Look up nonce in Wiktionary, the free dictionary. Nonce may refer to: Cryptographic nonce, a number or bit string used only once, in security engineering...
655 bytes (114 words) - 02:49, 10 February 2024
In cryptography, a nonce is an arbitrary number that can be used just once in a cryptographic communication. It is often a random or pseudo-random number...
7 KB (906 words) - 17:31, 29 July 2024
In linguistics, a nonce word—also called an occasionalism—is any word (lexeme), or any sequence of sounds or letters, created for a single occasion or...
11 KB (1,280 words) - 23:29, 8 August 2024
The Nonce was a hip-hop duo from Los Angeles, California, that was active in the 1990s, releasing material from 1992 to 1999. As part of the Project Blowed...
6 KB (603 words) - 14:45, 25 August 2024
"Prince Andrew Is a Sweaty Nonce" is a 2022 punk rock single by The Kunts, a band created by the dark comedy singer Kunt and the Gang. The song is directed...
13 KB (1,298 words) - 14:18, 20 July 2024
variant of the original ChaCha20 algorithm (using 32-bit counter and 96-bit nonce) and a variant of the original Poly1305 (authenticating 2 strings) being...
13 KB (1,511 words) - 14:10, 12 October 2024
Jabberwocky (redirect from Wabe (nonce word))
playing this file? See media help. Many of the words in the poem are playful nonce words of Carroll's own invention, without intended explicit meaning. When...
52 KB (5,454 words) - 02:10, 12 June 2024
authentication is an application of cryptographic hashing with usage of nonce values to prevent replay attacks. It uses the HTTP protocol. DIGEST-MD5...
24 KB (2,850 words) - 04:01, 30 September 2024
Salsa20 (section XSalsa20 with 192-bit nonce)
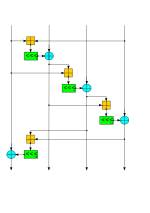
and rotation operations. The core function maps a 256-bit key, a 64-bit nonce, and a 64-bit counter to a 512-bit block of the key stream (a Salsa version...
31 KB (3,574 words) - 01:57, 24 July 2024
In case of a non-random nonce (such as a packet counter), the nonce and counter should be concatenated (e.g., storing the nonce in the upper 64 bits and...
52 KB (5,878 words) - 15:11, 20 September 2024
Classical order (redirect from Nonce order)
been used again. They are termed "nonce orders" by analogy to nonce words; several examples follow below. These nonce orders all express the "speaking...
28 KB (3,374 words) - 04:03, 28 July 2024
Pompatus (or Pompitus) (/ˈpɒmpətəs/) is a nonce word coined by Steve Miller in his hit single "The Joker" (1973). The word is probably a corruption of—or...
5 KB (695 words) - 15:59, 24 August 2024
and a randomly generated client nonce c-nonce. server-first The server appends to this client nonce its own nonce s-nonce, and adds it to the server-first...
15 KB (1,891 words) - 08:47, 14 October 2024
date after the subject certificate may have been revoked. OCSP allows a nonce to be included in the request that may be included in the corresponding...
18 KB (1,796 words) - 23:34, 6 October 2024
Architecture parlante (section Nonce orders)
but have not been used again. Thus, they may be termed "nonce orders" on the analogy of nonce words. In 1762, James Adam invented a British order featuring...
7 KB (948 words) - 02:37, 19 July 2024
formation, in fact, identify the process of a "neological continuum": a nonce word is any single-use term that may or may not grow in popularity; a protologism...
24 KB (2,794 words) - 22:43, 2 October 2024
cryptographic nonce. The construction is defined in RFC 8452. AES-GCM-SIV is designed to preserve both privacy and integrity even if nonces are repeated...
4 KB (397 words) - 18:19, 16 September 2024
time-based nonces, as these can weaken servers in different time zones and servers with inaccurate clocks. It can also be important to use time-based nonces and...
11 KB (1,540 words) - 06:34, 22 September 2024
challenges Alice by sending a nonce N. B → A: N Alice responds by sending back the MAC calculated on her identifier and the nonce using the shared key Kab...
3 KB (364 words) - 08:16, 8 September 2024
related signature algorithms DSA, ECDSA, and ElGamal, reusing the secret nonce value k {\displaystyle k} on two Schnorr signatures of different messages...
8 KB (1,204 words) - 18:16, 2 October 2024
{\displaystyle S} N A {\displaystyle N_{A}} and N B {\displaystyle N_{B}} are nonces generated by A {\displaystyle A} and B {\displaystyle B} respectively K...
13 KB (2,192 words) - 08:04, 20 March 2024
boy". Academic. "nancy". Macmillan Dictionary. "NONCE | English meaning - Cambridge Dictionary". "NONCE definition and meaning | Collins English Dictionary"...
133 KB (15,611 words) - 18:11, 30 September 2024
randomness is derived internally. In this case, the IV is commonly called a nonce (a number used only once), and the primitives (e.g. CBC) are considered...
14 KB (1,797 words) - 08:53, 7 September 2024
a major author, the longest word ever to appear in literature Contrived nonce word; not in dictionary; Ancient Greek transliteration...
36 KB (3,233 words) - 04:46, 12 October 2024
random number generator. Salt (cryptography) Pseudorandomness Cryptographic nonce Initialization vector /dev/random Web's random numbers are too weak, researchers...
2 KB (245 words) - 17:34, 23 September 2024
Cryptographic primitive Cryptanalysis Cryptocurrency Cryptosystem Cryptographic nonce Cryptovirology Hash function Cryptographic hash function Key derivation...
221 KB (19,930 words) - 21:27, 11 October 2024
contents somehow depend on the web application's state—such as usage of the nonce origin. Otherwise, the CSP is rather static and can be delivered from web...
18 KB (1,779 words) - 21:23, 27 September 2024
The attack was made possible because Sony failed to generate a new random nonce for each signature. An analysis comparing millions of RSA public keys gathered...
21 KB (2,632 words) - 01:52, 7 October 2024
Cryptographic primitive Cryptanalysis Cryptocurrency Cryptosystem Cryptographic nonce Cryptovirology Hash function Cryptographic hash function Key derivation...
49 KB (5,566 words) - 05:30, 28 September 2024
Cryptographic primitive Cryptanalysis Cryptocurrency Cryptosystem Cryptographic nonce Cryptovirology Hash function Cryptographic hash function Key derivation...
34 KB (4,071 words) - 15:13, 29 September 2024