transforms a 128-bit plaintext block into a ciphertext block of 128 bits...
14 KB (1,779 words) - 08:47, 29 April 2024
project, receiving the highest weighted voting score of any Profile 1 algorithm at the end of Phase 2. Salsa20 had previously been selected as a Phase...
31 KB (3,563 words) - 22:55, 6 July 2024
Bernoulli number (redirect from Akiyama-Tanigawa algorithm)
second fractional Euler numbers OEIS: A198631 (n) / OEIS: A006519 (n + 1): E0 = 1 E1 = 1 − 1/2 E2 = 1 − 3/2 + 2/4 E3 = 1 − 7/2 + 12/4 − 6/8 E4 = 1 − 15/2...
92 KB (12,957 words) - 20:07, 8 July 2024
of algorithms that carry out the encryption and the reversing decryption. The detailed operation of a cipher is controlled both by the algorithm and...
98 KB (10,726 words) - 01:02, 9 July 2024
abort: do anything Assigns values to variables. v := E or v0, v1, ..., vn := E0, E1, ..., En where v are program variables E are expressions of the same data...
11 KB (1,438 words) - 21:46, 7 July 2024
ChaCha20-Poly1305 is an authenticated encryption with additional data (AEAD) algorithm, that combines the ChaCha20 stream cipher with the Poly1305 message authentication...
14 KB (1,461 words) - 04:22, 9 June 2024
was enabled for code signing and that still used the weak MD5 hashing algorithm, then produced a counterfeit copy of the certificate that they used to...
33 KB (2,725 words) - 20:15, 31 May 2024
ORYX (redirect from ORYX (encryption algorithm))
ORYX is an encryption algorithm used in cellular communications in order to protect data traffic. It is a stream cipher designed to have a very strong...
3 KB (345 words) - 03:14, 17 October 2023
MD2 (hash function) (redirect from Message Digest Algorithm 2)
The MD2 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1989. The algorithm is optimized for 8-bit computers. MD2...
9 KB (1,051 words) - 18:55, 14 April 2024
v t e Stream ciphers Widely used ciphers A5/1 A5/2 ChaCha Crypto-1 E0 RC4 eSTREAM Portfolio Other ciphers Achterbahn F-FCSR FISH ISAAC KCipher-2 MUGI ORYX...
2 KB (209 words) - 14:37, 9 April 2024
In cryptography, SEAL (Software-Optimized Encryption Algorithm) is a stream cipher optimised for machines with a 32-bit word size and plenty of RAM with...
1 KB (140 words) - 01:11, 14 November 2023
In cryptography, Yamb is a stream cypher algorithm developed by LAN Crypto. It has been submitted to the eSTREAM Project of the eCRYPT network. Archived...
454 bytes (34 words) - 02:06, 26 September 2022
the container format that contains the image data encoded with the JPEG algorithm. The base specifications for a JPEG container format are defined in Annex...
15 KB (1,523 words) - 08:40, 31 March 2024
cryptography, MULTI-S01 (pronounced multi-ess-zero-one), is an encryption algorithm based on a pseudorandom number generator (PRNG). MULTI-S01 is an encryption...
3 KB (341 words) - 15:28, 20 August 2022
Signed graph (section Algorithmic problems)
matroid L0(G) has for its ground set the set E0 the union of edge set E with an extra point, which we denote e0. The lift matroid L(G) is the extended lift...
25 KB (3,395 words) - 01:12, 30 May 2024
hexadecimal values DE, DF, E0, and E1 can all be either lead units or trail units, then a search for the two-unit sequence DF E0 can yield a false positive...
10 KB (1,550 words) - 18:09, 28 January 2024
Stream cipher (redirect from Combiner-type algorithm)
Security Agency documents sometimes use the term combiner-type algorithms, referring to algorithms that use some function to combine a pseudorandom number generator...
23 KB (2,217 words) - 13:45, 7 May 2024
the E0 signal rate is designed so that each higher level can multiplex a set of lower level signals. Framed E1 is designed to carry 30 or 31 E0 data...
6 KB (750 words) - 15:52, 25 April 2024